You can search for and filter log events on the Explore Logs page by entering queries in the search text box.
Procedure
- Enter keywords, globs, or phrases in the search text box and click the Search button to find only events that contain the keywords.
Use the glob * in search terms for zero or more characters. For example, searching for vm* returns results that match VMware and VMtools.Note: You cannot use globs as the first character of a search term. For example, you can use 192.168.0.*, but you cannot use *.168.0.0 in your filtering queries.
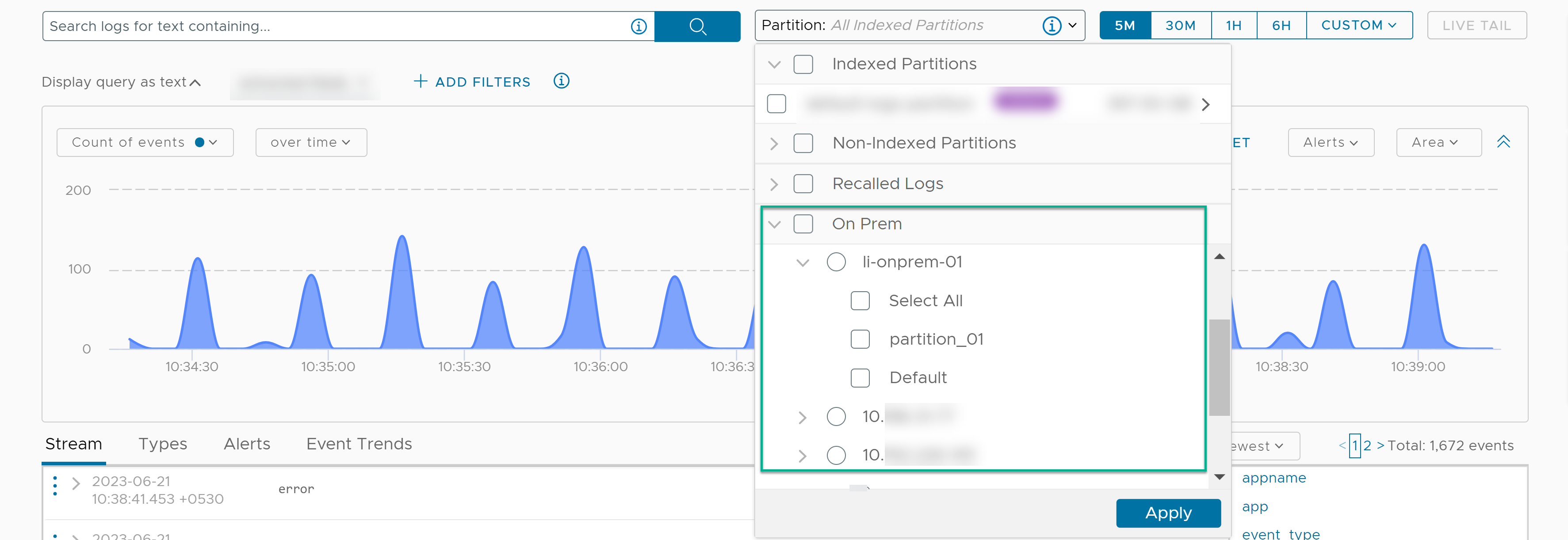
- Select one or more partitions to analyze logs in the partition.
You can select multiple partitions belonging to the same partition type, but you cannot select partitions belonging to different partition types. For example, you can select multiple non-indexed partitions. But you cannot select a recalled logs partition with a non-indexed partition.
Similarly, you can select one or more partitions from a single VMware Aria Operations for Logs cluster. You cannot select partitions belonging to different VMware Aria Operations for Logs clusters.
 For more information, see:
For more information, see: - Select a time range to find events within the range. Time ranges are inclusive when filtering.
