This topic tells you how an administrator can test the connection between Single Sign‑On for VMware Tanzu Application Service and Microsoft Entra ID. An administrator can test both service provider and identity provider connections.
You can test your identity provider integration by deploying the Pivotal Single Sign-On Service Sample Applications.
Test Your Configurations in Microsoft Entra ID
-
Log in to Microsoft Entra ID at https://portal.azure.com/.
-
Navigate to Azure Active Directory (Microsoft Entra ID) > Enterprise Applications.
-
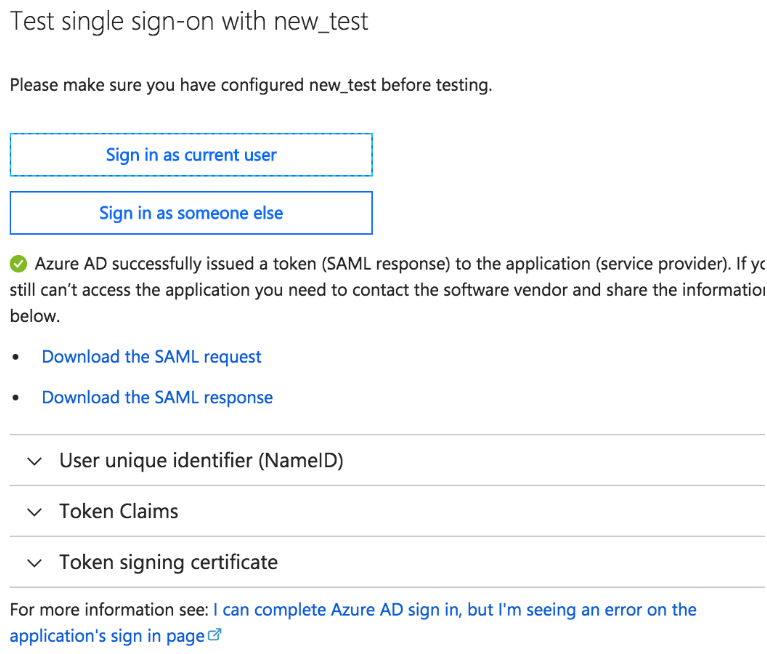
Select your app and navigate to Single Sign-on > Test SAML settings.
-
Select the user that you want to log in as.
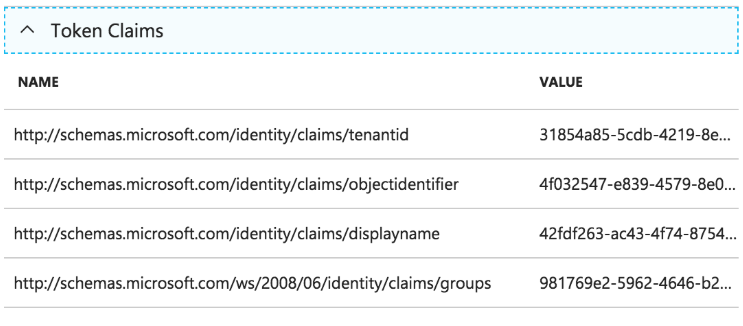
If you have set up all configuration correctly, you should see something like the images below. Otherwise, you should see some meaningful error message.
