Internet Content Adaptation Protocol (ICAP) is a lightweight HTTP-like protocol to transport HTTP messages to third-party services. The server executes its transformation service on messages and sends back responses to the client, usually with modified messages.
For more information on ICAP, see RFC3507.
ICAP is supported for HTTP request processing through Avi Load Balancer. With the implementation of the ICAP client functionality within the NSX Advanced Load Balancer, the following use cases are supported:
Antivirus scanning - Using a third-party antivirus scan engine
Content sanitization - Using a third-party content sanitization service
Other request modification options using ICAP services, for example, URL filtering
Configuring NSX Advanced Load Balancer for ICAP
Avi Load Balancer as an ICAP client supports the following:
Preview functionality
Streaming of payload
Content rewrite
The following are the main configuration components for enabling ICAP for virtual service on an Avi Load Balancer:
Configuring an ICAP pool group
Configuring an ICAP profile (attached to the virtual service)
Configuring an HTTP Policy for the virtual service with the action set as Enable ICAP
Associating the ICAP profile to the virtual service
Configuring HTTP security policy for ICAP
Configuring ICAP Pool Group
Navigate to and create a pool group. Leave the field Fail Action under Pool Group Failure Settings blank.
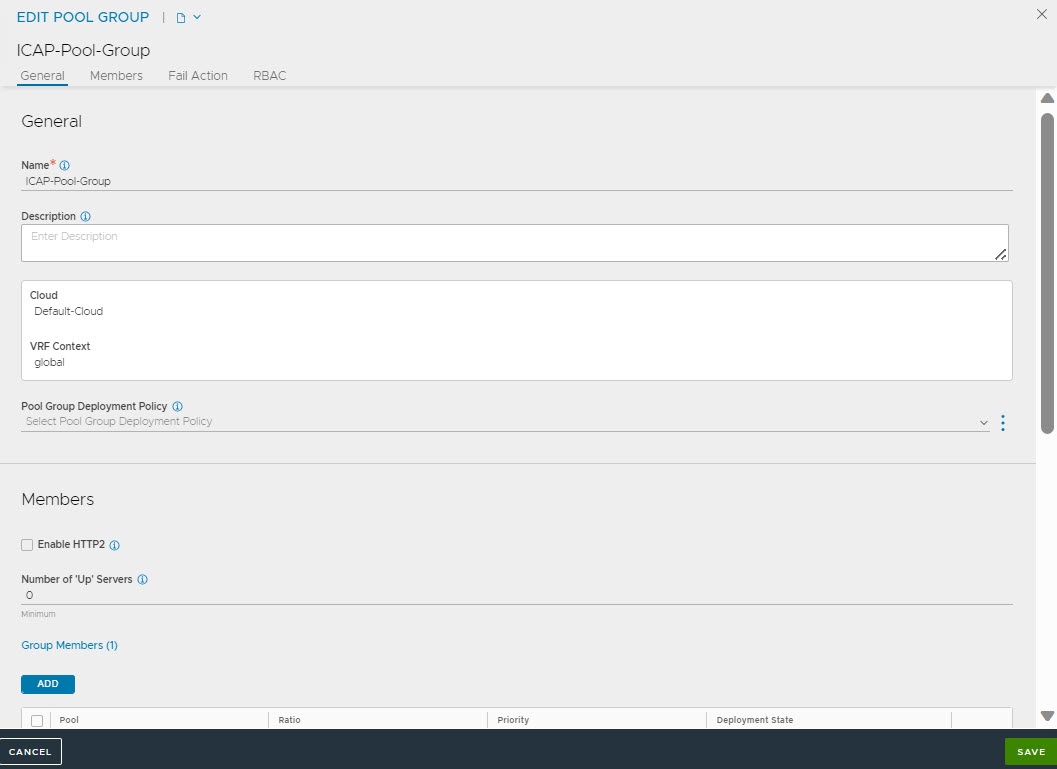
Configuring ICAP Pool
Navigate to create an ICAP pool. Configure the default port as 1344. Multiple Servers can be added as Pool members.
