How to integrate Jira Cloud with VMware Aria Automation for Secure Clouds
Configure your Jira Cloud integration
The VMware Aria Automation for Secure Clouds Jira Cloud integration can be used to create issues from security findings, where they can be tracked and resolved through your team's existing ticketing framework.
Log in to VMware Aria Automation for Secure Clouds.
Navigate to Settings > Integrations.
Under Jira Cloud, select Add New.
Enter the following required values:
- Integration name - Choose a name for your integration.
- Username - Enter the email address you use to log in to your Jira organization.
- API token - Click on the provided API token link to create a token with Jira. Copy the value into this field.
- Organization name - You can find the organization name in the URL for your Jira Cloud page, which should be yourcompany.atlassian.net. In this case, the organization name would be "yourcompany".
- Project key - The project key is the prefix you have your issue IDs. For example, if "JRA-123" is how your organization assigns IDs, then JRA is the project key.
- Issue type - Your options for this field depend on which issue types your organization supports. See the Jira Cloud Issue Types documentation for more information.
- Fields Template - This field is optional, but allows you to customize the ticket template associated with this integration. See Customizing your Jira Cloud ticket template for more details on how to use this field.
If you're an organization admin, you can select the context (Organization or Project) you want the integration to have access to on the next page.
Click Test to verify a working connection, then click Save.
After you've set up the integration, you must create a Jira alert to begin creating issues from findings.
The following is an example of the default ticket template you receive on a finding when you set up the integration and alert:
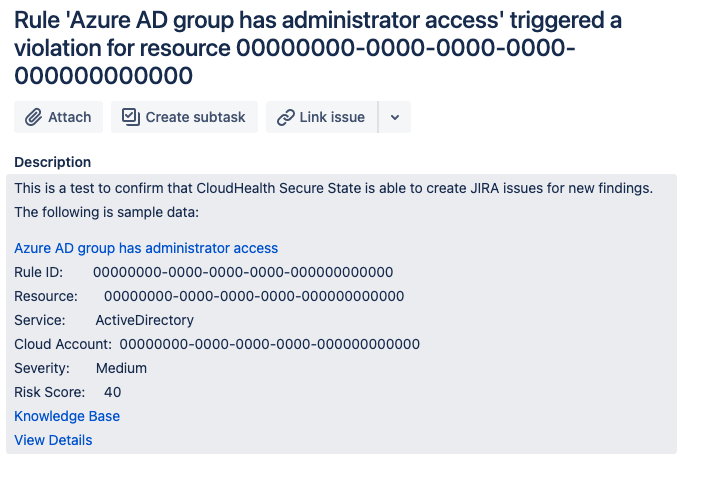
Customizing your Jira Cloud ticket template
As you can see from the last section, the summary and description fields come with default values at first. You may want to change these values, add other common fields, or include custom fields for your organization. You can do this by adding a valid JSON object to the Fields Template during or after initial configuration that customizes the available fields in the template.
You can validate the JSON by clicking the Test button during the Jira Cloud integration setup process and seeing if you get an error.
Add a custom field
Let's say you want to add a custom field that represents a team you want all Jira tickets assigned to. For this, you must obtain the id and name values for the custom field, which can get by making a call to this API - https://your-domain.atlassian.net/rest/api/3/field. For readability, try making this call with an API testing tool like Postman, or copy the output into an online JSON formatter.
In this example, the custom field has "id": "customfield_10811" and "name": "Team". To add it, enter this JSON object in the fields template:
{
"customfield_10811" : {"value" : "Fixers"},
"labels": ["SecureStateOps"]
}
Jira tickets now generate with a pre-defined value for the custom field, and adds a label as well.
