This topic tells you how an administrator can test the OpenID Connect (OIDC) connection between Single Sign‑On for VMware Tanzu Application Service and Microsoft Entra ID.
You can test your identity provider integration by deploying the Pivotal Single Sign-On Service Sample Applications.
Follow the steps below to test your Single Sign‑On connection.
-
Log in to Apps Manager at
https://apps.SYSTEM-DOMAINand navigate to the org and space where your app is located. -
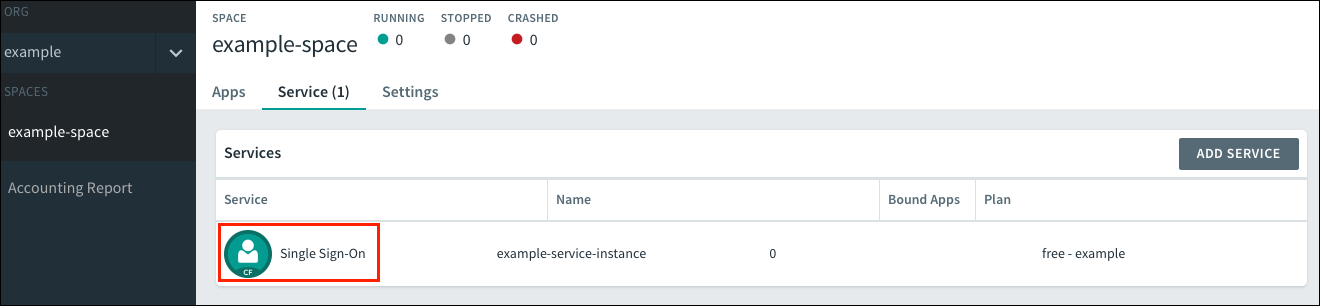
Under Services, locate the service instance of the Single Sign‑On plan bound to your app.
-
Select the service instance and click Manage.

-
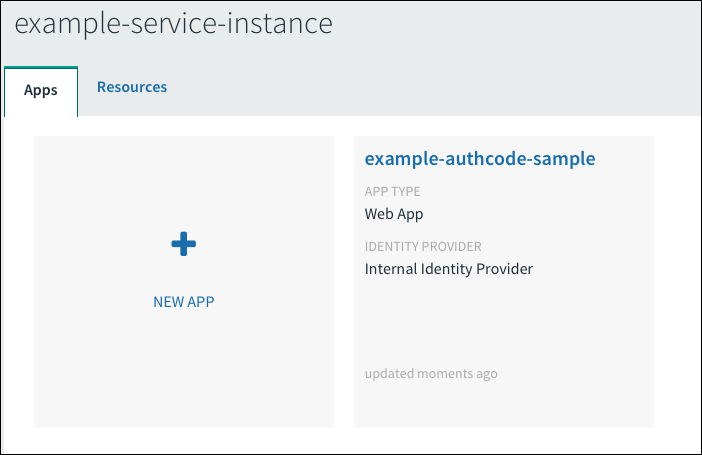
Under the Apps tab, select your app.
-
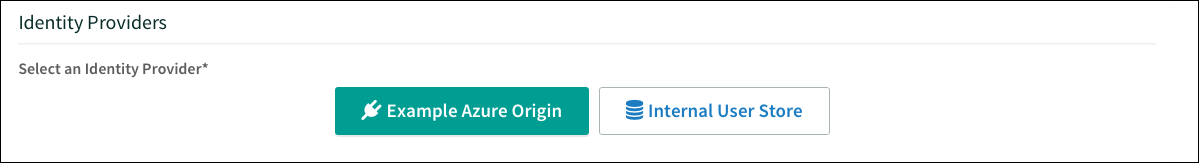
Under Identity Providers, select the Microsoft Entra ID identity provider. Remove any other identity providers.
-
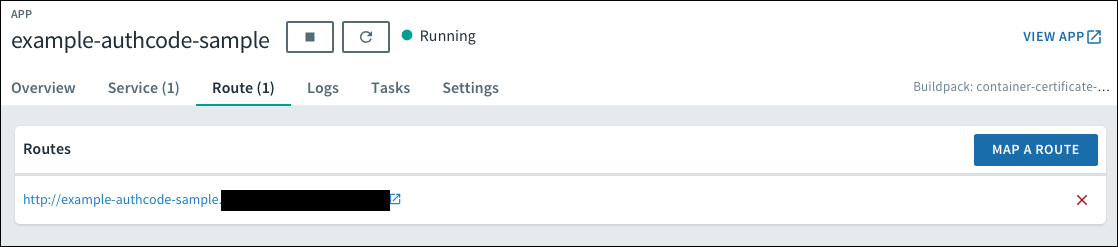
Return to Apps Manager and click the URL listed below your app to access your app.
-
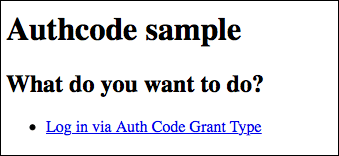
Navigate to your login. You will be redirected to the identity provider to authenticate.
-
On the identity provider sign-in page, enter your credentials and sign in.

-
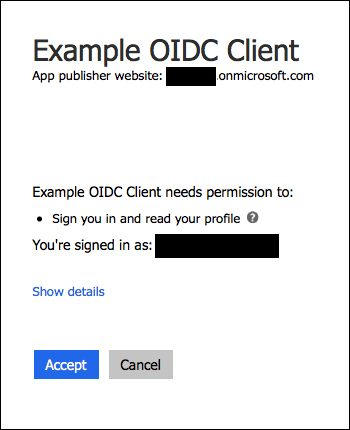
If the app prompts for authorization to the necessary scopes, click Accept.
-
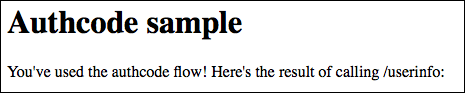
If you are now logged into your app, your Microsoft Entra ID OIDC to Single Sign‑On connection works.