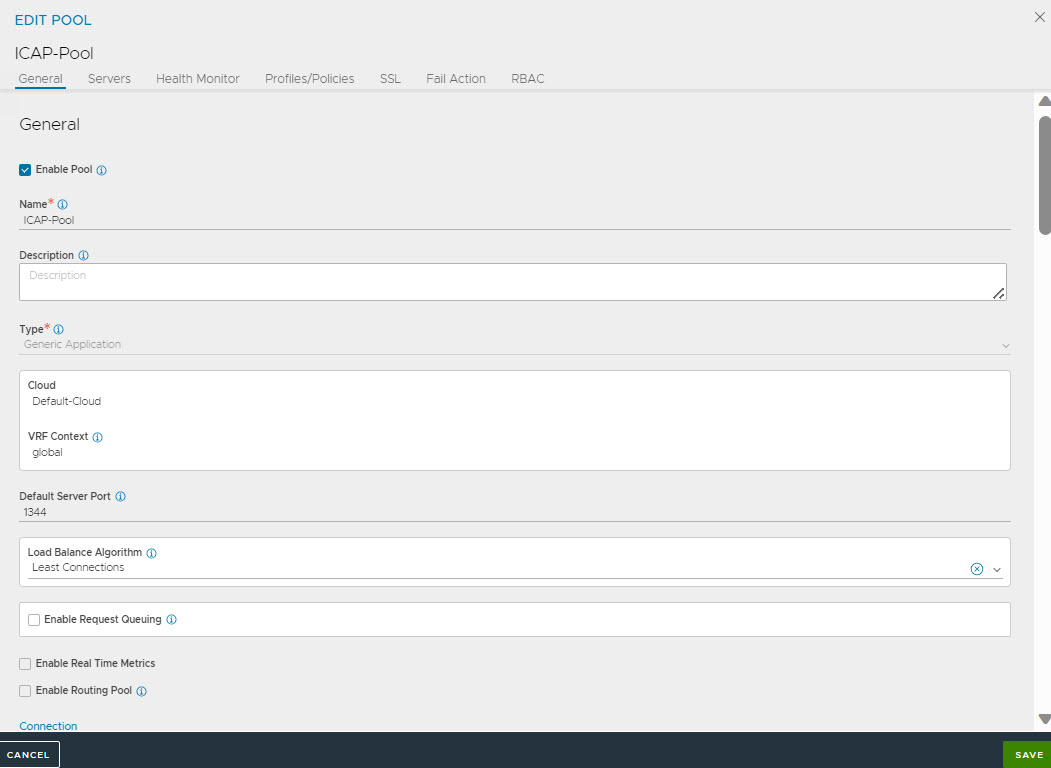
Configuring ICAP Profile
Refer to the following table for the various attributes used in the ICAP profile configuration:Configuration Item
Description
Example
Name
Name of this profile
ICAP-APPX
Cloud
Specifies which cloud object this is associated with
Default-Cloud
Pool Group
Pool group of all ICAP server pools
ICAP-Pool-Group
Vendor
Vendor specific configuration if a vendor is supported
OPSWAT
Generic-ICAP
Service URL
ICAP Server service URL
When using OPSWAT: /OMSScanReq-AV
Request Buffer Size
Maximum buffer size for request body
Default: 51200 (50 MB)
Enable ICAP Preview
Enable ICAP Preview functionality, where the ICAP server can make decisions by examining the preview size payload
Default: Enabled (Boolean)
Preview Size
Payload size for ICAP preview
Default: 5000 (5 MB)
Response Timeout
When this threshold is reached, the request will be handled as an error and the failure action will be executed
Default: 60000 (60 seconds)
Slow Response warning Threshold
When this threshold is reached, the request will cause a significant log entry, but will still be served
Default: 10000 (10 seconds)
Actions
Description
Example
Failure Action
Handling of error with ICAP server. If failed closed, a 503 will be sent if an error is occurring.
Fail Closed/ Fail Open
Large Upload Failure Action
Handling of size exceeded error. If fail closed, error 413 will be sent.
Fail Closed/ Fail Open
Navigate to to create an ICAP profile.
