How to onboard your Azure subscriptions with the VMware Aria Automation for Secure Clouds API
VMware Aria Automation for Secure Clouds uses a read-only cloud account role to scan the Azure configurations to create an interconnected cloud security model of your environment. The service also uses an activity log event stream from Azure to trigger near real-time notifications of configuration violations.
For Azure resources, the events are generated by monitoring activity logs that trigger a webhook. A provided shell script simplifies setup of stream of activity log events into the service.
Before you start
Before you can onboard an Azure subscription with the API, you need:
- The ID of the Azure subscription you want to onboard.
- Access to the subscription in the Azure console.
- Permissions to register a new Azure Active Directory (Azure AD) app and create a new secret.
- Permissions to enable a new activity log subscription for your account.
- A shell terminal with curl installed or an API development tool capable of making REST API calls, such as Postman.
- An API access token for the VMware Aria Automation for Secure Clouds platform.
Obtain credentials from Azure
You can register an Azure AD application before you start adding any cloud accounts to VMware Aria Automation for Secure Clouds. This makes it easier to retrieve some required information later on in the onboarding process.
Sign into the Azure portal and navigate to Azure Active Directory > App registrations > New registration.
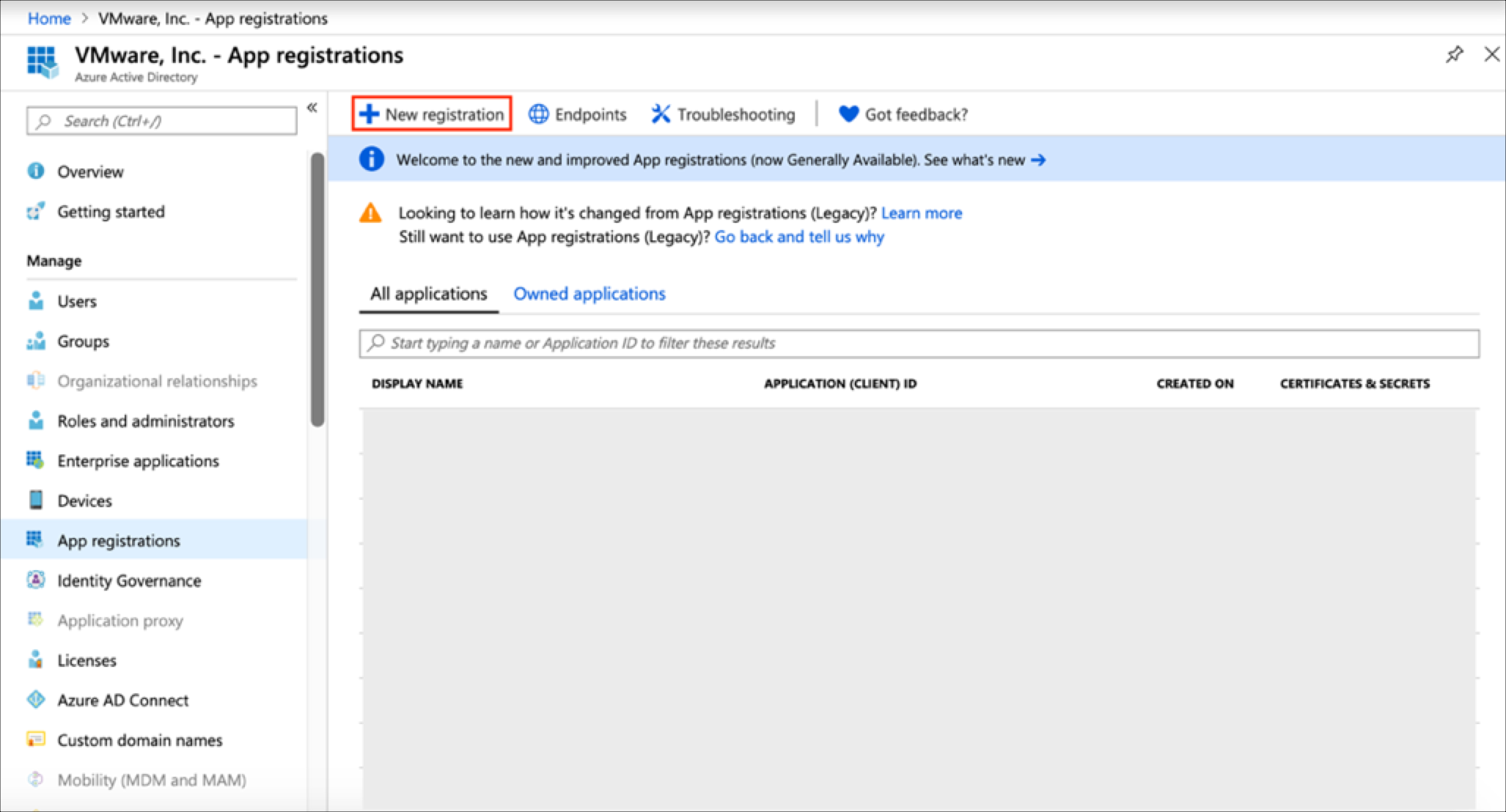
Complete the requested fields and click register.
