PowerShell scripts prepare your environment with all the configuration settings. When you run the PowerShell script to deploy Unified Access Gateway, the solution is ready for production on first system boot.
However, both Admin UI and the API are not available if the Admin UI password is not provided during deployment. If you do not provide the Admin UI password at the time of deployment, you cannot add a user later to enable access to either the Admin UI or the API. You must redeploy your Unified Access Gateway.
You can include the parameters in the INI file for creating low-priviledged admin users with monitoring roles. Creating superuser admin user is not supported. You can configure the password policies for the root user and admin user before deploying the Unified Access Gateway instance.
For more information about the parameters, you can see the section in which the equivalent admin UI parameter is used. For example: some of the deployment parameters are described in PowerShell Parameters for Deploying Unified Access Gateway and Deploy Unified Access Gateway Using the OVF Template Wizard, for information about parameters used in system configuration, syslog server settings, network settings, and so on, see Configuring Unified Access Gateway From the Admin Configuration Pages, and for information about parameters used in edge services and other use cases of Unified Access Gateway such as Workspace ONE Intelligence and Identify Bridging, see Deployment Use Cases for Unified Access Gateway.
Prerequisites
- For a Hyper-V deployment, and if you are upgrading Unified Access Gateway with static IP, delete the older appliance before deploying the newer instance of Unified Access Gateway.
- Verify that the system requirements are appropriate and available for use.
This is a sample script to deploy Unified Access Gateway in your environment.
Figure 1. Sample PowerShell Script 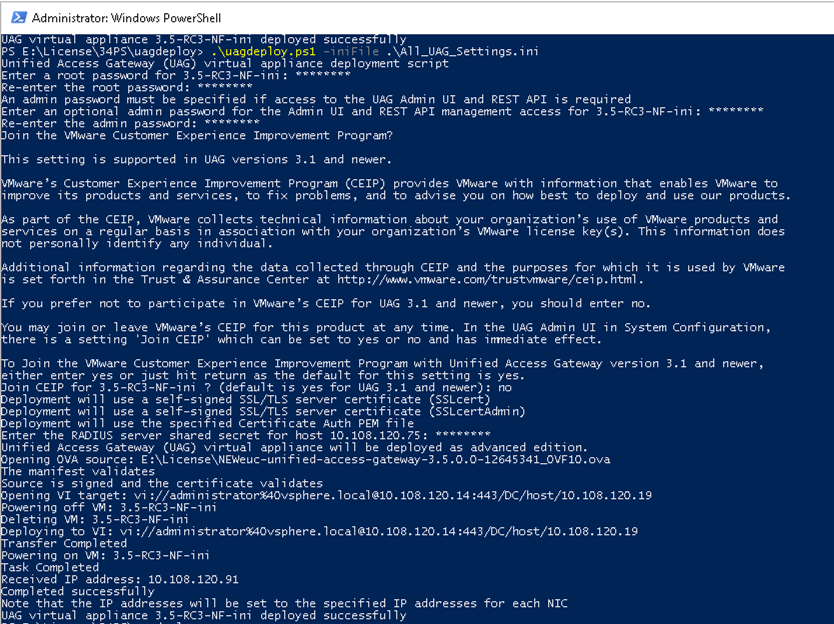
Procedure
Results
What to do next
[General] name=UAG1 source=C:\temp\euc-unified-access-gateway-3.2.1-7766089_OVF10.ova
If you want to upgrade with zero service interruption, see Upgrade with Zero Downtime.