On the
Security Planning page, when you click the wedge or the edge in the
Micro-Segments topology diagram, you can view the list of the services, flows, and recommended firewall rules for that particular segment. Click
Recommended Firewall Rules to view the rules defined on it. The members of the source or the destination are listed under the following types of rules:
- Physical to Physical: This tab lists all the rules associated with the physical and Internet IPs. The rules can be for physical-physical, physical-Internet, Internet-physical, or Internet-Internet entities.
- Virtual: This tab lists all rules where at least one of the endpoints is a VM.
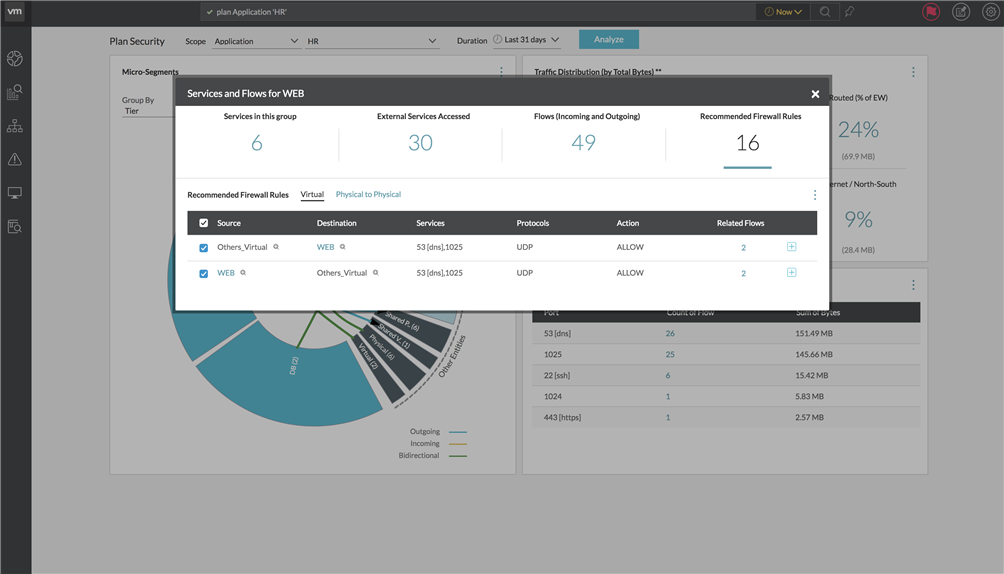
For each firewall rule, the following details are available:
- Show members of the group: Click the
+sign next to the name of the entity to see the members of the group.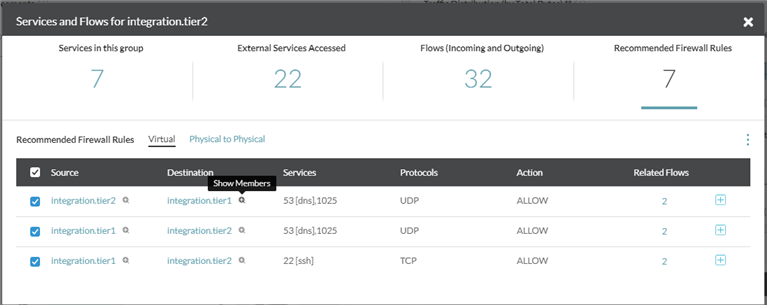 Note:
Note:- The members are not shown for the groups belonging to the Internet category.
- If a security group has both virtual and physical IPs, the physical and the Internet IPs are not shown in the list of the members of that particular group.
- The member Kubernetes services are shown under the Kubernetes Services tab.
- If the member count or the entry is zero for Virtual Machine, Physical & Internet IPs, or Kubernetes Services the tab is not visible.
- Source
- Destination
- Services
- Protocols
- Action
- Related Flows: Click the number of the related flows to see the list of flows with the corresponding flow information.
- View Applied Firewall Rules: Click the
+sign next to the Related Flows column to view the applied firewall rules corresponding to the similar sets of flows.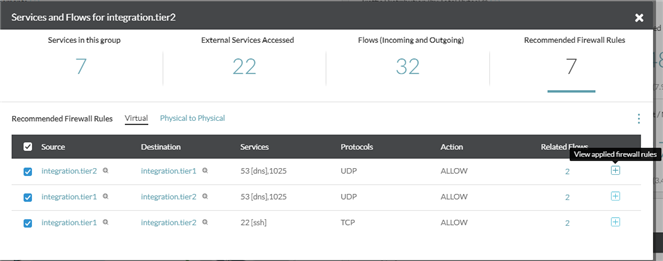
You can export the recommended rules as XML or CSV based on your requirement.
Note: You can export recommended rules related to Kubernetes objects in the YAML format also.
Refer to
Exporting Rules for more information on these artifacts.
Recommended Firewall Rule to Secure Vulnerable OS
Use the following procedure to get recommended firewall rule to secure vulnerable OS:
- Go to .
- In the Add Application page, do the following actions:
Options Actions Application Name Type a name for the Application Tier / Deployment - Provide a unique name for the tier.
- In the Member drop-down, select Custom VM Search and in the Search your application environment text box add the following condition:
in the qualifier put the matching criteria as: Operating System like 'Microsoft Windows Server 2003' or Operating System like 'Microsoft Windows Server 2008' or Operating System like 'Red Hat Enterprise Linux 6' or Operating System like 'Red Hat Enterprise Linux 5' or Operating System like 'SUSE Linux Enterprise 10'
- Click Save.
- Go to .
- In the Scope drop-down, select Application and the name of application you created.
- In Duration drop-down, select Last 7 days.
- To get the recommended firewall rules, click Analyze