本节介绍了 NSX Advanced Load Balancer 上的 ICAP 的各种日志和故障排除选项。可以使用 NSX Advanced Load Balancer UI 和 CLI 检查日志和错误消息以进行分析和故障排除。
ICAP 服务器处理的请求日志填充了 icap_log 部分。
如果 ICAP 服务器阻止或修改请求,则生成的日志条目是重要日志。以下示例显示了
NSX Advanced Load Balancer 上的可用日志的详细信息。正如“响应信息”中所示,阻止了整个请求,并将 403 响应代码发回到客户端。
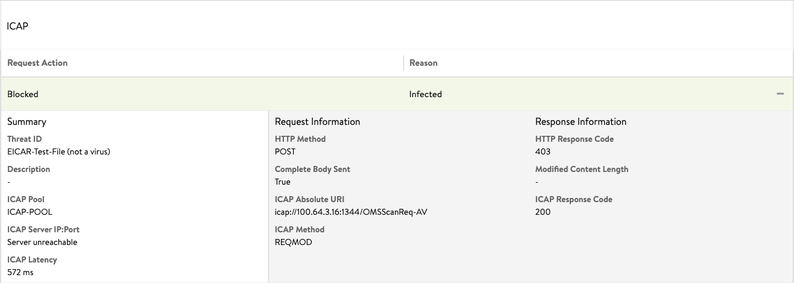

以下日志显示 ICAP 扫描检测到感染(JSON 日志文件):
"icap_log": { "action": "ICAP_BLOCKED", "request_logs": [ { "icap_response_code": 200, "icap_method": "ICAP_METHOD_REQMOD", "http_response_code": 403, "http_method": "HTTP_METHOD_POST", "icap_absolute_uri": "icap://100.64.3.15:1344/OMSScanReq-AV ", "complete_body_sent": true, "pool_name": { "val": "ICAP-POOL-GROUP", "crc32": 1799851903 }, "pool_uuid": "poolgroup-c7dd3b93-60c1-4190-b6d6-26c22d55dc30", "latency": "1275", "icap_headers_sent_to_server": "Host: 100.64.3.15:1344\r\nConnection: close\r\nPreview: 653\r\nAllow: 204\r\nEncapsulated: req-hdr=0, req-body=661\r\n", "icap_headers_received_from_server": "Date: Thu, 19 Nov 2020 13:55:00 G11T\r\nServer: Metadefender Core V4\r\nISTag: \"001605794100\"\r\nX-ICAP-Profile: File process\r\nX-Response-Info: Blocked\r\nX-Response-Desc: Infected\r\nX-Blocked-Reason: Infected\r\nX-Infection-Found: Type=0", "action": "ICAP_BLOCKED", "reason": "Infected", "threat_id": "EICAR-Test-File (not a virus)" }] },以下是 ICAP 服务器修改 ICAP 请求时生成的日志条目:
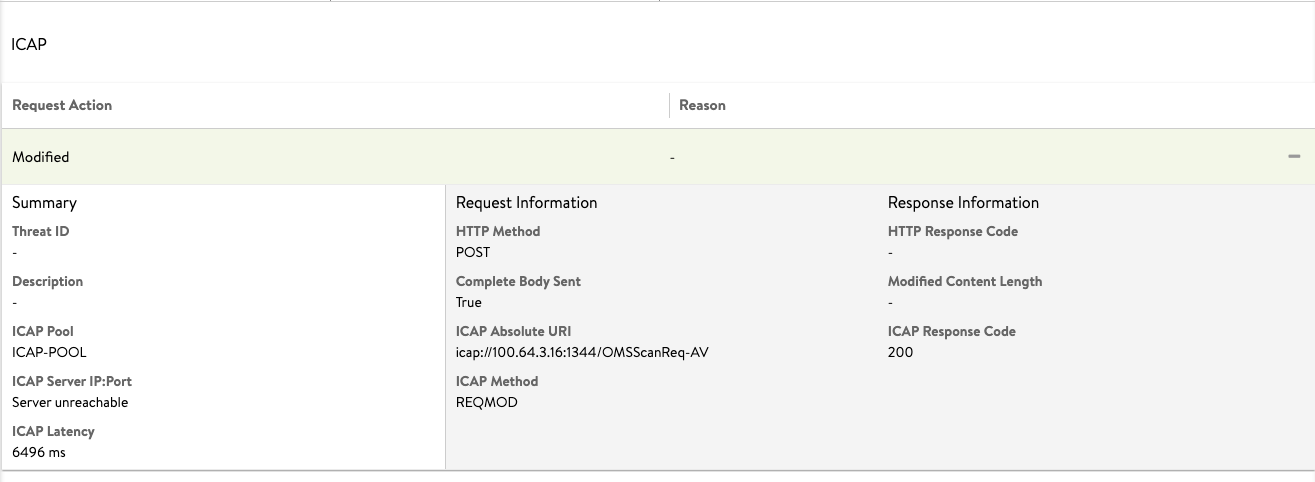
以下日志显示已成功执行 ICAP 扫描。icap_log 的操作字段显示值为
ICAP_PASSED。{"icap_log": {"action": "ICAP_PASSED", "request_logs": [{ "icap_response_code": 204, "icap_method": "ICAP_METHOD_REQMOD", "http_method": "HTTP_METHOD_POST", "icap_absolute_uri": "icap://100.64.3.15:1344/OMSScanReq-AV ", "complete_body_sent": true, "pool_name": {"val": "ICAP-POOL-GROUP", "crc32": 