Test Your Service Provider Connection
-
Log in to Apps Manager at
https://apps.SYSTEM-DOMAINand navigate to the org and space where your application is located. -
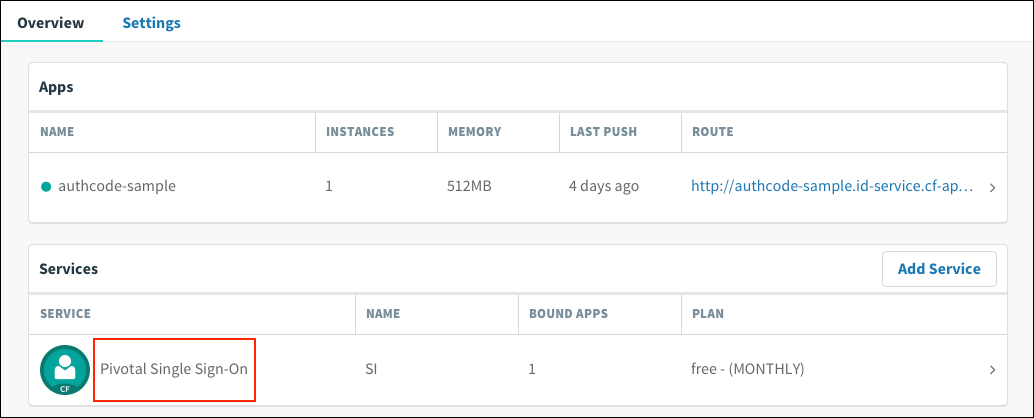
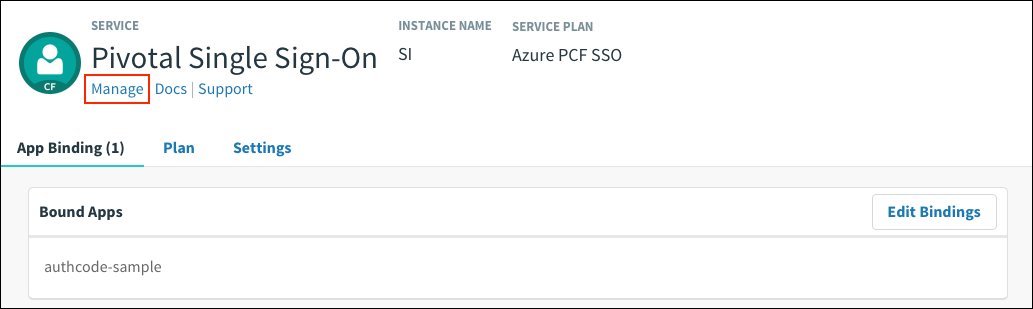
Under Services, locate the service instance of the Single Sign‑On plan bound to your app. Click on the service instance and click Manage.
-
Under the Apps tab, click your app.
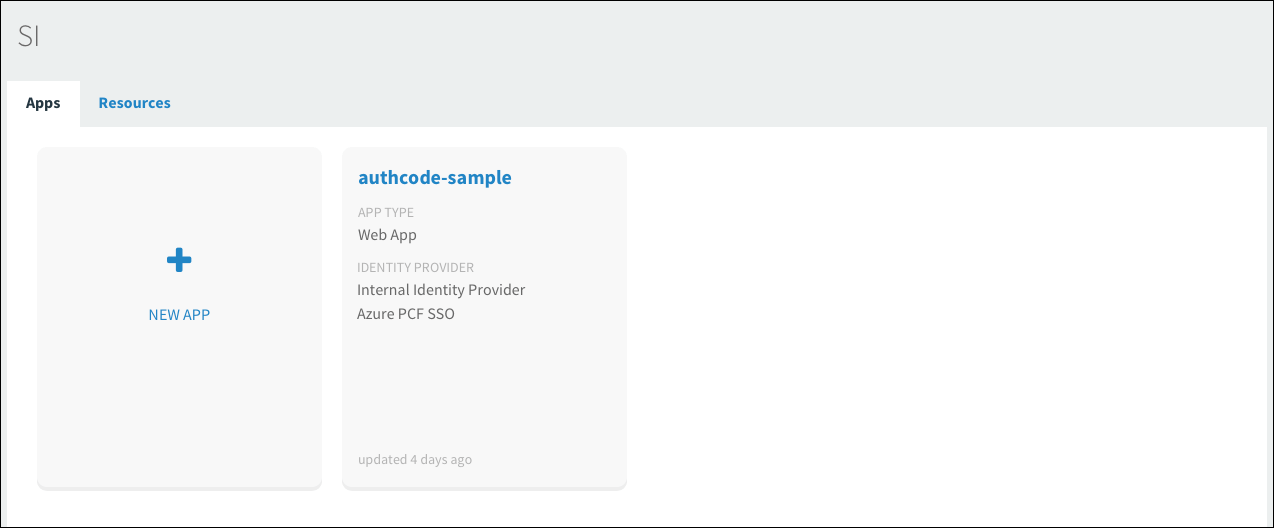
-
Under Identity Providers, select the Microsoft Entra ID identity provider.