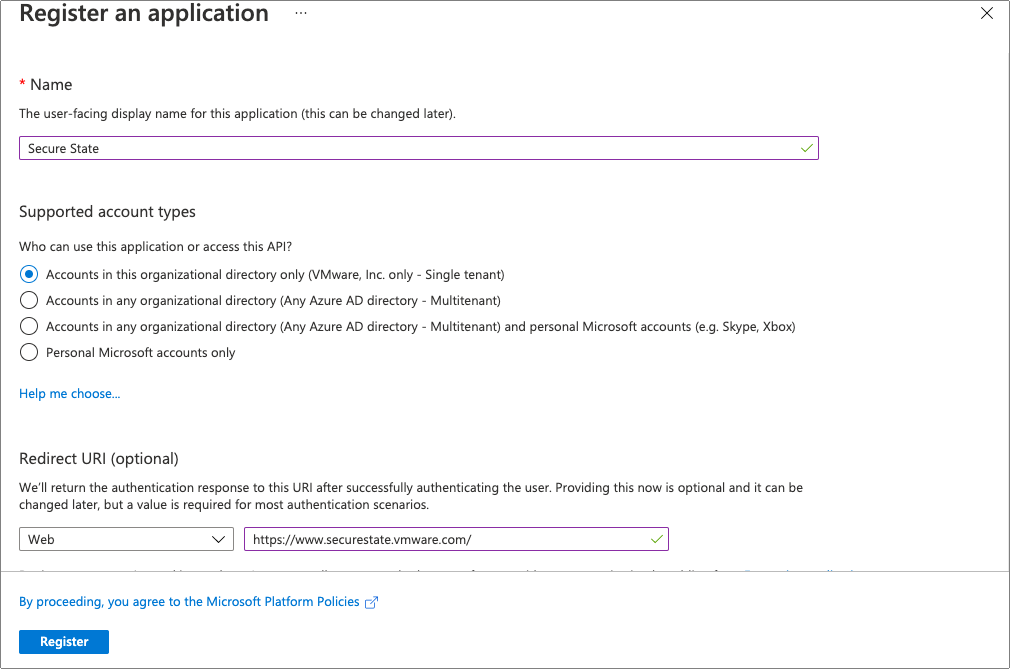
Navigate to Azure Active Directory > App Registrations > Secure State.
Copy the Application (client) ID and Directory (tenant) ID on this page. You must enter them later when onboarding the subscription.