1799851903}, "pool_uuid": "poolgroup-c7dd3b93-60c1-4190-b6d6-26c22d55dc30", "latency": "456", "icap_headers_sent_to_server": "Host: 100.64.3.15:1344\r\nConnection: close\r\nPreview: 0\r\nAllow: 204\r\nEncapsulated: req-hdr=0, null-body=661\r\n", "icap_headers_received_from_server": "Date: Wed, 18 Nov 2020 12:54:06 G11T\r\nServer: Metadefender Core V4\r\nISTag: \"000000000096\"\r\nX-Response-Info: Allowed\r\nEncapsulated: null-body=0\r\n", "action": "ICAP_PASSED"}]}如果未启用 ICAP 功能,日志条目将 icap_log 操作显示为
ICAP_DISABLED。"icap_log": {"action": "ICAP_DISABLED"}
日志分析
如果启用了 ICAP,NSX Advanced Load Balancer 上的日志分析将提供额外的概览信息。可以单击所有数据项,并允许快速添加筛选器以获取详细的日志视图。
故障排除
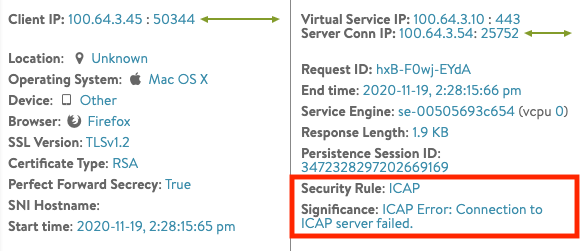
ICAP 服务器连接失败:以下示例显示失败的 ICAP 服务器连接的日志错误消息。将在
重要性字段中记录
ICAP 错误。要解决该问题,请检查从 SE 到 ICAP 服务器的直接连接。

ICAP 服务器错误:以下示例显示阻止了 ICAP 请求。由于未正确配置 ICAP 服务器,ICAP log 操作显示为 ICAP_BLOCKED。该操作的原因是 No security rule matched,即,在 ICAP 标头中没有匹配的规则。
"icap_log":
{"action": "ICAP_BLOCKED",
"request_logs":
[{
"icap_response_code": 200,
"icap_method": "ICAP_METHOD_REQMOD",
"http_response_code": 403,
"http_method": "HTTP_METHOD_POST",
"icap_absolute_uri": "icap://100.64.3.15:1344/OMSScanReq-AV ",
"complete_body_sent": true, "pool_name": {"val": "ICAP-POOL-GROUP", "crc32": 1799851903}, "pool_uuid": "poolgroup-c7dd3b93-60c1-4190-b6d6-26c22d55dc30", "latency": "17",
"icap_headers_sent_to_server": "Host: 100.64.3.15:1344\r\nConnection: close\r\nPreview: 0\r\nAllow: 204\r\nEncapsulated: req-hdr=0, null-body=661\r\n",
"icap_headers_received_from_server": "Date: Thu, 19 Nov 2020 13:25:15 G11T\r\nServer: Metadefender Core V4\r\nISTag: \"001605792300\"\r\nX-Response-Info: Blocked\r\nX-Response-Desc: No security rule matched\r\nEncapsulated: res-hdr=0, res-body=91\r\n", "action": "ICAP_BLOCKED"}]}
要解决该问题,请参见“用于部署的 ICAP 服务器”。