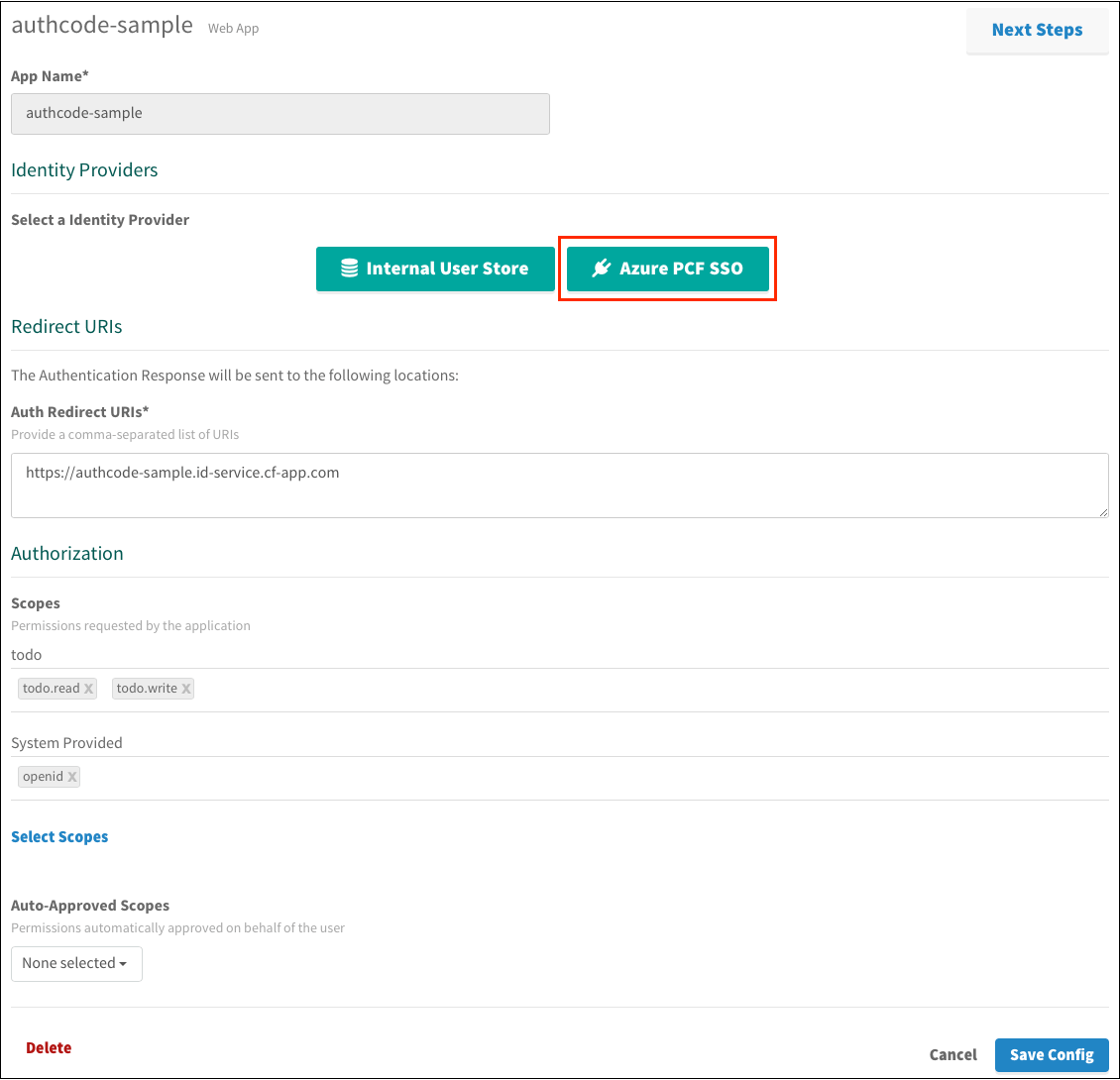
-
Return to Apps Manager and click on the URL below your app to be redirected to the identity provider to authenticate.
