This section explains the steps to create Avi Load Balancer cloud of type Google Cloud Platform (GCP). It spawns the Service Engines in the configured GCP project, zone, and VPC. The Service Engines will start load balancing the workloads in GCP.
To create the Avi Load Balancer cloud of type GCP,
Log in to the Controller using your credentials.
From the Avi Load Balancer UI, navigate to .
-
Click Create and select Google Cloud Platform from the dropdown.
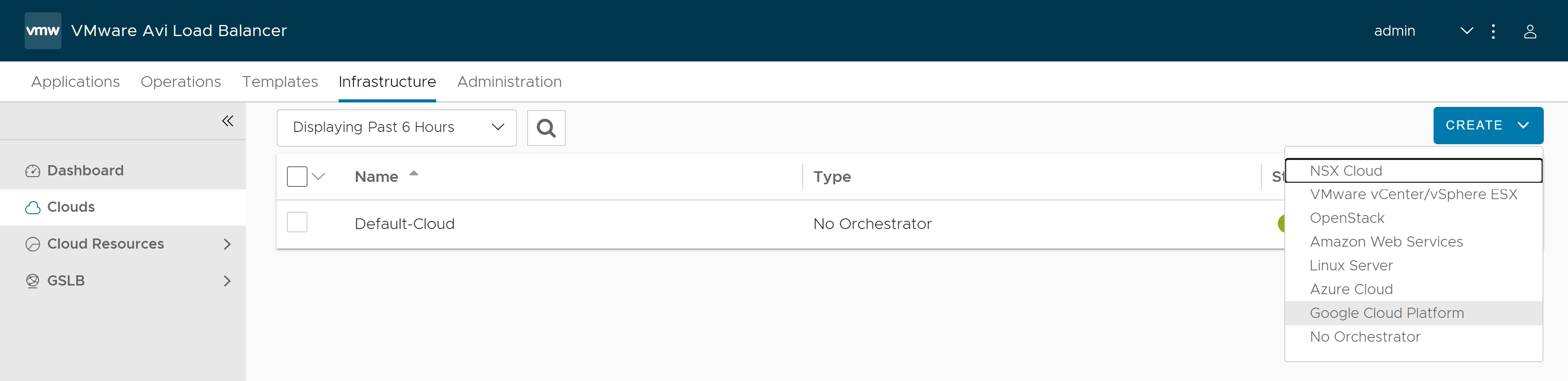
Configure the details under the General tab.
Enter a Name for the cloud.
Enter the Object Name Prefix which will be added to all the objects created under this cloud.
Under Management Network, Enable IPv4 is selected by default to Enable IPv4 on the Management Interface of the Service Engine.

Under the GCP tab, configure the Credentials for GCP API access.
Under the GCP tab, click SET CREDENTIALS.
In the GCP Credentials screen,
Enter the Service Engine Project ID. This is the Project ID from the GCP console. This is where the Service Engines will be created.
To Configure API access,
If the Controller is running in GCP and a service account is attached to the Avi Controller VM, then select Compute Account as Defalult Service Account.
If the Controller is outside GCP (in some other public/private cloud) or there is no GCP service account attached to the Avi Controller VM, then add a user with GCP service account JSON key in Avi Load Balancer as discussed:
If the CREDENTIALS object is created, select it or click the three ellipses are the right-corner of the Credentials field and click Create. In the NEW USER CREDENTIALS screen, perform one of the following steps:
In the NEW USER CREDENTIALS screen, select the Credentials Type as GCP.
-
click IMPORT File and select the file to upload or copy the Service Account Key and paste it in the text box provided.