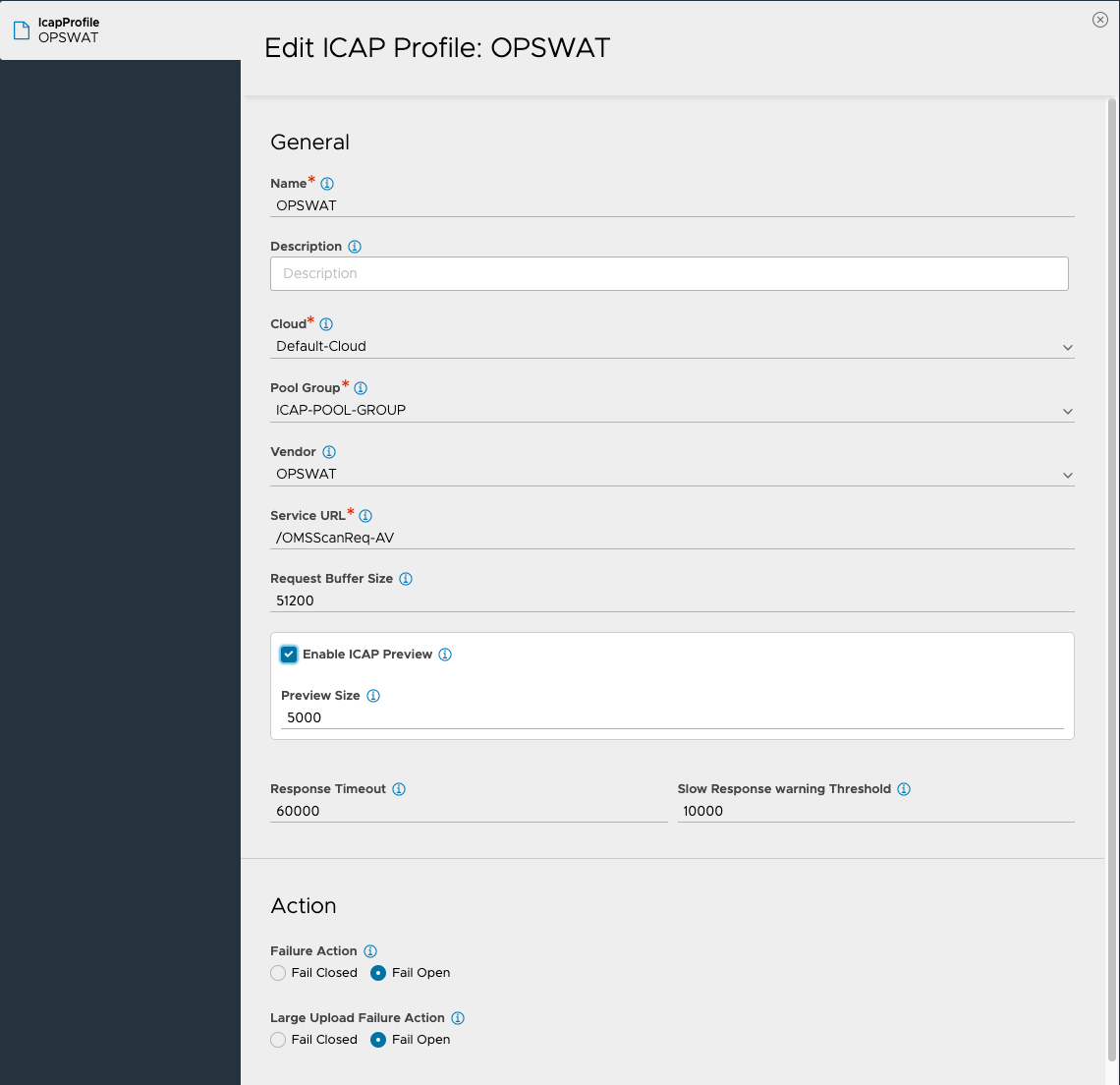
Navigate to the , select the required virtual service, and select the ICAP profile (created in the previous step).
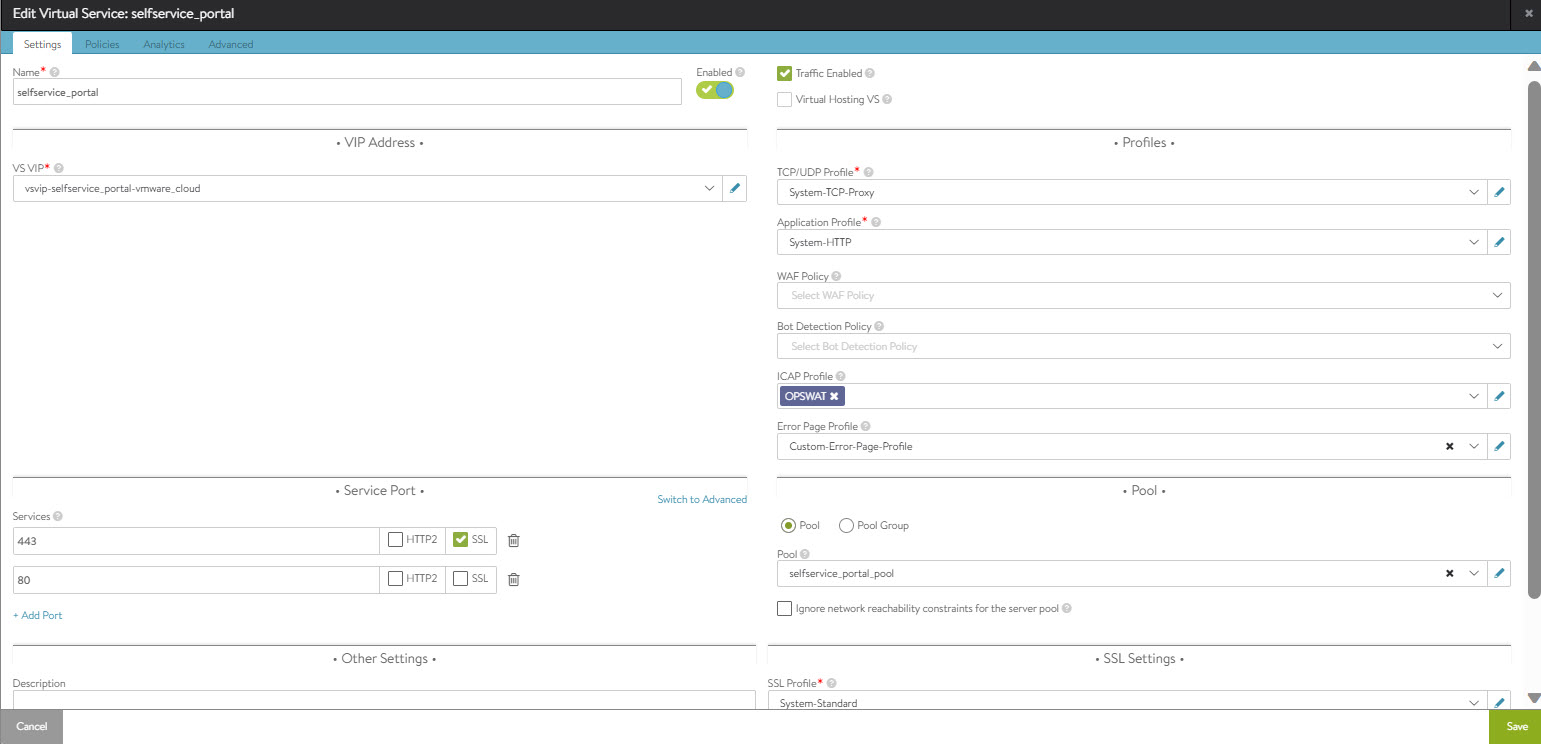
Creating HTTP Security Policy
Create a security policy to define the rules based on which the ICAP scanning must be performed. Navigate to , select the desired virtual service, and click Edit. Select , and create a new rule with the following options:
Select match criteria for the ICAP requests
Select Enable ICAP as the action
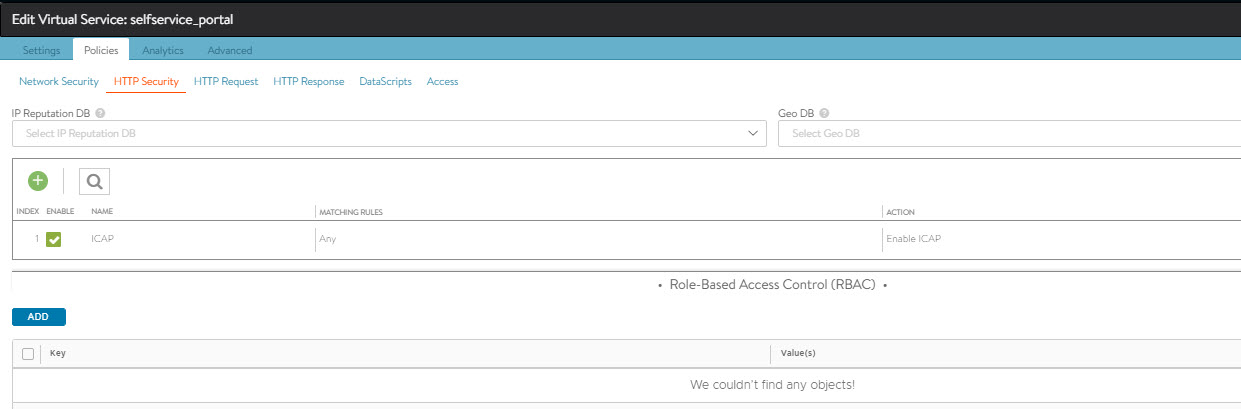
Note:The rule name configured in this step will appear in the logs. Make it self-explanatory for ease of troubleshooting.
Save the virtual service configuration.
With these steps, the ICAP configuration for the virtual service is complete. Incoming requests on the virtual service that match the rule or the match criteria of the HTTP security policy will use ICAP.
Avi Load Balancer supports the following ICAP servers (Third-party AV-Malware/CDR vendors):
MetaDefender ICAP Server (with MetaDefender Core)
To set up an OPSWAT server for ICAP scanning, see OPSWAT documentation.
Limitations
The following are the limitations for ICAP support on Avi Load Balancer:
ICAP is not supported for HTTP/2 virtual services.
ICAP client does not work in the response context.