If the change-detected icon  appears next to a Ready to Publish, No Recommendations Available, or Failed status, review the changes in the original scope of the Security Intelligence recommendation input entities. Rerun the recommendation analysis, if needed.
appears next to a Ready to Publish, No Recommendations Available, or Failed status, review the changes in the original scope of the Security Intelligence recommendation input entities. Rerun the recommendation analysis, if needed.
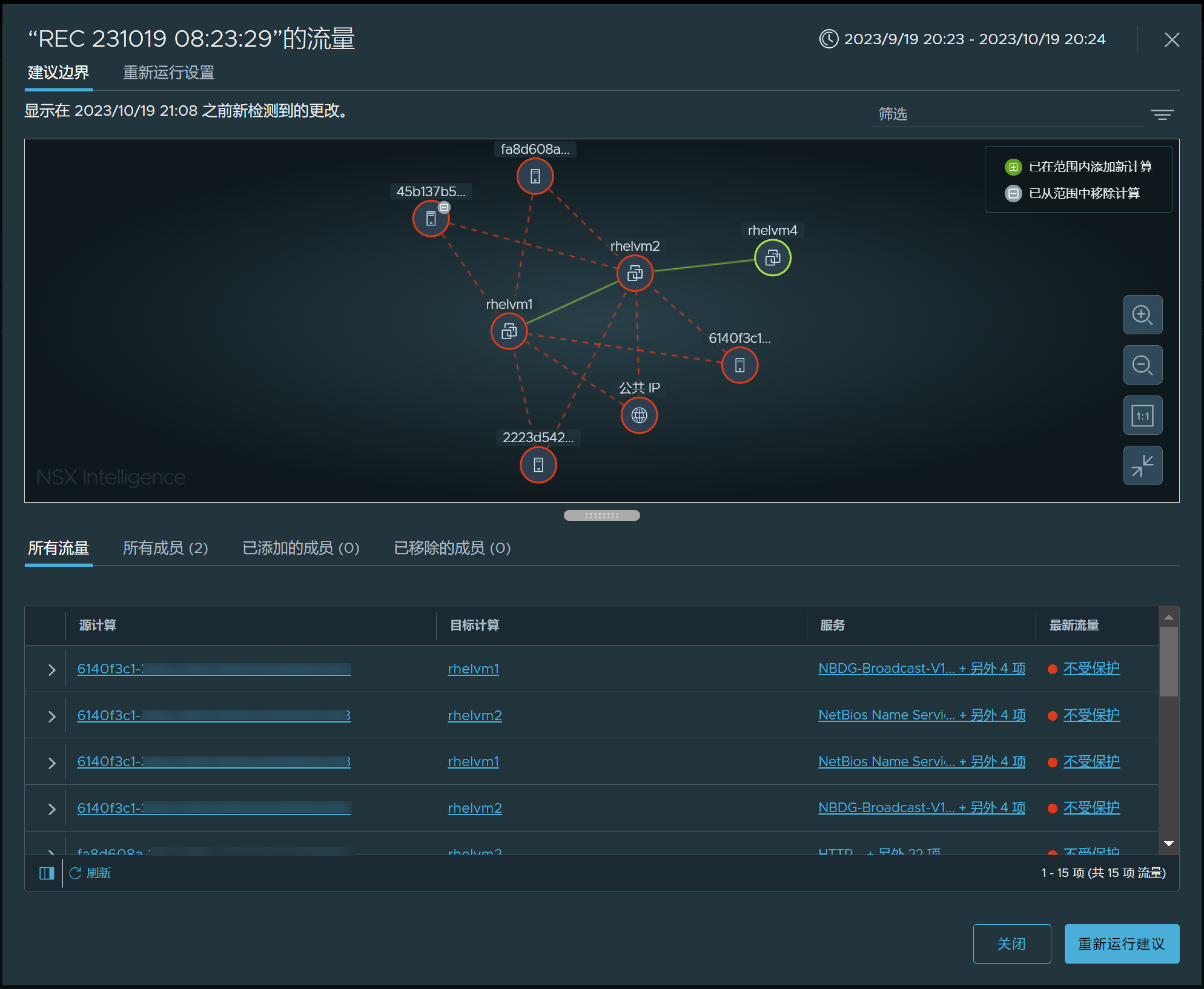
The change-detected icon  indicates that some change occurred with the input entities that were used to generate the previous Security Intelligence recommendation. If at least one of the following occurs, the change-detected icon appears in the Recommendations table, next to the affected recommendation.
indicates that some change occurred with the input entities that were used to generate the previous Security Intelligence recommendation. If at least one of the following occurs, the change-detected icon appears in the Recommendations table, next to the affected recommendation.
New effective members are added or removed from the originally selected entities that were used to generate the Security Intelligence recommendation.
The "applied to the scope" of the security policy changed from the value that was used at the start of the Security Intelligence recommendation analysis.
The permissive mode changed for an existing section that was reused to generate the Security Intelligence recommendation.
The status changed for a compute entity that was used to generate the Security Intelligence recommendation even if it is not part of the selected entities in the scope boundary. This compute entity is included in the original rule recommendation analysis because it communicated with one of the originally selected compute entities in the scope boundary.
前提条件
You must have previously generated an Security Intelligence recommendation. See Generate a New Security Intelligence Recommendation.
Ensure you have the required privileges to rerun the Security Intelligence recommendations. See Security Intelligence 中的基于角色的访问控制 for more information.
过程
结果
After you select Rerun Recommendation, the previously generated recommendation is deleted and cannot be restored. The Security Intelligence recommendation service regenerates the DFW rule recommendation using the modified input entities as the recommendation boundary. Newly detected flows and compute entities for the selected time period are also included in the recommendation analysis. Traffic flows for compute entities that were deleted from the original input entities are not considered in the analysis.
下一步做什么
After the new recommendation has the Ready to Publish status, review the recommendation using the information in Review and Publish Generated Security Intelligence Recommendations.
 on the leftmost side of the recommendation's row and select
on the leftmost side of the recommendation's row and select