Unified Access Gateway identity bridging mode can be configured to work with VMware Workspace® ONE® either in the cloud or in an on-premises environment.
Using Unified Access Gateway Identity Bridging with Workspace ONE Clients in the Cloud
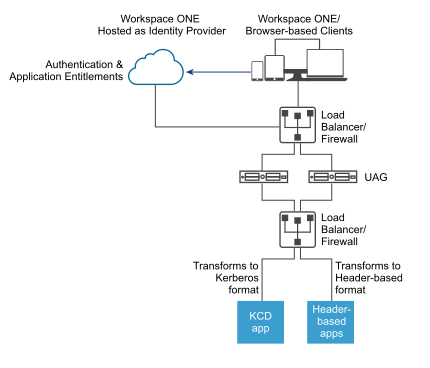
The identity bridging mode can be set up to work with Workspace ONE in the cloud to authenticate users. When a user requests access to a legacy Web application, the identity provider applies applicable authentication and authorization policies.
If the user is validated, the identity provider creates a SAML token and sends it to the user. The user passes the SAML token to Unified Access Gateway in the DMZ. Unified Access Gateway validates the SAML token and retrieves the User Principal Name from the token.
If the request is for Kerberos authentication, Kerberos Constrained Delegation is used to negotiate with the Active Directory server. Unified Access Gateway impersonates the user to retrieve the Kerberos token to authenticate with the application.
If the request is for header-based authentication, the user header name is sent to the Web server to request authentication with the application.
The application sends the response back to Unified Access Gateway. The response is returned to the user.
Using Identity Bridging with Workspace ONE Clients On Premises
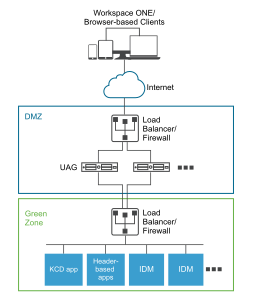
When the identity bridging mode is set up to authentication users with Workspace ONE in an on premises environment, users enter the URL to access the on-premise legacy Web application through the Unified Access Gateway proxy. Unified Access Gateway redirects the request to the identity provider for authentication. The identity provider applies authentication and authorization policies to the request. If the user is validated, the identity provider creates a SAML token and sends the token to the user.
The user passes the SAML token to Unified Access Gateway. Unified Access Gateway validates the SAML token and retrieves the User Principal Name from the token.
If the request is for Kerberos authentication, Kerberos Constrained Delegation is used to negotiate with the Active Directory server. Unified Access Gateway impersonates the user to retrieve the Kerberos token to authenticate with the application.
If the request is for header-based authentication, the user header name is sent to the Web server to request authentication with the application.
The application sends the response back to Unified Access Gateway. The response is returned to the user.
Using Identity Bridging with Certificate to Kerberos
You can configure Identity Bridging to provide single sign-on (SSO) to On-Premises legacy non-SAML applications using certificate validation. See Configure a Web Reverse Proxy for Identity Bridging (Certificate to Kerberos).