This section explains the steps to enable the Disk Encryption option for the SEs.
Limitations:
Only softand hard RSA keys of size 2080 are supported. For more information, refer to Azure Key Management Table.
All resources related to the customer-managed keys (Azure Key Vaults, disk encryption sets, VMs, disks, and snapshots) must be in the same subscription and region.
Disks, snapshots, and images encrypted with customer-managed keys cannot move to another subscription.
Configuring Microsoft Azure
To configure the key vault and Setting up your Azure Key Vault and DiskEncryptionSet, follow the steps from step 1 to 4 of Server-side encryption of Azure Disk Storage.
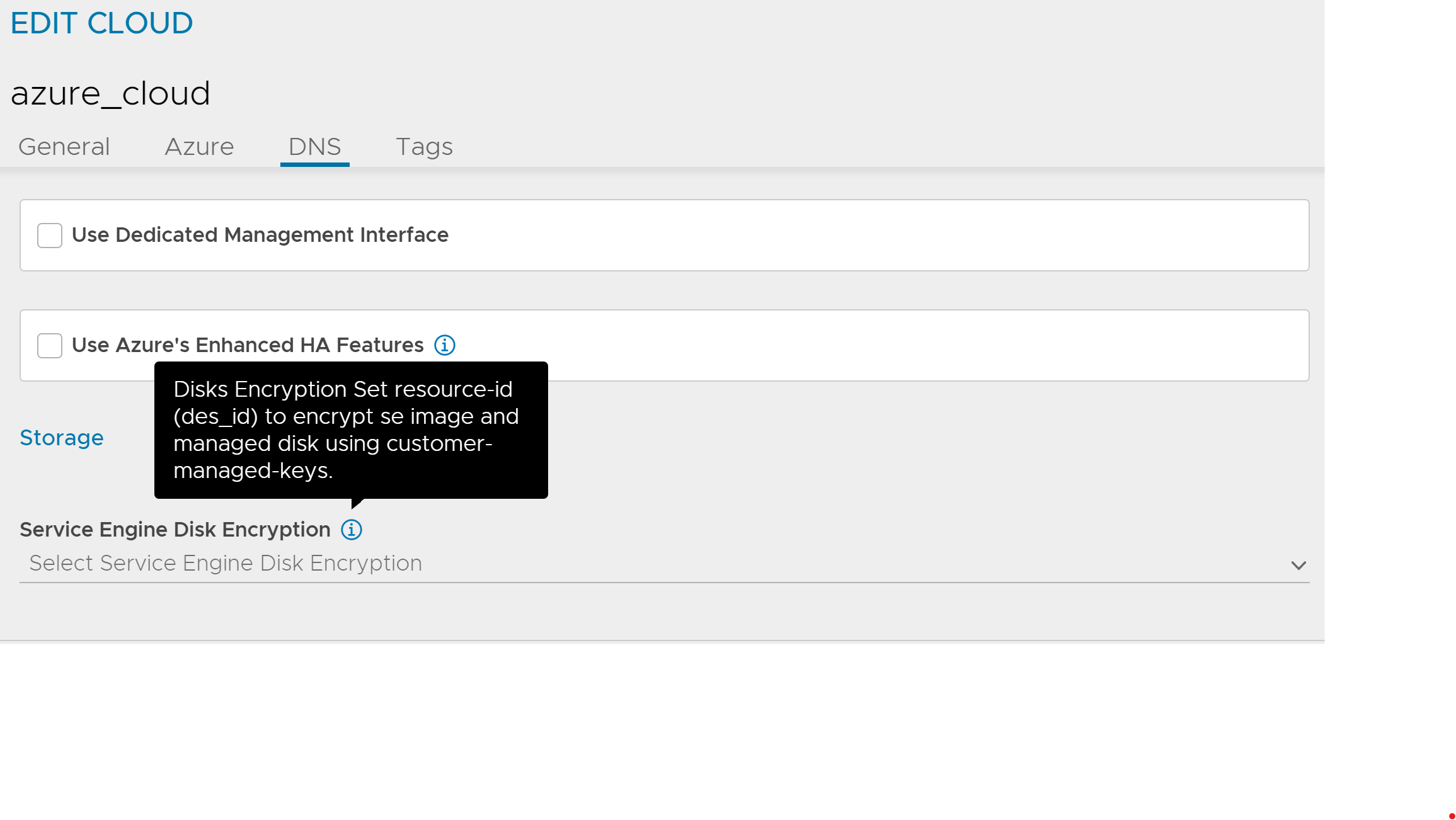
Configuring Avi Load Balancer for Disk Encryption
The Disk Encryption Set option is available on the Avi Load Balancer UI to select DES ID.
Navigate to and use the drop-down menu to select the DES ID as shown below:
Configuring Disk Encryption using the CLI
Server-side managed disk encryption with customer-managed keys allows the Controller to create encrypted SE Images and create SEs with encryption on OS and Azure Managed disk only.
The des_id option available under the cloud configuration mode uses the DES resource ID as the input for Azure cloud configuration.
[admin:controller]: > configure cloud Default-Cloud [admin:controller]: cloud> azure_configuration [admin:controller]: cloud:azure_configuration> des_id /subscriptions/0eebbbed-14c0-462e-99e0-daaaaaaaaa9/resourceGroups/avi-resource-group/providers/Microsoft.Compute/diskEncryptionSets/DESavi [admin:controller]: cloud:azure_configuration> save [admin:controller]: cloud> save
SE images, SEs with encrypted OS, and Azure Managed disk have the same DES ID.
Different DES IDs are not supported among SE VMs or Image and SE VMs.