Configure the Unified Access Gateway bridging feature to provide single sign-on (SSO) to on-premises legacy non-SAML applications using certificate validation.
Prerequisites
- Keytab file of a back-end application, such as Sharepoint or JIRA
- Root CA certificate or the entire certificate chain with intermediate certificate for the user
- You must have added and uploaded a certificate in the Workspace ONE UEM console. See Enable Workspace ONE UEM Console to Fetch and Use CA Certificates.
See the relevant product documentation to generate the root and user certificates and the keytab file for non-SAML applications.
Ensure that TCP/UDP port 88 is open since Unified Access Gateway uses this port for Kerberos communication with Active Directory.
Procedure
- From , go to:
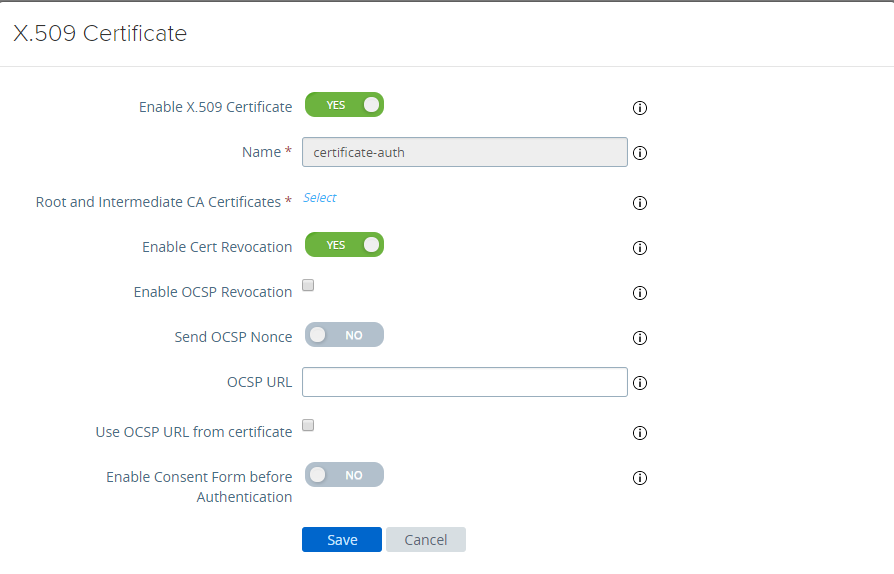
- At Root and Intermediate CA certificate, click Select and upload the entire cert chain.
- At Enable Cert Revocation, set the toggle to Yes.
- Select the check box for Enable OCSP Revocation.
- Enter the OCSP responder URL in the OCSP URL text box.
Unified Access Gateway sends the OCSP request to the specified URL and receives a response that contains information indicating whether or not the certificate is revoked.
- Select the check box Use OCSP URL from certificate only if there is a use case to send the OCSP request to the OCSP URL in the client certificate. If this is not enabled, then it defaults to the value in the OCSP URL text box.
- From , click Add.
- Click Select and upload the OCSP signing certificate.
- Select the Realm Settings gearbox icon and configure the Realm settings as described in Configure Realm Settings.
- From General Settings > Edge Service Settings, select the Reverse Proxy Settings gearbox icon.
- Set Enable Identity Bridging Settings to YES, configure the following Identity Bridging settings, then click Save.
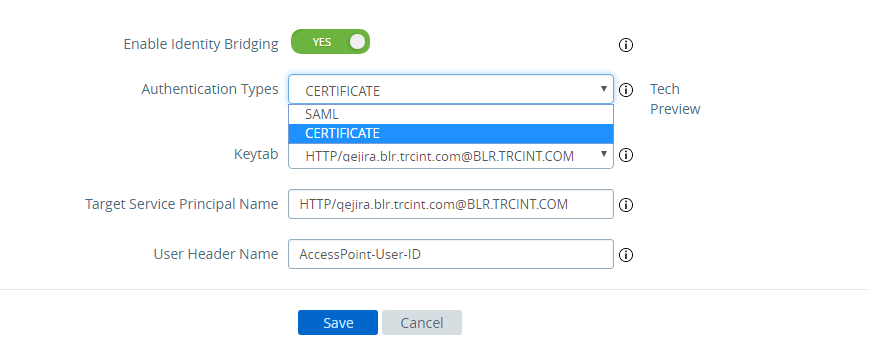
Option Description Authentication Types Select CERTIFICATE from the drop-down menu. Keytab In the drop-down menu, select the configured keytab for this reverse proxy. Target Service Principal Name Enter the Kerberos service principal name. Each principal is always fully qualified with the name of the realm. For example, myco_hostname@MYCOMPANY. Type the realm name in uppercase. If you do not add a name to the text box, the service principal name is derived from the host name of the proxy destination URL. User Header Name For header-based authentication, enter the name of the HTTP header that includes the user ID derived from the assertion or use the default, AccessPoint-User-ID.
What to do next
When you use the Workspace ONE Web to access the target website, the target website acts as the reverse-proxy. Unified Access Gateway validates the presented certificate. If the certificate is valid, the browser displays the user interface page for the back-end application.
For specific error messages and troubleshooting information, see Troubleshooting Errors: Identity Bridging.