授权是控制向用户提供的访问的过程。通过使用授权策略,您可以指示是否允许经过身份验证的用户访问资源。例如,在受保护资源(如 saml.acme.com)上,您可以限制用户访问权限以使用 same.acme.com/admin 页面。本节介绍了如何配置授权策略以及相应的规则和操作。
SAML 授权策略
下图表示 SAML 授权流程:
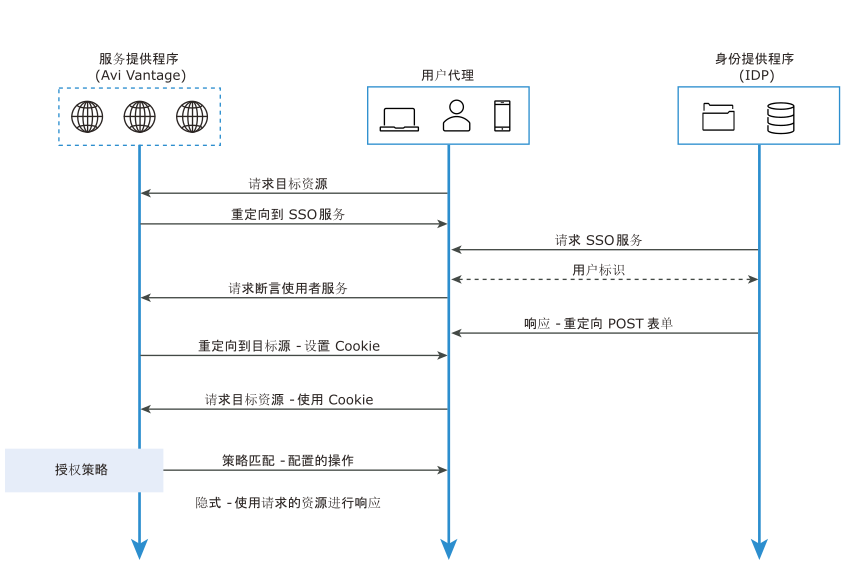
SAML 授权规则
SAML 授权支持以下匹配类型:
匹配类型 |
描述 |
属性 |
来自 IdP 的 SAML 响应包含的属性 |
路径 |
URI 路径 |
主机标头 |
在入站请求中包含的主机标头 |
方法 |
HTTP 请求方法,例如 GET、POST。 |
可以将主机标头和路径配置为区分大小写。
SAML 授权支持以下操作类型:
操作类型 |
描述 |
allow_access |
在授权策略规则匹配时允许访问 |
close_connection |
在授权策略规则匹配时关闭连接 |
http_local_response |
在授权策略规则匹配时发送 HTTP 本地响应 |
必须仅允许具有电子邮件的用户(属性为 [email protected])使用 aviadmin 路径。
仅允许 GET 请求使用该路径。
仅允许具有主机标头 admin.acme.com 的请求访问该路径。
如果满足上述条件,才能允许进行访问。否则,必须向用户返回 403 响应代码。
授权策略配置如下所示:
+------------------------------+----------------------------------------+ | Field | Value +------------------------------+----------------------------------------+ | uuid | ssopolicy-86fb0825-8d1f-45f4-a56b-f8bf8adf9a46 | | name | sso1 | authentication_policy | | default_auth_profile_ref | saml-idp-authz | authorization_policy | | authz_rules[1] | | name | Demo_rule | index | 1 | enable | True | match | | attr_matches[1] | | attribute_name | email | attribute_value_list | | match_criteria | EQUALS | match_str[1] | [email protected] | path | | match_criteria | EQUALS | match_case | INSENSITIVE | match_str[1] | /aviadmin | host_hdr | | match_criteria | HDR_EQUALS | match_case | INSENSITIVE | value[1] | admin.acme.com | method | | match_criteria | IS_IN | methods[1] | HTTP_METHOD_GET | action | | type | ALLOW_ACCESS | status_code | HTTP_RESPONSE_STATUS_CODE_403 | authz_rules[2] | | name | Deny_rule | index | 2 | enable | True | match | | path | | match_criteria | EQUALS | match_case | INSENSITIVE | match_str[1] | /aviadmin | action | | type | HTTP_LOCAL_RESPONSE | status_code | HTTP_RESPONSE_STATUS_CODE_403 | type | SSO_TYPE_SAML | tenant_ref | admin +------------------------------+----------------------------------------+
此处,只有在满足所有条件时,才会显示规则名称 Demo_rule,并为其提供访问。
如果在 Demo_rule 中不满足任何条件,将显示 Deny_rule,但拒绝访问。您需要在规则(此处为 Deny_rule)中明确定义操作,否则,将默认允许该操作。
如果在单个规则中具有多个条件,则为 AND 匹配。如果具有多个规则,则为 OR 匹配。也就是说,如果配置了多个规则,并且其中的一个规则匹配,则执行该操作。规则检查顺序取决于规则的索引。
status_code 字段的默认值为
HTTP_RESPONSE_STATUS_CODE_403,只有在操作是本地响应时,才会采用该状态代码。对于其他操作(例如,关闭连接或允许访问),将忽略该状态代码。
使用相应的规则和操作配置授权策略
本节通过示例解释了不同种类的匹配。您可以根据用例或要求选择一个或多个条件。
以下是配置 SAML 授权策略的步骤:
将授权配置文件附加到包含 IdP 元数据的身份验证策略。例如,配置的授权配置文件为 saml-idp-authz。
[admin:controller]: > configure ssopolicy ssopolicy1 [admin:controller]: ssopolicy> authentication_policy default_auth_profile_ref saml-idp-authz [admin:controller]: ssopolicy:authentication_policy> save
导航到授权策略模式。
[admin: controller]: ssopolicy> authorization_policy
在授权策略中配置多个按索引排序的授权规则。以下是名为 rule1 的授权规则的配置示例。
[admin:controller]: ssopolicy:authorization_policy> authz_rules name rule1 New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules>
为授权策略选择匹配条件,如上面的匹配表中所述。在以下示例中,attr_matches 属性用作匹配条件。