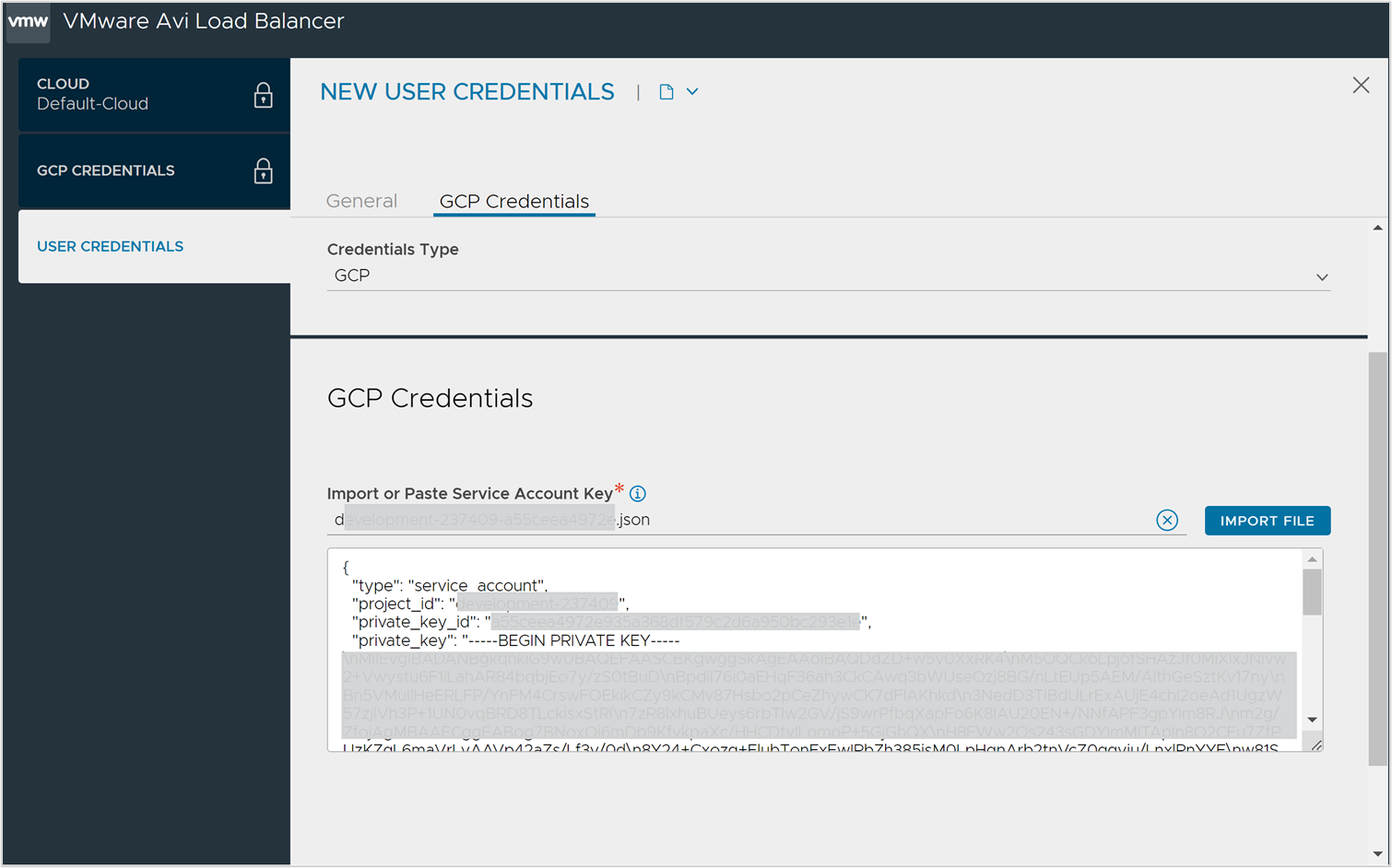
Click Save. The new credential is selected under Credentials.
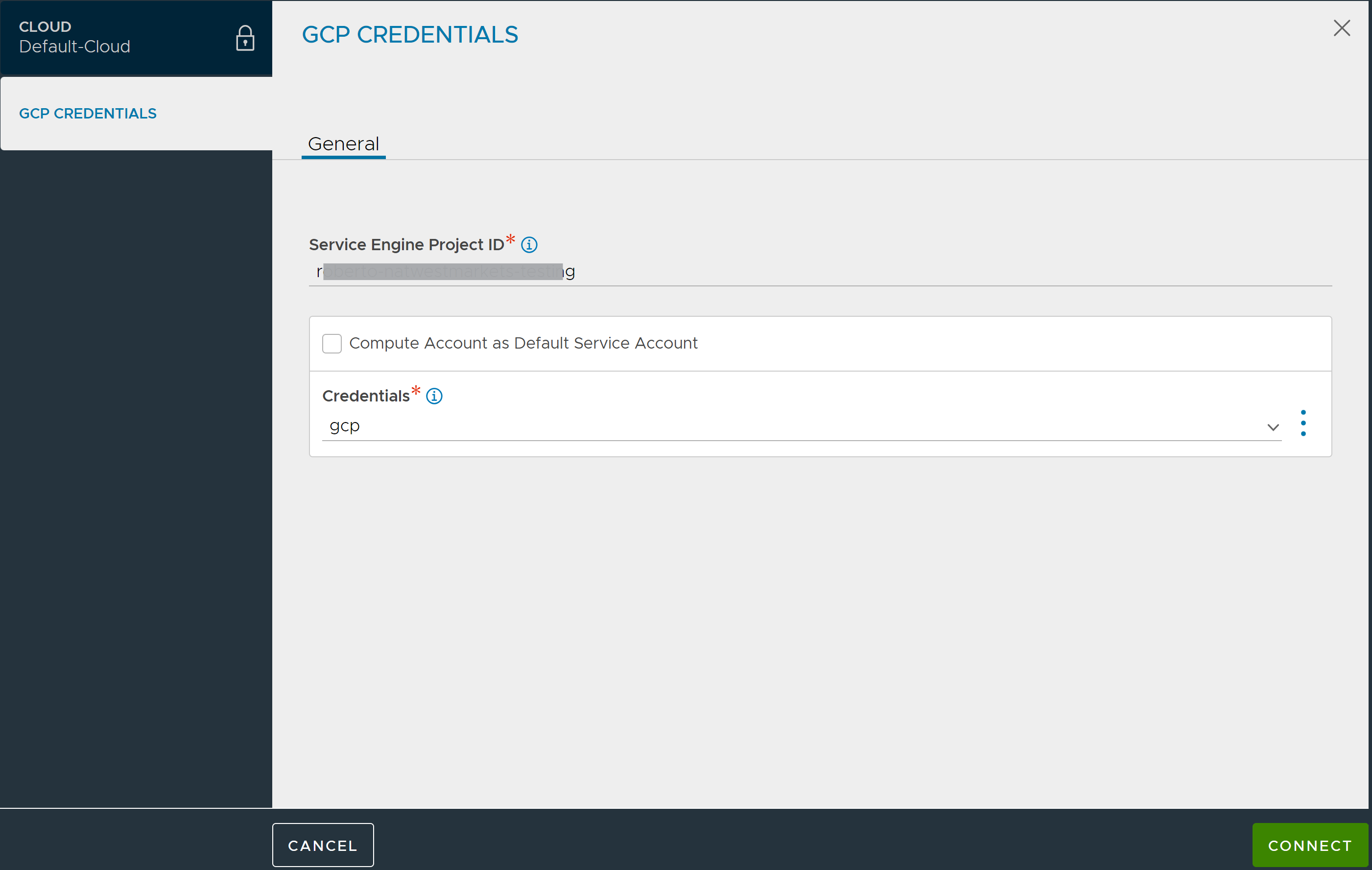
Click CONNECT.
Under Regions & Zones, configure the following:
Select the GCP Service Engine Region where the Service Engine will be deployed.
Select the Availiability Zones from the selected region. The Service Engines will be distributed among the selected zones.
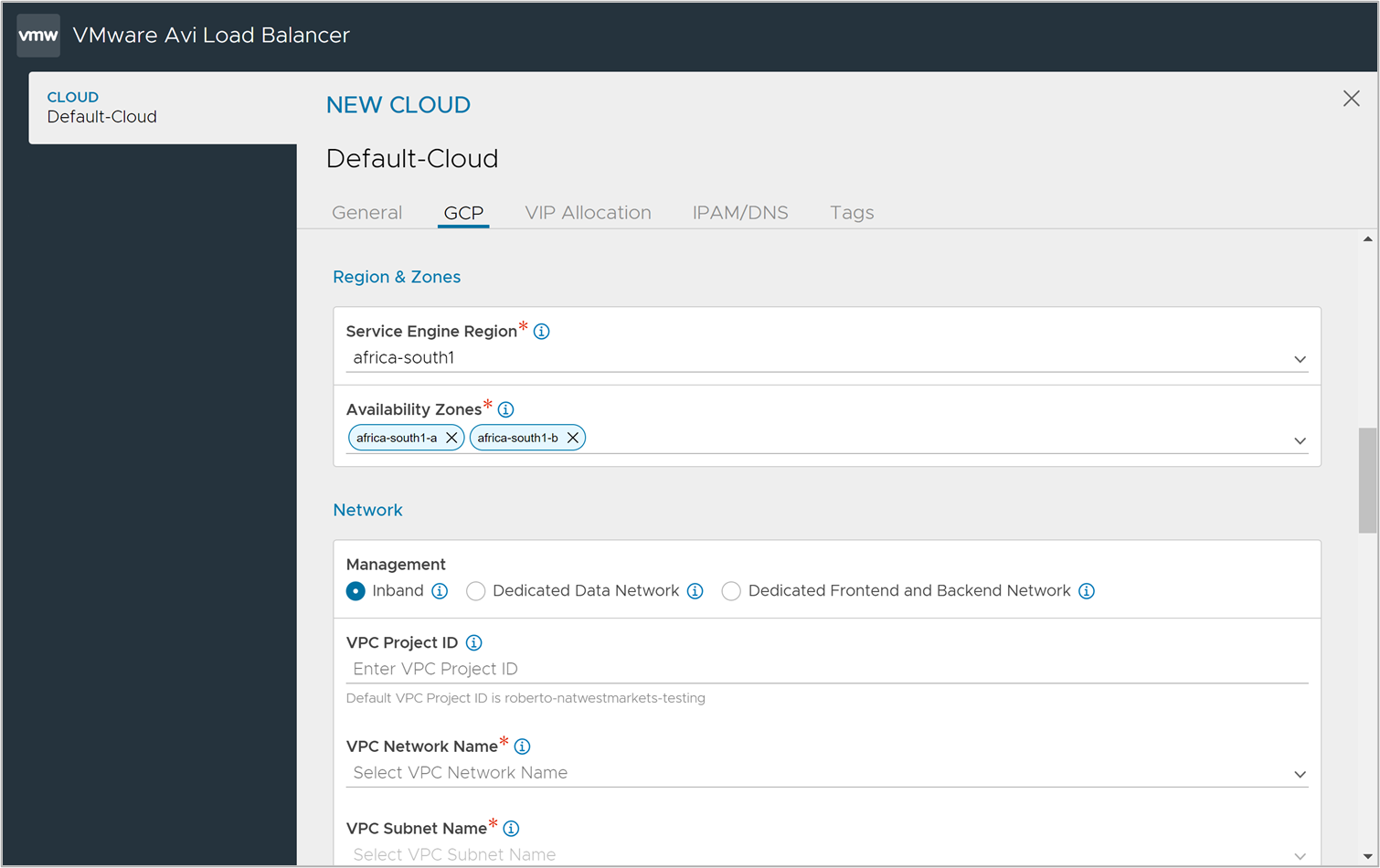
Note:It is recommended to have more than one zone for Service Engine High Availability.
Under Network, select and configure the required Network Configuration Mode.
Select firewall Target Tags to be applied on the Service Engine virtual machines to allow the ingress and egress traffic to the Controller, other Service Engines, and virtual services.
Under Storage, the Cloud Storage ID corresponding to the Service Engine project is selected by default. Enter the Cloud Storage Bucket Name, where the Service Engine image will be uploaded.
