This topic gives you an overview of how to prepare for using Transport Layer Security (TLS) with Redis for VMware Tanzu Application Service to secure communication between apps and service instances.
CautionThis procedure involves restarting all of the VMs in your deployment to apply a CA certificate. The operation can take a long time to complete.
When you use TLS, a new port is co-located with Redis for Tanzu Application Service service instances. Apps and clients can use this secure port to establish encrypted connections with the service.
Using BOSH CredHub, Tanzu Operations Manager generates a server certificate using a Certificate Authority (CA) certificate.
If you do not want to use the CA certificate generated, you can provide your own CA certificate and add it through the CredHub CLI. For an overview of the purpose and capabilities of the CredHub component, see CredHub.
Apps and clients use this CA certificate to verify that the server certificate is trustworthy. A trustworthy server certificate allows apps and clients to securely communicate with the Redis for Tanzu Application Service server.
VMware Tanzu Application Service for VMs (TAS for VMs) shares the CA certificate public component:
- TAS for VMs provisions a copy of the CA certificate in the trusted store of each container’s operating system. Apps written in Java and Spring, or C# and Steeltoe, automatically discover the CA certificate in the trusted store. Apps not written in Java and Spring, or C# and Steeltoe, can retrieve the public component of the CA certificate from
VCAP_SERVICESand use it to establish an encrypted connection with the data service.
Generated or Provided CA Certificate
Tanzu Operations Manager can generate a CA certificate for TLS to use.
Alternatively, you can choose to provide your own CA certificate for TLS to use.
Workflow
The workflow you follow to prepare for TLS depends on whether you use the CA certificate generated by Tanzu Operations Manager or if you bring your own CA certificate.
Using the Generated CA Certificate
To use the CA certificate that Tanzu Operations Manager generates through CredHub, follow this workflow to enable TLS for Redis for VMware Tanzu Application Service:
-
An operator adds the CredHub-generated certificate to Tanzu Operations Manager by performing the procedures:
-
An operator enables TLS in the tile configuration while installing Redis for Tanzu Application Service. See Enable TLS in Redis for Tanzu Application Service.
- An app developer edits their app to communicate securely with the Redis for Tanzu Application Service server. See Using TLS.
Providing Your Own CA Certificate
To provide your own CA certificate instead of using the one that Tanzu Operations Manager generates, follow this workflow to enable TLS for Redis for VMware Tanzu Application Service:
-
An operator provides a CA certificate to CredHub by performing the procedures:
-
An operator enables TLS in the tile configuration while installing Redis for Tanzu Application Service. See Enable TLS in Redis for Tanzu Application Service.
- An app developer edits their app to communicate securely with the Redis for Tanzu Application Service server. See Using TLS.
Find the CredHub Credentials in Tanzu Operations Manager
To find the BOSH CredHub client name and client secret:
- In the Tanzu Operations Manager Installation Dashboard, click the BOSH Director tile.
- Click the Credentials tab.
- In the BOSH Director section, click the link to the BOSH Commandline Credentials.
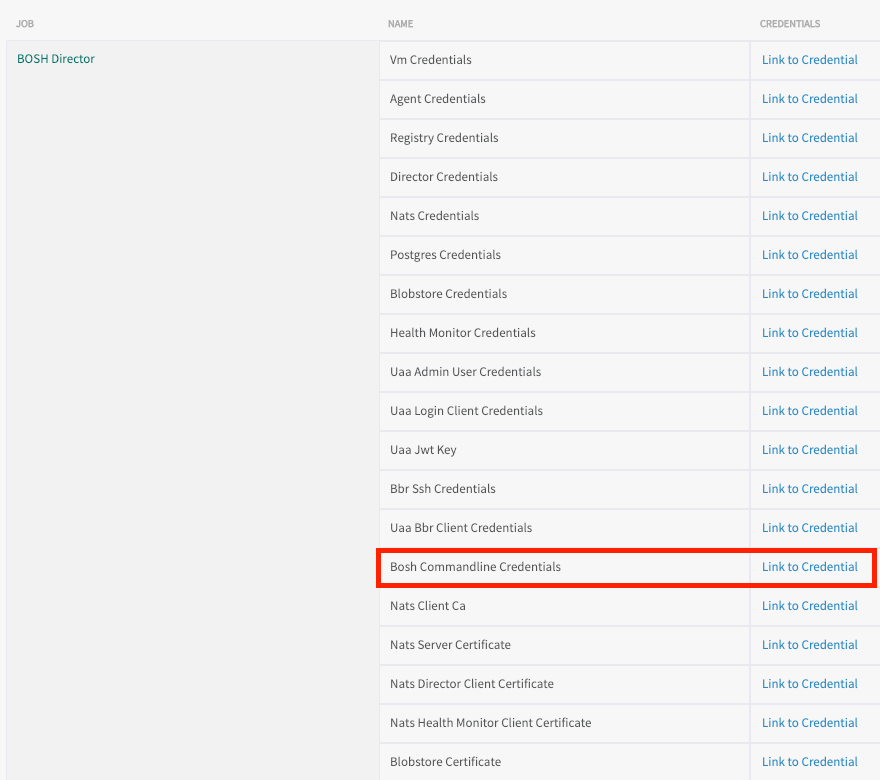
-
Record the values for
BOSH_CLIENTandBOSH_CLIENT_SECRET.Here is an example of the credentials page:
{"credential":"BOSH_CLIENT=ops_manager BOSH_CLIENT_SECRET=abCdE1FgHIjkL2m3n-3PqrsT4EUVwXy5 BOSH_CA_CERT=/var/tempest/workspaces/default/root_ca_certificate BOSH_ENVIRONMENT=10.0.0.5 bosh "}The
BOSH_CLIENTis the BOSH CredHub client name and theBOSH_CLIENT_SECRETis the BOSH CredHub client secret.
