You can apply secret, encrypted values to Terraform configurations that you add to Automation Assembler cloud template designs.
- In your git repository, add a Terraform configuration source file that references the secret properties as variables.
In this Terraform configuration source example, API and application keys are the secret variables.
variable "datadog_api_key" { description = "Datadog API Key" } variable "datadog_app_key" { description = "Datadog App Key" } provider "datadog" { api_key = "${var.datadog_api_key}" app_key = "${var.datadog_app_key}" } # Create a new monitor resource "datadog_monitor" "default" { # ... } # Create a new timeboard resource "datadog_timeboard" "default" { # ... } - In Automation Assembler, go to , and enter your secret property values.
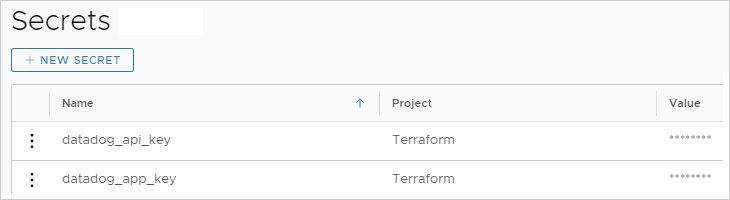
Add secret names and corresponding values. For the names, it's easiest to simply enter the same name as the variable name from your Terraform source.
If needed, see Secret Automation Assembler properties for more details.
- In Automation Assembler, import the Terraform configuration for use in a cloud template.
Go to and click .
Note: Even though the variables appear for selection on the last page of the wizard, you do not need to set the secret variables as sensitive. Secret Automation Assembler variables will already be encrypted and do not need the encryption that the wizard applies.If needed, see Designing for Terraform configurations in Automation Assembler for more details.
The example cloud template should look similar to the following code:
inputs: datadog_api_key: type: string description: Datadog API Key datadog_app_key: type: string description: Datadog App Key resources: terraform: type: Cloud.Terraform.Configuration properties: variables: datadog_api_key: '${input.datadog_api_key}' datadog_app_key: '${input.datadog_app_key}' providers: [] terraformVersion: 0.12.29 configurationSource: repositoryId: 0fbf8f5e-54e1-4da3-9508-2b701gf25f51 commitId: ed12424b249aa50439kr1c268942a4616bd751b6 sourceDirectory: datadog - In the code editor, for the secret values, manually change
inputtosecretas shown.terraform: type: Cloud.Terraform.Configuration properties: variables: datadog_api_key: '${secret.datadog_api_key}' datadog_app_key: '${secret.datadog_app_key}' - In the
inputs:section of the code, remove the input entries that were replaced by the bindings to secret properties.