PowerShell scripts prepare you environment with all the configuration settings. When you run the PowerShell script to deploy Unified Access Gateway, the solution is ready for production on first system boot.
However, both Admin UI and the API are not available if the Admin UI password is not provided during deployment.
- If you do not provide the Admin UI password at the time of deployment, you cannot add a user later to enable access to either the Admin UI or the API. You must redeploy your Unified Access Gateway instance with a valid password if you want to add an Admin UI user.
-
Unified Access Gateway 3.5 and later includes an optional
sshEnabledINI property. SettingsshEnabled=truein the[General]section of the PowerShell INI file automatically enablessshaccess on the deployed appliance. VMware does not generally recommend enablingsshon Unified Access Gateway except in certain specific situations and where access can be restricted. This capability is mainly intended for Amazon AWS EC2 deployments where an alternative console access is not available.Note: For more information on Amazon AWS EC2 see, Unified Access Gateway PowerShell Deployment to Amazon Web Services.If
sshEnabled=trueis not specified or is set tofalsethen thesshis not enabled.Enabling
sshaccess on Unified Access Gateway for vSphere, Hyper-V or Microsoft Azure deployments is not generally required as console access with those platforms can be used. If root console access is required for Amazon AWS EC2 deployment, then setsshEnabled=true. In cases wheresshis enabled, TCP port 22 access must be restricted in firewalls or security groups to source IP addresses of individual administrators. EC2 supports this restriction in the EC2 Security Group associated with the Unified Access Gateway network interfaces.
Prerequisites
- For a Hyper-V deployment, and if you are upgrading Unified Access Gateway with static IP, delete the older appliance before deploying the newer instance of Unified Access Gateway.
- Verify that the system requirements are appropriate and available for use.
This is a sample script to deploy Unified Access Gateway in your environment.
Figure 1. Sample PowerShell Script 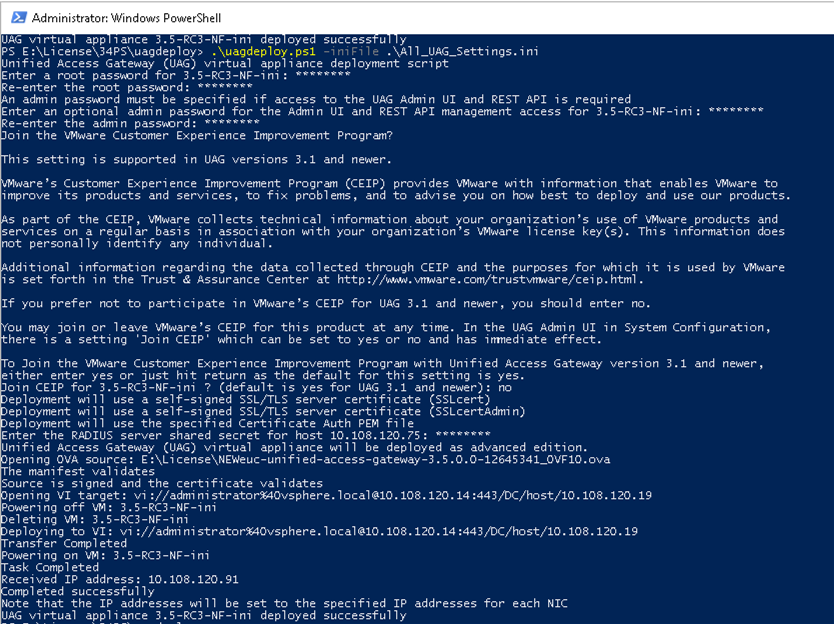
Procedure
Results
What to do next
[General] name=UAG1 source=C:\temp\euc-unified-access-gateway-3.2.1-7766089_OVF10.ova
If you want to upgrade with zero service interruption, see Upgrade with Zero Downtime.