[admin:controller]: ssopolicy:authorization_policy:authz_rules> match [admin:controller]: ssopolicy:authorization_policy:authz_rules:match> attr_matches New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_name Attribute name whose values will be looked up in the access lists. attribute_value_list (submode)
SAML 断言响应中的属性或值通过属性匹配与配置的属性及其值进行匹配。每个 SAML 断言属性可能具有零个或更多关联的值。您可以将多个属性和值配置为每个规则的一部分。只有在所有属性都匹配时,才与规则匹配。匹配可能是肯定匹配或否定匹配。
肯定匹配:BEGINS_WITH、CONTAINS、ENDS_WITH、EQUALS、REGEX_MATCH
否定匹配:DOES_NOT_BEGIN_WITH、DOES_NOT_CONTAIN、DOES_NOT_END_WITH、DOES_NOT_EQUAL、REGEX_DOES_NOT_MATCH 如果属性在断言响应中存在,并且相应属性的值之一与配置的值列表匹配,则与肯定属性匹配规则匹配。如果属性不存在,或者相应属性的所有值都与配置的值列表不匹配,则与否定属性匹配规则匹配。
在同一规则中搜索多个属性,并在单个规则中配置多个属性匹配,如下所示:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> attr_matches New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_name firstname [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_value_list match_criteria equals match_str abc [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match>
根据以上详细信息,配置如下所示:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> where Tenant: admin Cloud: Default-Cloud +------------------------+-------------+ | Field | Value | +------------------------+-------------+ | attr_matches[1] | | | attribute_name | email | | attribute_value_list | | | match_criteria | BEGINS_WITH | | match_str[1] | [email protected] | | attr_matches[2] | | | attribute_name | firstname | | attribute_value_list | | | match_criteria | EQUALS | | match_str[1] | abc | +------------------------+-------------+
在同一规则中添加更多要匹配的条件。例如,您可以添加另一个条件以匹配主机标头。
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> host_hdr [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_ hdr_begins_with header value begins with the configure value(s) hdr_contains header value contains configured value(s) hdr_does_not_begin_with header value does not begins with the configure value(s) hdr_does_not_contain header value does not contains configured value(s) hdr_does_not_end_with header value does not ends with the configured value(s) hdr_does_not_equal header value does not equals the configured value(s) hdr_does_not_exist header does not exist in the HTTP request hdr_ends_with header value ends with the configured value(s) hdr_equals header value equals the configured value(s) hdr_exists header exists in the HTTP request [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> value abc.xyz.com [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match>
如果需要,根据 HTTP 方法添加另一个条件,如下所示:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> host_hdr [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_ hdr_begins_with header value begins with the configure value(s) hdr_contains header value contains configured value(s) hdr_does_not_begin_with header value does not begins with the configure value(s) hdr_does_not_contain header value does not contains configured value(s) hdr_does_not_end_with header value does not ends with the configured value(s) hdr_does_not_equal header value does not equals the configured value(s) hdr_does_not_exist header does not exist in the HTTP request hdr_ends_with header value ends with the configured value(s) hdr_equals header value equals the configured value(s) hdr_exists header exists in the HTTP request [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> value abc.xyz.com [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match>