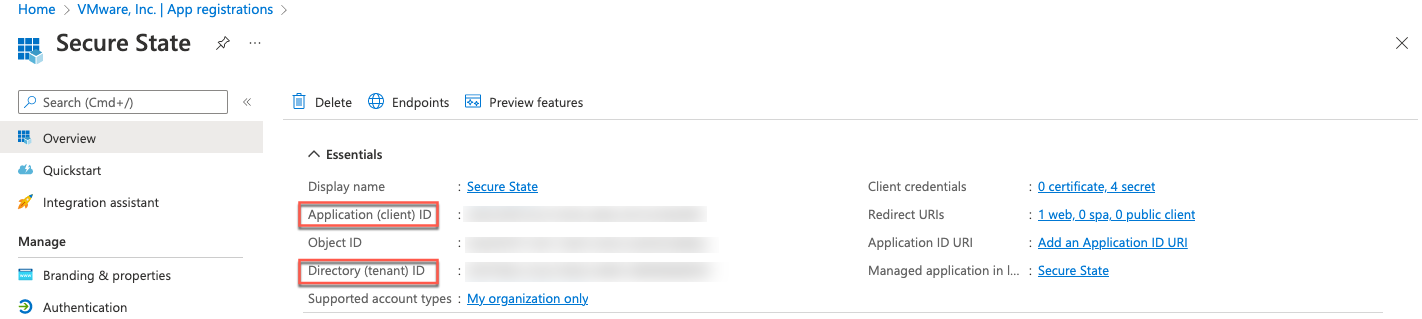
Click the Certificates & secrets link in the sidebar.
Click + New client secret, add a description and expiration time, then copy the Value in a safe location for later use (it becomes unavailable after you leave this page).
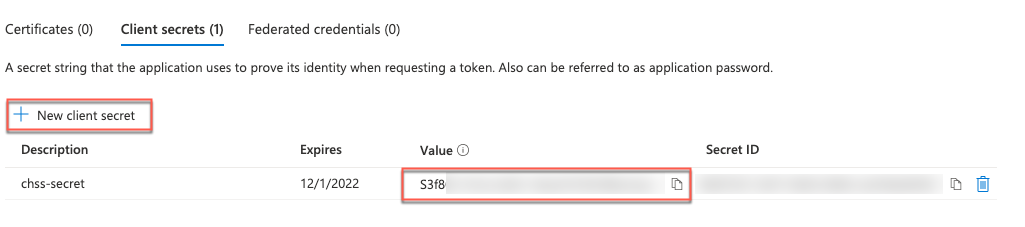
Note: Ensure you copy the Value and not the Secret ID. The latter doesn't work if you try to enter it when onboarding a cloud account for Azure.
Keep the Azure Portal tab open so you can return to it when prompted.
Assign role permissions for VMware Aria Automation for Secure Clouds
Follow these directions in your Azure portal to complete the permission needs for your application registration to communicate with VMware Aria Automation for Secure Clouds.
- From your Azure console, navigate to the Subscriptions page, select your subscription, then select Access control (IAM).
- Select Add > Add role assignment.
- Search for and select the Reader role, then select Next.
- Click Select members, search for the application you created, then click Select.
- Click Review + assign, confirm your assignment, then click Review + assign again.
- Verify the role is assigned by going to Access control (IAM) > Role assignments and searching for your application.
You can now begin onboarding your Azure subscriptions individually or in bulk.
Add a single cloud account
You can onboard an Azure subscription with several API calls to different endpoints using the credential information you obtained in the previous section.
Create a credential for your Azure subscription
Make a cloud-credentials API call to create a credential for your Azure subscription and upload it.
curl -X POST \
https://api.securestate.vmware.com/v1/providers/azure/cloud-credentials/ \
-H 'Authorization: Bearer {access_token}' \
-d '{
"credentialType": "collection",
"provider": "azure",
"properties": [
{
"name": "ApplicationId",
"type": "string",
"stringV": "{Application client ID}"
},
{
"name": "ApplicationKey",
"type": "string",
"stringV": "{Client secret}"
},
{
"name": "DirectoryId",
"type": "string",
"stringV": "{Directory tenant ID}"
}
]
}'
A successful response confirms the information you entered and returns the credentialId. Copy it for us in the next call.
