You can deploy Unified Access Gateway with Horizon Cloud with On-Premises Infrastructure and Horizon Air cloud infrastructure.
Deployment Scenario
Unified Access Gateway provides secure remote access to On-Premises virtual desktops and applications in a customer data center. This operates with an On-Premises deployment of Horizon or Horizon Air for unified management.
Unified Access Gateway provides the enterprise with strong assurance of the identity of the user, and precisely controls access to their entitled desktops and applications.
Unified Access Gateway virtual appliances are typically deployed in a network demilitarized zone (DMZ). Deploying in the DMZ ensure that all traffic entering the data center to desktop and application resources is traffic on behalf of a strongly authenticated user. Unified Access Gateway virtual appliances also ensure that the traffic for an authenticated user can be directed only to desktop and application resources to which the user is entitled. This level of protection involves specific inspection of desktop protocols and coordination of potentially rapid changing policies and network addresses, to accurately control access.
The following figure shows an example of a configuration that includes front-end and back-end firewalls.
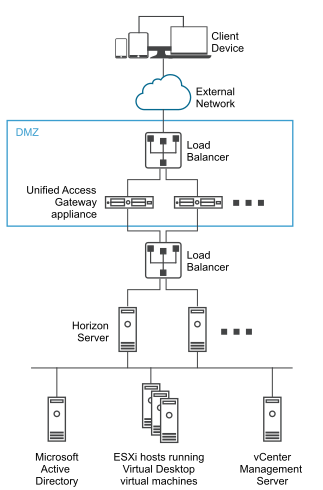
You must verify the requirements for seamless Unified Access Gateway deployment with Horizon.
- Unified Access Gateway appliance points to a load balancer in front of the Horizon servers, the selection of the server instance is dynamic.
- By default, port 8443 must be available for Blast TCP/UDP. However, port 443 can also be configured for Blast TCP/UDP.
Note: If you configure Unified Access Gateway to use both IPv4 and IPv6 mode, then the Blast TCP/UDP must be set to port 443. See Unified Access Gateway Support for IPv4 and IPv6 Dual Mode for Horizon Infrastructure.
- The Blast Secure Gateway and PCoIP Secure Gateway must be enabled when Unified Access Gateway is deployed with Horizon. This ensures that the display protocols can serve as proxies automatically through Unified Access Gateway. The BlastExternalURL and pcoipExternalURL settings specify connection addresses used by the Horizon Clients to route these display protocol connections through the appropriate gateways on Unified Access Gateway. This provides improved security as these gateways ensure that the display protocol traffic is controlled on behalf of an authenticated user. Unauthorized display protocol traffic is disregarded by Unified Access Gateway.
- Disable the secure gateways (Blast Secure Gateway and PCoIP Secure Gateway) on Horizon Connection Server instances and enable these gateways on the Unified Access Gateway appliances.
It is recommended that users deploying Horizon 7 use Unified Access Gateway appliance instead of Horizon security server.
The differences between Horizon security server and Unified Access Gateway appliance is as follows.
- Secure deployment. Unified Access Gateway is implemented as a hardened, locked-down, preconfigured Linux-based virtual machine.
- Scalable. You can connect Unified Access Gateway to an individual Horizon Connection Server, or you can connect it through a load balancer in front of multiple Horizon Connection Servers, giving improved high availability. It acts as a layer between Horizon Clients and back end Horizon Connection Servers. As the deployment is fast, it can rapidly scale up or down to meet the demands of fast-changing enterprises.
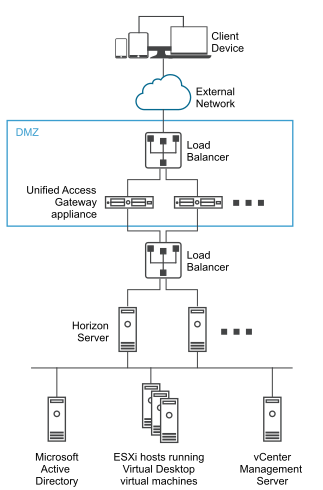
Alternatively you can have one or more Unified Access Gateway appliances pointing to an individual server instance. In both approaches, use a load balancer in front of two or more Unified Access Gateway appliances in the DMZ.
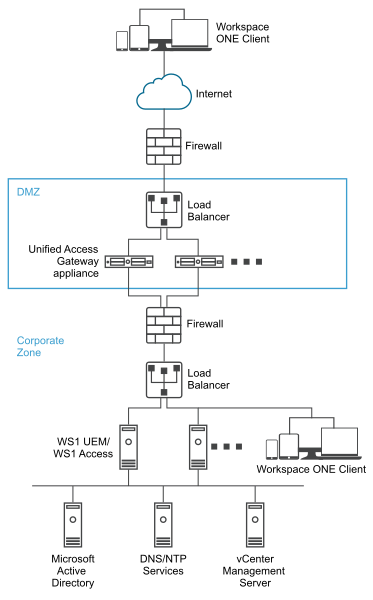
Authentication
User authentication is similar to Horizon security server. Supported user authentication methods in Unified Access Gateway include the following:
- Active Directory user name and password.
- Kiosk mode. For details about Kiosk mode, see the Horizon documentation.
- RSA SecurID two-factor authentication, formally certified by RSA for SecurID.
- RADIUS via various third party, two-factor security-vendor solutions.
- Smart card, CAC, or PIV X.509 user certificates.
- SAML.
These authentication methods are supported with Horizon Connection Server. Unified Access Gateway is not required to communicate directly with Active Directory. This communication serves as a proxy through the Horizon Connection Server, which can directly access Active Directory. After the user session is authenticated according to the authentication policy, Unified Access Gateway can forward requests for entitlement information, and desktop and application launch requests, to the Horizon Connection Server. Unified Access Gateway also manages its desktop and application protocol handlers to allow them to forward only authorized protocol traffic.
Unified Access Gateway handles smart card authentication by itself. This includes options for Unified Access Gateway to communicate with Online Certificate Status Protocol (OCSP) servers to check for X.509 certificate revocation, and so on.