You can configure automated compliance remediation by applying host security configuration rules and setting options to enforce hardening rules.
Prerequisites
Install or upgrade to Management Pack for vRealize Orchestrator version 3.1.
Procedure
- Add the Apply Host Security Configuration Rules out of the box workflow to the vRealize Orchestrator server. For more information, see Import Workflow.
- Log in to vRealize Orchestrator to enforce the hardening rules in vRealize Orchestrator.
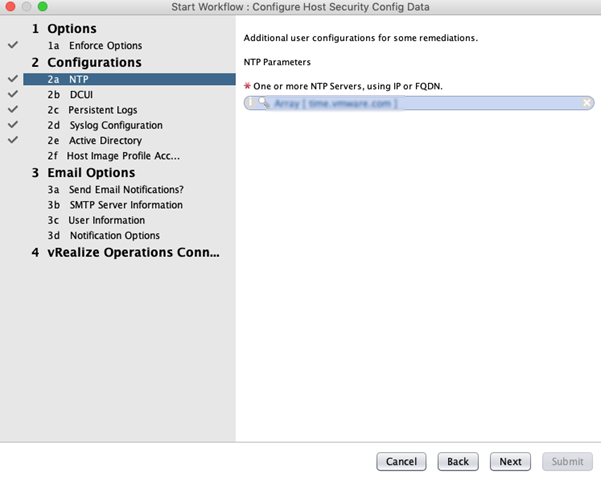
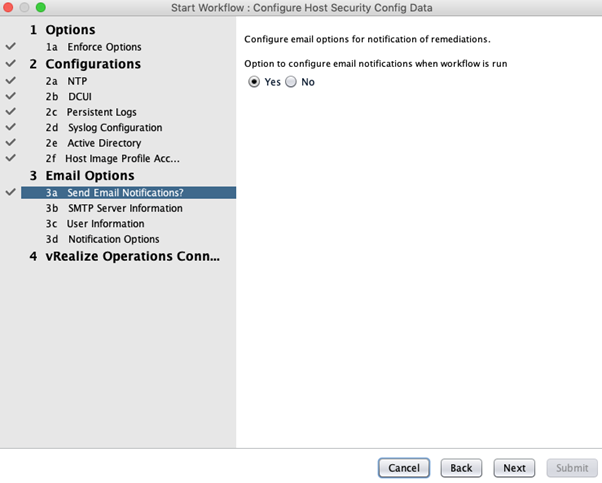
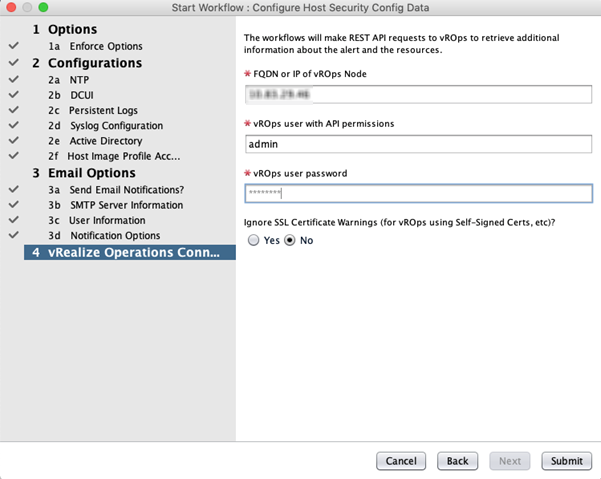
- Run the Configure Host Security Config Data workflow to configure the Host Security Hardening Configuration and Email Config attributes.
- In the Enforce Options, you can choose to selectively enforce rules by configuring the configuration elements.
- Under Configurations, set the NTP values.
- Under Email Options, configure Send Email Notifications?
- Under vRealize Operations Connections, configure the connection and login credentials.
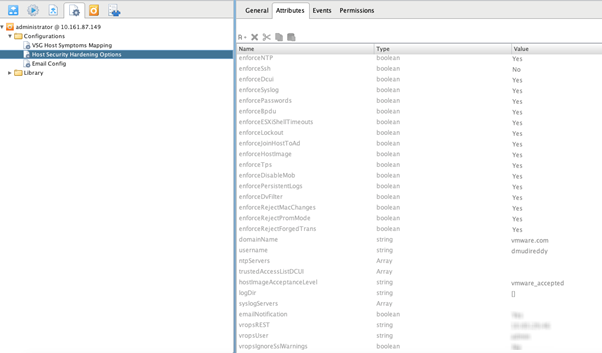
After executing the workflow, both the
Host Security Hardening Options and
Email Config configurational elements are filled with attribute values that are enforced.
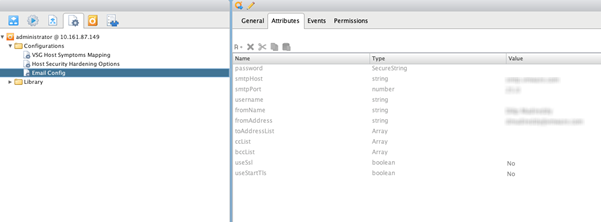
- After setting the options to enforce hardening rules, enforce them automatically through auto remediation feature of Management Pack for vRealize Orchestrator
- Go to .
- Edit the policy currently active.
- Select the Symptom Definitions tab on the left, and search for the alert, ESXi Host is violating VMware vSphere Security Configuration Guide for vCenter version 6.5 or 6.7 on the panel that appears on the right.
- Select the alert and in the Automate column, change the value to local.
- Select the Apply Policy to Groups tab on the left and and select the checkbox against vRealize Orchestrator Adapter Managed Objects in the panel that appears on the right.
Results
When any new ESXi Host is violating VMware vSphere Security Configuration Guide for vCenter version 6.5 or 6.7 alert is triggered, Management Pack for vRealize Orchestrator will automatically invoke the action mapped to it. If there is an existing alert, you can manually run the action against that alert. For any new alerts, the action automatically gets triggered in the next collection cycle. The recipient you configured earlier will receive an email after the action is successfully executed.