Response body
{
"credentialId": "<Credential ID",
"credentialType": "collection",
"provider": "azure",
"properties": [
{
"name": "DirectoryId",
"type": "string",
"stringV": "{Directory tenant ID}"
},
{
"name": "ApplicationId",
"type": "string",
"stringV": "{Application client ID}"
}
],
"eTag": "{e-tag}",
"createdTime": "{timestamp}",
"lastUpdateTime": "{timestamp}"
}
Create and associate a cloud account for your Azure subscription
Next, make a call to the bulk-update API to create a cloud account for your Azure subscription and link it with the credentials you just uploaded. The cloudAccountName field accepts a string value of your choice, while cspProjectId can be either default, or another project you would like to add your account under. If the AccountType property isn't included, the cloud account onboards as a commercial type into the service by default.
curl -X POST \
https://api.securestate.vmware.com/v1/cloud-accounts/bulk-update \
-H 'Authorization: Bearer {access_token}' \
-d '{
"provider": "azure",
"cloudAccountUpdates": [
{
"action": "post",
"cloudAccountName": "{Azure subscription name}",
"cspProjectId": "{CSP project ID}",
"environment": "None",
"ownerInfo": {
"email": "{Owner email address}",
"name": "{Owner name}"
},
"properties": [
{
"name": "subscriptionId",
"type": "string",
"stringV": "{Azure subscription ID}"
},
{
"name": "AccountType",
"type": "string",
"stringV": "{Commercial or Government}"
}
]
}
],
"relationshipUpdates": [
{
"action": "post",
"cloudAccountId": "{Azure subscription ID}",
"credentialId": "{Credential ID}"
}
]
}'
Note: The environment and ownerInfo fields are optional, and can be removed from the request if preferred.
You can use the bulk update API to upload single or multiple Azure subscriptions, as seen in the request example. You can add as many subscriptions and credentials as necessary to the cloudAccountUpdates and relationshipUpdates arrays, though Azure does let you share a single credential across multiple subscriptions if desired.
A successful response confirms the information you entered, along with general account status and timestamps.
Response Body
{
"cloudAccountUpdates": [
{
"action": "post",
"cloudAccountId": "{Azure subscription ID}",
"cloudAccountName": "{Azure subscription name}",
"cspProjectId": "{CSP Project ID}",
"provider": "azure",
"accountStatus": {
"value": "{Account status value}",
"lastUpdateTime": "{timestamp}"
},
"rollupStatus": {
"value": "{Rollup status value}",
"lastUpdateTime": "{timestamp}"
},
"properties": [
{
"name": "subscriptionId",
"type": "string",
"stringV": "{Azure subscription ID}"
}
...
],
"eTag": "{e-tag}",
"createdTime": "{timestamp}",
"lastUpdateTime": "{timestamp}"
}
...
],
"relationshipUpdates": [
{
"action": "post",
"cloudAccountId": "{Azure subscription ID}",
"credentialId": "{Credential ID}",
"eTag": "{e-tag}",
"createdTime": "{timestamp}",
"lastUpdateTime": "{timestamp}"
}
...
]
}
Add multiple cloud accounts
VMware Aria Automation for Secure Clouds supports bulk onboarding for situations where you need to onboard a large number of Azure subscriptions. You can use this feature to onboard up to 100 subscriptions in the same management group with one action. If you need to onboard more than 100 subscriptions, you do so with additional bulk-update API calls after completing the directions in this section. Subscriptions may be onboarded from the root management group or sub-management group, as long as they are associated with the same Azure AD tenant.
If you have already onboarded some subscriptions from the same management group as individual cloud accounts, ensure they all use the same credentials (application ID and client secret) as the subscriptions you plan to onboard in bulk. VMware Aria Automation for Secure Clouds recognizes any Azure cloud accounts with shared credentials as part of the same management group. To change a credential for an Azure cloud account, see the manage cloud account credentials section.
Create a credential for your Azure subscriptions
Make a cloud-credentials API call to create and upload a credential with the information you gathered from your Azure AD application.
curl -X POST \
https://api.securestate.vmware.com/v1/providers/azure/cloud-credentials/ \
-H 'Authorization: Bearer {access_token}' \
-d '{
"credentialType": "collection",
"provider": "azure",
"properties": [
{
"name": "ApplicationId",
"type": "string",
"stringV": "{Application client ID}"
},
{
"name": "ApplicationKey",
"type": "string",
"stringV": "{Client secret}"
},
{
"name": "DirectoryId",
"type": "string",
"stringV": "{Directory tenant ID}"
}
]
}'
A successful response confirms the information you entered and returns the credentialId. Copy it for use in the next call.