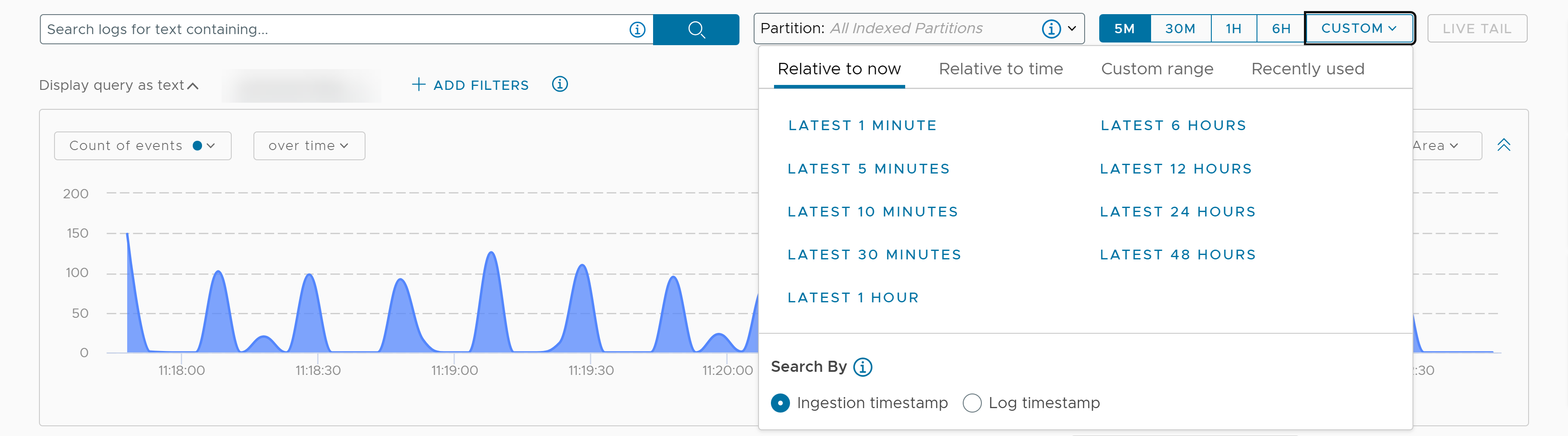
When you pick a time range, click CUSTOM and select either of the following options:
- Ingestion timestamp: This is the default option when you open the Explore Logs page. Selecting this option sets the time range filter based on the timestamp at which each log is ingested into VMware Aria Operations for Logs (SaaS).
For example, the current time is
2023:01:27 09:20:00. If you select Ingested timestamp and a time range of 5M (the last 5 minutes), the search results display logs ingested into VMware Aria Operations for Logs (SaaS) from2023:01:27 09:15:00to2023:01:27 09:20:00. - Log timestamp: Selecting this option sets the time range filter based on the timestamp parsed from the log payload. The log timestamp can differ from the ingestion timestamp, which is the time the log was ingested into VMware Aria Operations for Logs (SaaS).
For example, the current time is
2023:01:27 10:30:00. If you select Log timestamp and the time range as 30M (the last 30 minutes), the search results display logs that contain log timestamp values within the2023:01:27 10:00:00to2023:01:27 10:30:00range.Note: Querying by log timestamp is available only for logs in indexed partitions.
- Ingestion timestamp: This is the default option when you open the Explore Logs page. Selecting this option sets the time range filter based on the timestamp at which each log is ingested into VMware Aria Operations for Logs (SaaS).
- Search for log events that match certain values of specific fields. Using text in quotes in the main search text box matches exact phrases. Entering space in the main search text box is a logical AND operator. The search uses only full tokens. For example, searching for "err" does not find "error" as a match.
- Enter the search criteria using fields or filters.
Within a single filter, press Enter or Tab to separate filter values with an OR operator. For example, select hostname contains and type 127.0.0.1, press Enter, and type 127.0.0.2. The search returns events with the host name 127.0.0.1 or 127.0.0.2.
To separate filter values with an AND operator, you must add multiple filters. For example, add another filter by selecting the log_size field, selecting the > operator, and providing the filter value as 200. The search returns events with the host name 127.0.0.1 or 127.0.0.2. having the log_size greater than 200 bytes.
You can click the Display Query as Text option to view your query in text format and validate your inputs. For example, the text for this query is
hostname contains "127.0.0.1" or "127.0.0.2" AND log_size > 200.