Note:Cloud Storage Bucket Name is required only in the cases where the service account does not have the permissions to create a bucket in the Google Storage Project.
If the service account has permissions to create the bucket in the Google storage project as described in the Authentication section, the NSX Advanced Load Balancer creates the bucket while creating the SE image in GCP and deletes the bucket once the image is created.
Under Encryption Keys, configure the Customer Managed Encryption Keys (CMEK) for different resources.
Service Engine Image Encryption Key ID: CMEK Resource ID to encrypt Service Engine GCE Image.
Service Engine Disk Encryption Key ID: CMEK Resource ID to encrypt Service Engine Disks.
GCS Bucket Encryption Key ID: CMEK Resource ID to encrypt Google Cloud Storage Bucket. This Bucket is used to upload Service Engine raw image.
GCS Objects Encryption Key ID: CMEK Resource ID to encrypt Service Engine raw image. The raw image is a Google Cloud Storage Object.
Configure the VIP Allocation Mode.
Under Management, choose one of the following VIP allocation modes:
Routes: The GCP routes for the VIP will be created in both the frontend data and backend data VPCs.
ILB: The VIP reachability is through the Internal Load Balancer (ILB), where VIP is allocated from a GCP subnet and the VIP will be frontend IP of the ILB.
Click Enable Subnet Routes to match the SE group subnets for VIP Placement.
Configure the IPAM/ DNS Profile.
Select an IPAM Profile for the cloud to allocate VIP from the Avi Load Balancer internal network.
Select a DNS Profile for the cloud, if required.
Create custom, cloud-level Tags for easier resource management.
Click Add.
Enter the Key and Value pairs.
Click Save.
On saving the cloud configuration, the GCP cloud is available as shown below:

The Controller validates the configuration and starts creating the Service Engine image in the SE project. After the image is successfully uploaded, the NSX Advanced Load Balancer cloud becomes ready for virtual service creation.