根据路径的字符串组或字符串值列表匹配路径匹配。这区分大小写,并支持以下匹配操作列表:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> path [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> match_criteria begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> string_group_refs System-Cacheable-Resource-Types [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> match_str /acme [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match> save [admin:controller]: ssopolicy:authorization_policy:authz_rules>
您可以配置上表中提到的任何操作。在以下示例中,您可以使用 HTTP 状态代码(例如 http_local_response)向用户发送 403 响应。
[admin:controller]: ssopolicy:authorization_policy:authz_rules> action [admin:controller]: ssopolicy:authorization_policy:authz_rules:action> status_code HTTP status code to use for local response when a policy rule is matched. type Defines the action taken when an authorization policy rule is matched.By default, access is allowed to the requested resource. watch Watch a given show command where Display the in-progress object [admin:controller]: ssopolicy:authorization_policy:authz_rules:action> type http_local_response [admin:controller]: ssopolicy:authorization_policy:authz_rules:action> status_code http_response_status_code_403 [admin:controller]: ssopolicy:authorization_policy:authz_rules:action> save [admin:controller]: ssopolicy:authorization_policy:authz_rules> index 1 [admin:controller]: ssopolicy:authorization_policy:authz_rules> save [admin:controller]: ssopolicy:authorization_policy> save [admin:controller]: ssopolicy> save
以下是基于上述配置步骤的 SSO 策略配置:
+------------------------------+----------------------------------------+ | Field | Value +------------------------------+----------------------------------------+ | uuid | ssopolicy-16fc1b04-f635-439b-97a4-a3890dead864 | | name | ssopolicy1 | authentication_policy | | default_auth_profile_ref | saml-idp-authz | authorization_policy | | authz_rules[1] | | name | rule1 | index | 1 | enable | True | match | | attr_matches[1] | | attribute_name | email | attribute_value_list | | match_criteria | BEGINS_WITH | match_str[1] | [email protected] | attr_matches[2] | | attribute_name | firstname | attribute_value_list | | match_criteria | EQUALS | match_str[1] | abc | path | | match_criteria | BEGINS_WITH | match_case | INSENSITIVE | match_str[1] | /acme | string_group_refs[1] | System-Cacheable-Resource-Types | host_hdr | | match_criteria | HDR_BEGINS_WITH | match_case | INSENSITIVE | value[1] | abc.xyz.com | method | | match_criteria | IS_IN | methods[1] | HTTP_METHOD_GET | action | | type | HTTP_LOCAL_RESPONSE | status_code | HTTP_RESPONSE_STATUS_CODE_403 | type | SSO_TYPE_SAML | tenant_ref | admin +------------------------------+----------------------------------------+