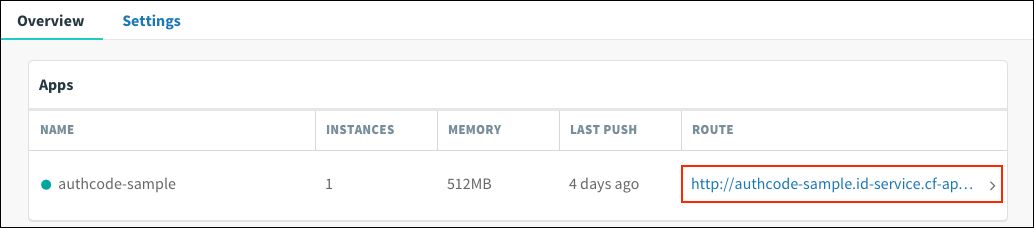
-
Click the link.
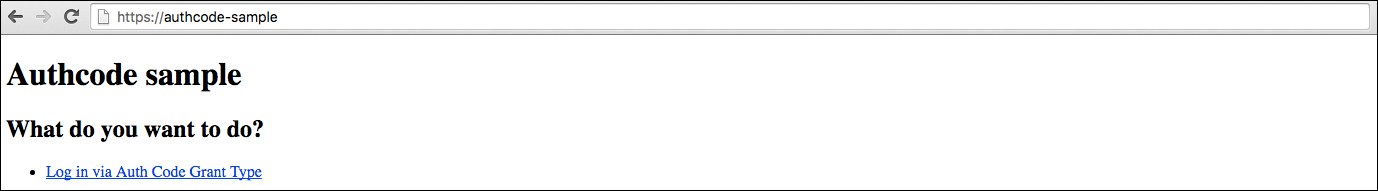
-
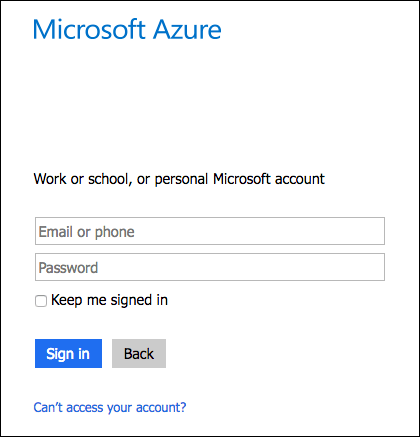
On the identity provider sign-in page, enter your credentials and click Sign In.
-
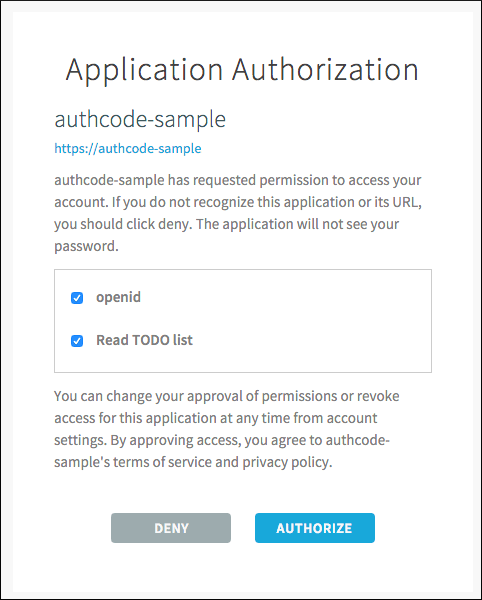
The app asks for authorization to the necessary scopes. Click Authorize.