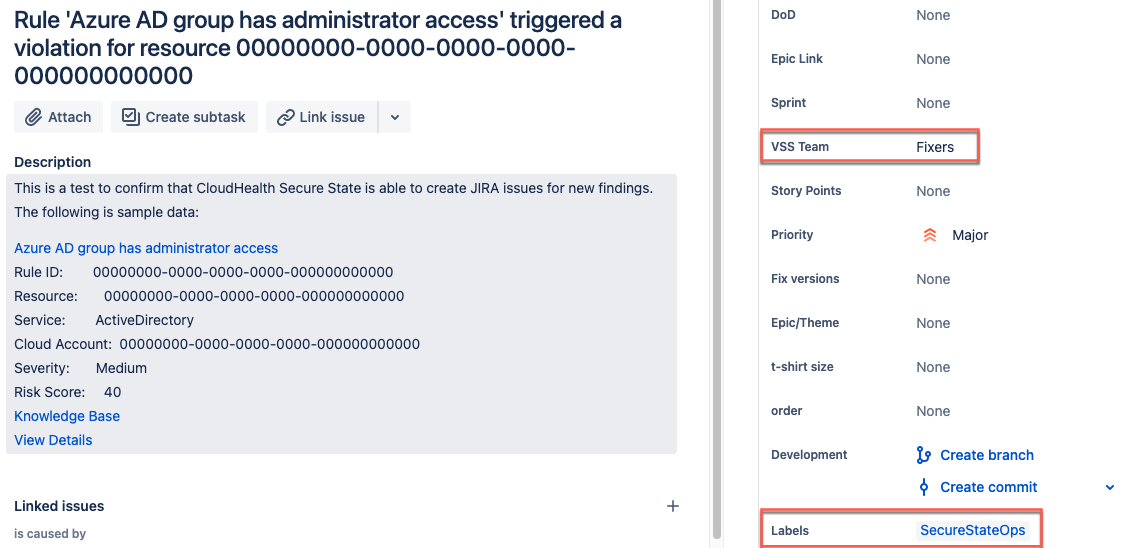
Override a pre-defined field
As stated, the summary and description fields are already defined by the base template when you configure a Jira Cloud integration. However, you can override both of these fields with your own preferred message if desired.
The following takes the previous JSON example and adds a new description:
{
"customfield_10811" : {"value" : "Fixers"},
"labels": ["SecureStateOps"],
"description:" "This is an override of the description."
}
After saving your changes, description will be replaced on future tickets.
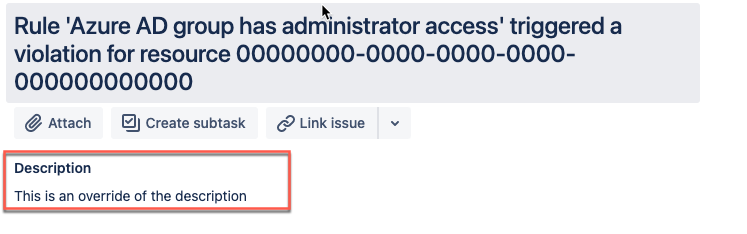
Adding variables to fields
VMware Aria Automation for Secure Clouds uses Mustache variables to add a finding's attributes to the ticket template. You can do this by including a mustache variable in this format: {{ Finding.attribute }}.
The following JSON object appends the finding ID and risk score to the description override:
{
"customfield_10811" : {"value" : "Fixers"},
"labels": ["SecureStateOps"],
"description:" "This is an override of the description. Finding ID = {{ Finding.ID }}, RiskScore = {{ Finding.RiskScore }}"
}
Future tickets now display the specific finding ID and risk score for any violation that alerts through the integration.

You can refer to this table breakdown of the Jira Cloud alert JSON template for all the available findings attributes you can add as variables.
| Element | Description | Example |
|---|---|---|
| Name | Name of your alert. | My Alert |
| Message | Additional message sent to the recipient of the alert. | This is a Jira alert for my cloud accounts. |
| Finding | A list of attributes for the finding that triggered the alert. | |
| ID | Unique ID for the finding. | 00000000-0000-0000-0000-000000000000 |
| RuleDisplayName | Public name of the rule for the triggered finding. | Azure AD group has administrator access |
| RuleName | Name of the cloud account where your affected resource resides. | Database name of the rule for the triggered finding. |
| RuleService | Service type of the triggered finding. | ActiveDirectory |
| RuleSeverity | Severity of the triggered finding (High, Medium, or Low). | Medium |
| CloudAccountID | ID of the cloud account where your affected resource resides. | 00000000-0000-0000-0000-000000000000 |
| CloudAccountName | Name of the cloud account where your affected resource resides. | Azure-Cloud-Dev |
| CloudAccountEnvironment | The environment type assigned to the cloud account. | development |
| CloudAccountProjectID | ID of the VMware Aria Automation for Secure Clouds project where the cloud account resides. | 00000000-0000-0000-0000-000000000000 |
| Source | Specifies if the finding is from a native or third-party rule. | Native |
| Provider | Provider associated with the cloud account where the affected resource resides. | azure |
| Service | Service type of the affected resource. | ActiveDirectory |
| Region | Region of the affected resource. | global |
| RiskScore | Risk score of the finding. | 40 |
| Timestamp | Timestamp from when the event was observed. | 2020-01-01T12:00:00.000Z |
| Tags | A list of tags associated with affected resource. | |
| Key | Name of the tag. | Owner |
| Value | Value of the tag. | [email protected] |
| Last | Indicates the last tag in the list. | FALSE |