This section covers the following features:
Visibility and Analytics
Log Settings
Visibility and Analytics
Navigate to and click the name of a virtual service configured for DNS. For instance, DNS-Site-US-East.
The Analytics tab displays the required metrics.
The Logs tab provides detailed information about DNS queries from clients, including FQDN, query-type, significant errors, responses such as IP addresses, CNAME, SRV, and so on.
Log Settings
Select the options available as per the requirement in the Log Analytics selector, as shown in the example below:
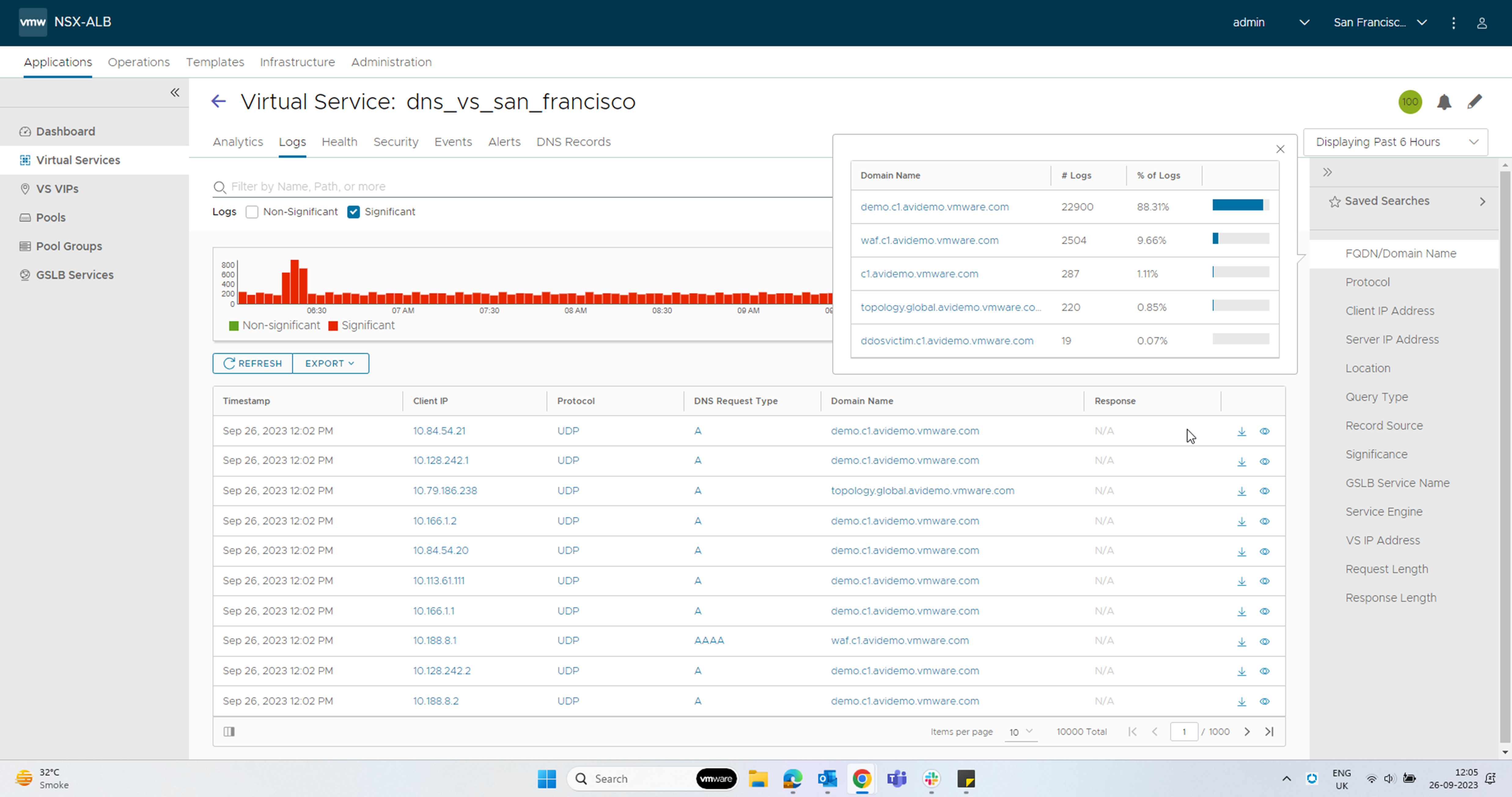
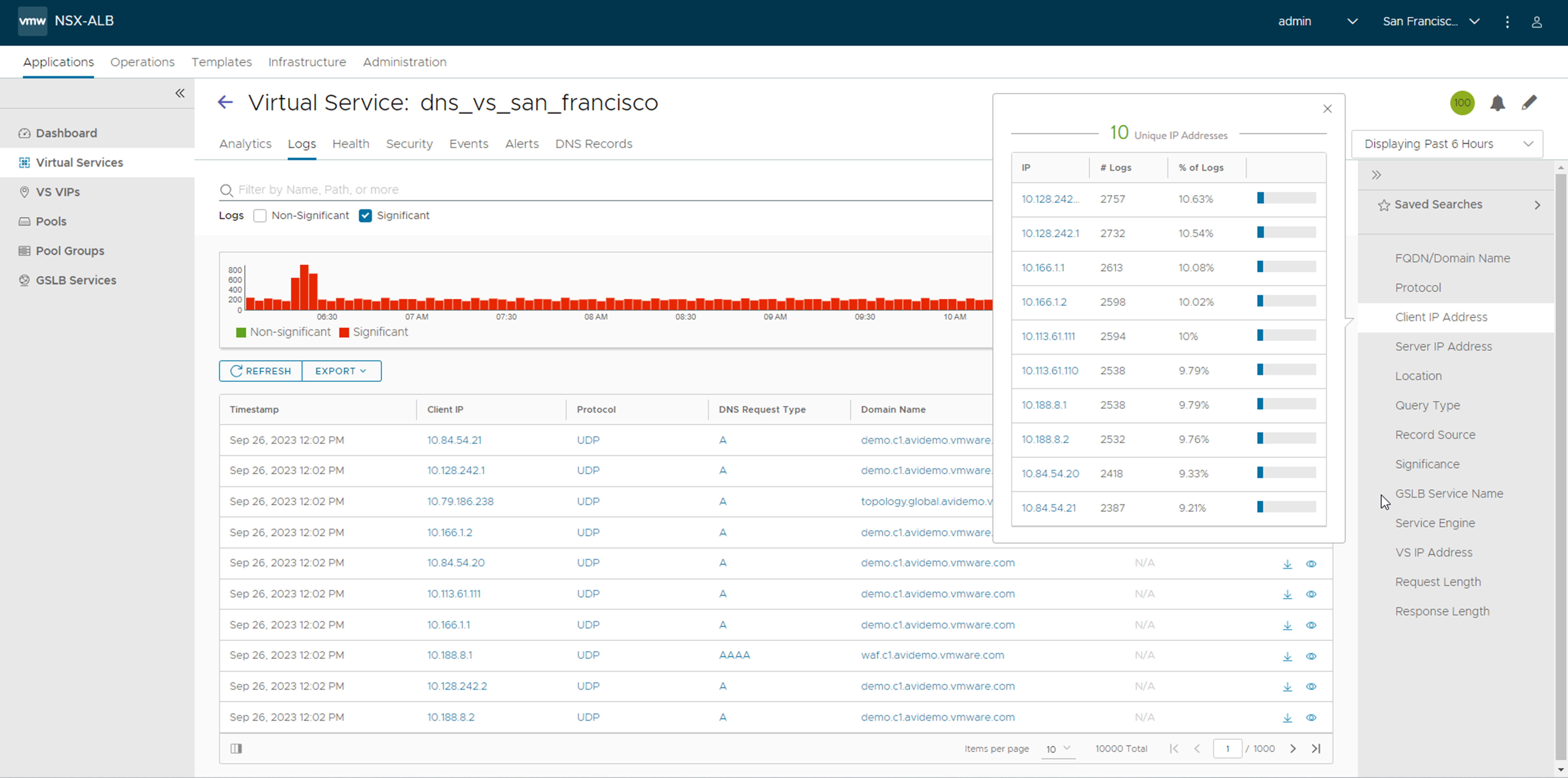
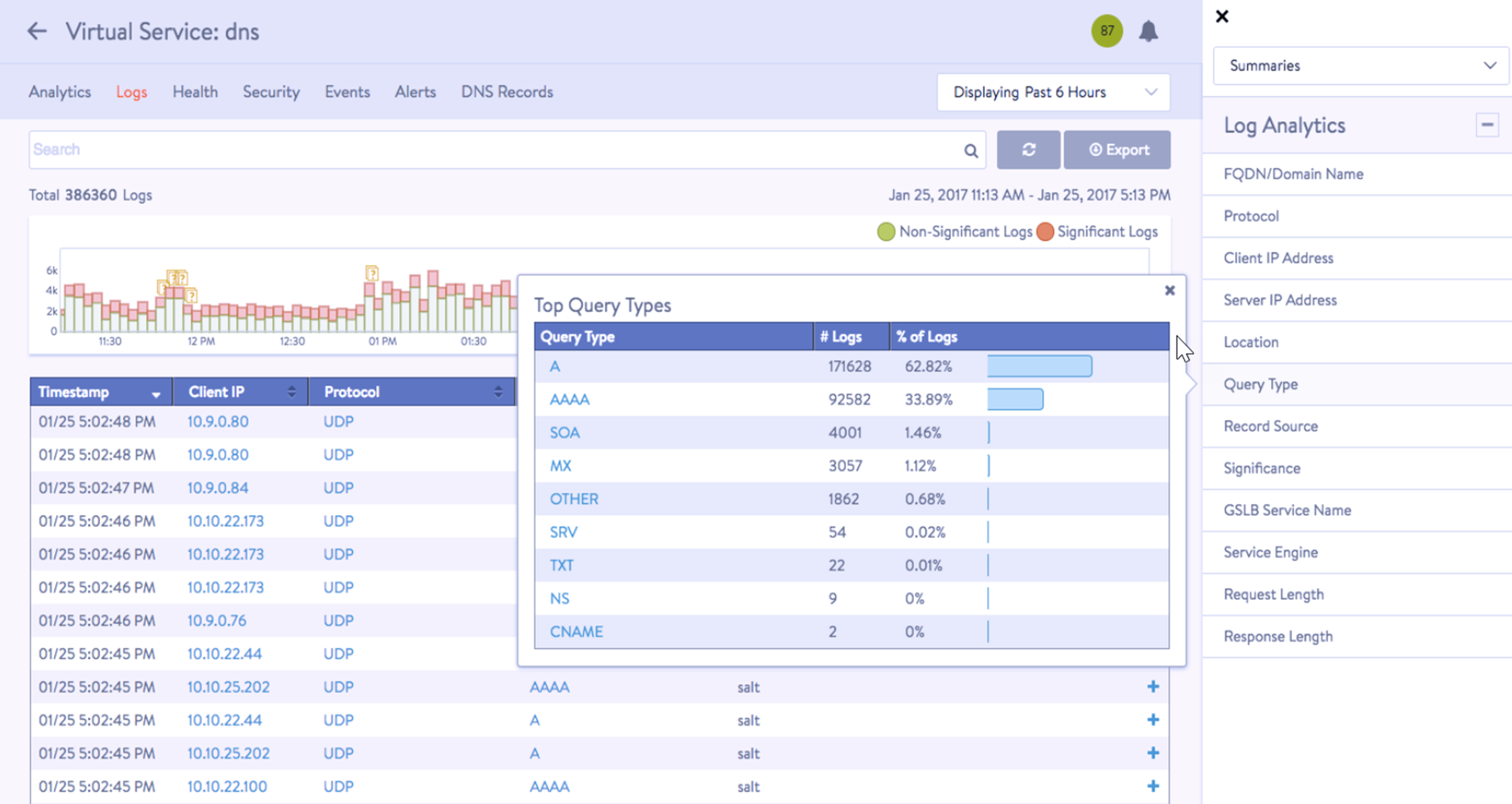
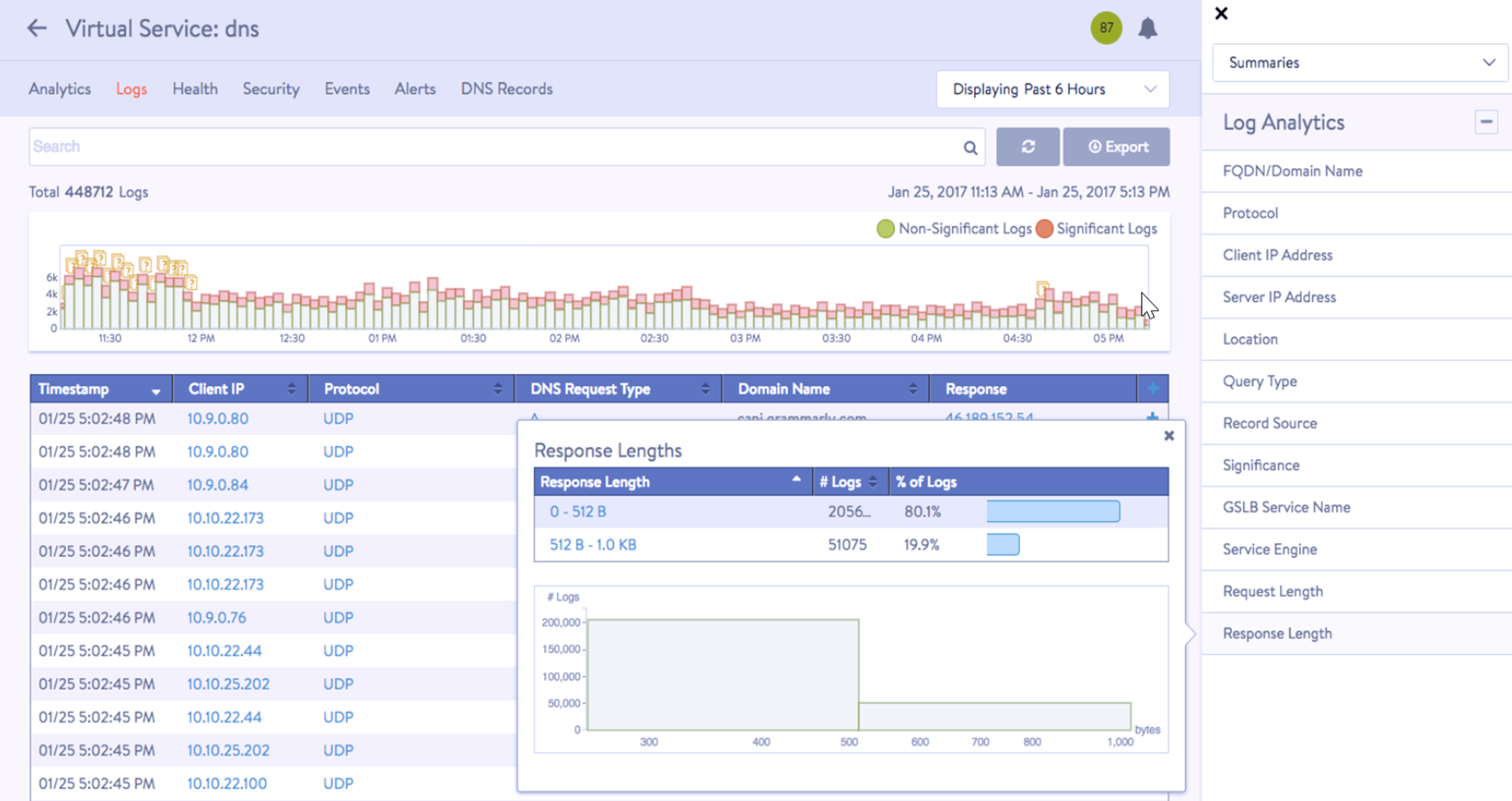
Non-significant logging is not recommended, since a DNS service usually receives a large number of DNS requests, resulting in an excessive number of log entries.
Categorization of non-significant logs is also very important.
If certain errors are typical in a certain deployment, these errors must be excluded from significant logs.
Subdomain names can be used to filter DNS requests.
NO DATA can occasionally appear when a metric tile is selected indicating the status as “Not Applicable”. For instance, a GSLB service name may not be applicable for the DNS proxy or a static entry.
The DNS Records tab is unique to this kind of virtual service.
Starting with Avi Load Balancer 22.1.3, the option to search DNS records for a DNS virtual service is available on Avi Load Balancer UI. This option is useful when there are multiple records, and it becomes difficult to find the specific entry to check if it is registered and receiving requests.
Additional Information
Any domains that are not explicitly configured on the DNS service are dropped through domain filtering (The default setting is to allow all domains).
Time-to-live (TTL) can be customized (Default is 30 seconds).
Network security policy can be based on client (source) IP and port.
With full TCP proxy, client spoofing is prevented for TCP DNS queries. SYN flood attacks are mitigated.
You can respond to failed DNS requests by returning a DNS error code or dropping the packets.