-
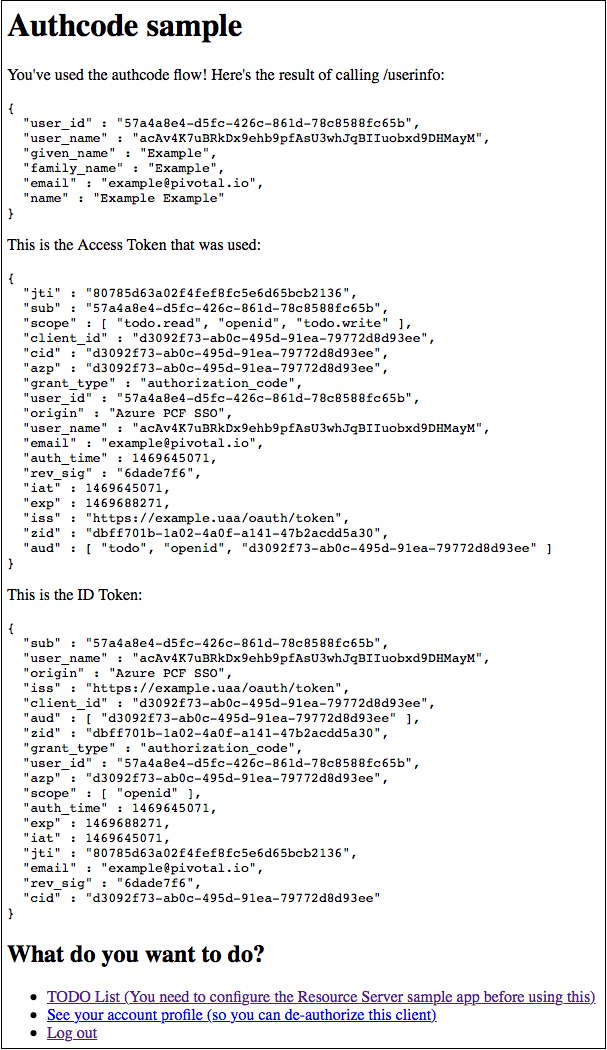
The access token and ID token displays.
Test Your Identity Provider Connection
Single Sign‑On does not support identity provider-initiated flow into applications, but it does redirect the user to the User Account and Authentication (UAA) page to select apps assigned to the user.
-
Sign in to Microsoft Entra ID.

-
Navigate to your app and click it.
-
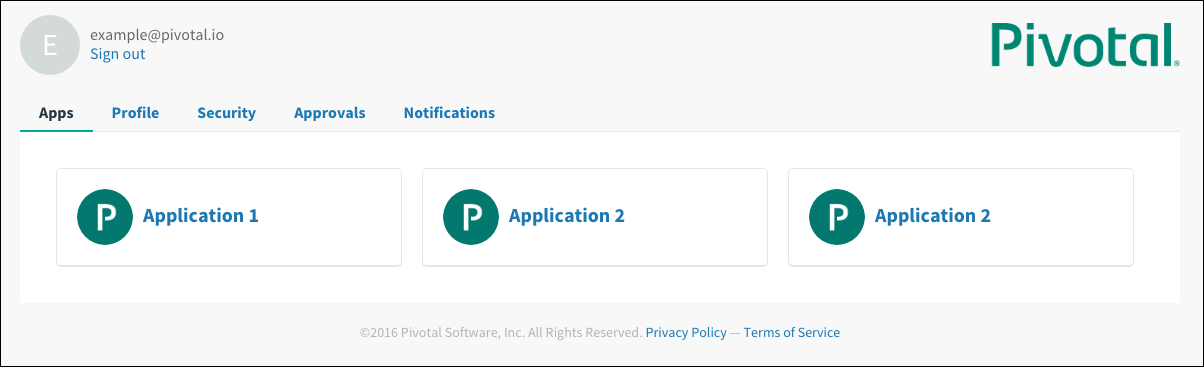
You are redirected to the page that lists apps you have access to.
Test Your Single Sign-Off
Test single sign-off to ensure that when users log out of the application, they are logged out of Microsoft Entra ID as well.
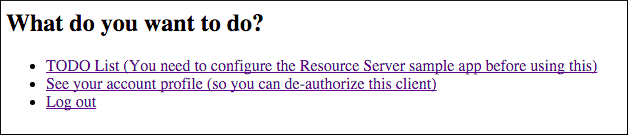
- Sign into the sample app. Information about the access and ID token displays, as well as the “What do you want to do?” section.
-
Under “What do you want to do?”, click Log out.
-
You are logged out and redirected to the Microsoft Entra ID login page.