Create and associate cloud accounts for your Azure subscriptions
Make a bulk-update API call to create cloud accounts with information from your Azure subscriptions and associate them with the credential ID you uploaded in the previous steps. You can use the same credential ID for every subscription you onboard in this call, as long as they are under the same root management group.
curl -X POST \
https://api.securestate.vmware.com/v1/cloud-accounts/bulk-update \
-H 'Authorization: Bearer {access_token}' \
-d '{
"provider":"azure",
"cloudAccountUpdates":[
{
"provider":"azure",
"cloudAccountId":"{Azure subscription ID 1}",
"cloudAccountName":"{Azure subscription name 1}",
"cspProjectId":"default",
"environment": "None",
"ownerInfo": {
"email": "{Owner email address}",
"name": "{Owner name}"
},
"properties":[
{
"name":"SubscriptionId",
"type":"string",
"stringV":"{Azure subscription ID 1}"
}
],
"action":"post"
},
{
"provider":"azure",
"cloudAccountId":"{Azure subscription ID 2}",
"cloudAccountName":"{Azure subscription name 2}",
"cspProjectId":"default",
"environment": "None",
"ownerInfo": {
"email": "{Owner email address}",
"name": "{Owner name}"
},
"properties":[
{
"name":"SubscriptionId",
"type":"string",
"stringV":"{Azure subscription ID 2}"
}
],
"action":"post"
},
{
"provider":"azure",
"cloudAccountId":"{Azure subscription ID 3}",
"cloudAccountName":"{Azure subscription name 3},
"cspProjectId":"default",
"environment": "None",
"ownerInfo": {
"email": "{Owner email address}",
"name": "{Owner name}"
},
"properties":[
{
"name":"SubscriptionId",
"type":"string",
"stringV":"{Azure subscription ID 3}"
}
],
"action":"post"
}
],
"credentialUpdates":[
],
"relationshipUpdates":[
{
"action":"post",
"cloudAccountId":"{Azure subscription ID 1}",
"credentialId":"{Credential ID}"
},
{
"action":"post",
"cloudAccountId":"{Azure subscription ID 2}",
"credentialId":"{Credential ID}"
},
{
"action":"post",
"cloudAccountId":"{Azure subscription ID 3}",
"credentialId":"{Credential ID}"
}
]
}'
A successful response confirms the information you entered, along with general status updates and timestamps.
Manage cloud account credentials
Follow these steps to change the credential associated with your cloud accounts after onboarding.
Use this call to delete the credential.
curl -X DELETE \ https://api.securestate.vmware.com/v1/providers/{provider}/cloud-credentials/{credentialId} \ -H 'Authorization: Bearer {access_token}'Add a new credential to the cloud account with this call.
curl -X POST \ https://api.securestate.vmware.com/v1/providers/{provider}/account-credential-relationship \ -H 'Authorization: Bearer {access_token}' \ -d '{ "cloudAccountId": "{cloud account ID}", "credentialId": "{credential ID}" }'
Event stream setup
VMware Aria Automation for Secure Clouds uses event streams through Azure Activity logs to provide real-time inspection of changes and to dynamically update the cloud infrastructure model. Enter this command in the Azure Cloud Shell to download and run the event stream setup shell script:
curl https://api.securestate.vmware.com/download/onboarding/azure/bulk/vss_azure_bulk_event_stream_setup.sh --output vss_azure_bulk_event_stream_setup.sh && /bin/bash vss_azure_bulk_event_stream_setup.sh <Subscription ID 1> <Subscription ID 2> <Subscription ID 2>
On successful execution of this command, the Azure subscription is configured to send activity log events to VMware Aria Automation for Secure Clouds. To verify the event stream is active, follow these steps:
- From the VMware Aria Automation for Secure Clouds dashboard, navigate to Settings > Cloud accounts.
- Locate your cloud account in the list, filtering as necessary.
- If the Status field displays a green checkmark, then the event stream is active for your account.
- You can click on the Account Name to see additional details regarding event stream status and cloud account metadata.
While the event stream is active, you should see real-time updates in the service for any changes in your cloud account that trigger or resolve a violation.