Set a Custom CA Certificate
Prerequisite: To complete this procedure, you must have the CredHub CLI. For installation instructions, see credhub-cli on GitHub.
Do this procedure if you are providing your own custom CA certificate instead of using the one generated by Tanzu Operations Manager or CredHub.
To add a custom CA Certificate to CredHub:
-
Record the information needed to log in to the BOSH Director VM by following the procedure in Gather Credential and IP Address Information.
-
Log in to the Tanzu Operations Manager VM by following the procedure in Log in to the Tanzu Operations Manager VM with SSH.
-
Set the API target of the CredHub CLI as your CredHub server by running:
credhub api \ https://BOSH-DIRECTOR-IP:8844 \ --ca-cert=/var/tempest/workspaces/default/root_ca_certificateWhere
BOSH-DIRECTOR-IPis the IP address of the BOSH Director VM.
For example:$ credhub api \
https://10.0.0.5:8844 \
--ca-cert=/var/tempest/workspaces/default/root\_ca\_certificate -
Log in to CredHub by running:
credhub login \ --client-name=CREDHUB-CLIENT-NAME \ --client-secret=CREDHUB-CLIENT-SECRETWhere:
CREDHUB-CLIENT-NAMEis the value you recorded forBOSH_CLIENTin Find the CredHub Credentials in Tanzu Operations Manager.CREDHUB-CLIENT-SECRETis the value you recorded forBOSH_CLIENT_SECRETin Find the CredHub Credentials in Tanzu Operations Manager.
For example:
$ credhub login \
--client-name=credhub \
--client-secret=abcdefghijklm123456789 -
Use the CredHub CLI to provide a CA certificate. Your deployment can have multiple CA certificates. VMware recommends a dedicated CA certificate for services. Create a new file called
root.pemwith the contents of the certificate. Then, run the following command, specifying the path toroot.pemand the private key for the certificate. For example:$ credhub set \
--name="/services/tls_ca" \
--type="certificate" \
--certificate=./root.pem \
--private=ERKSOSMFF...
Add the CA Certificate
Prerequisite: To complete this procedure, you must have the CredHub CLI. For installation instructions, see credhub-cli on GitHub.
To add the CA Certificate to Tanzu Operations Manager:
-
Record the CA certificate by running:
credhub get \ --name=/services/tls_ca \ -k ca -
Go to Tanzu Operations Manager Installation Dashboard > BOSH Director > Security.
-
Append the contents of the CA certificate you recorded in an earlier step into Trusted Certificates.
-
Click Save.
-
Ensure relevant app security groups are open for port 16379. This can be done through the Cloud Foundry Command Line Interface (cf CLI). For more information, see Managing ASGs with the cf CLI.
Enable TLS in Redis for Tanzu Application Service
To enable TLS in the Redis for Tanzu Application Service tile:
- Enable TLS by doing one of the following:
- If you are configuring TLS for an existing installation: Follow the procedure in Upgrade Redis for VMware Tanzu Application Service.
- If you are configuring TLS for a new installation: Follow the procedures in Configure On-Demand Service Settings, including enabling TLS in the On-Demand Service Settings tab.
- Navigate to Tanzu Operations Manager Installation Dashboard > Review Pending Changes.
- Ensure that the CA certificate is deployed to all VMs by selecting:
- VMware Tanzu Application Service for VMs
- Redis for VMware Tanzu Application Service
- The Upgrade All On-Demand Service Instances errand
- Click Apply Changes. This restarts all the VMs in your deployment and applies your CA certificate.