This section details the steps for configuring the WAF Profile.
Navigate to to locate the default profile.
There are two default WAF Profiles available:
System-WAF-Profile
Default for web applications
Contains standard settings for any WAF virtual service
System-WAF-Profile-API
Default for API traffic.
Focus on traffic that is JSON or XML.
Expands default settings to cover most API-centric use cases.
For customizing a profile, it is recommended to create a new profile instead of editing the default profile
System-WAF-ProfileorSystem-WAF-Profile-API.
To create a new profile.
Navigate to .
Click Create.
Configure the new WAF Profile under the following tabs:
General
Default Actions
Content Type Mapping
Files
Click Save.
General
The General section in the Create WAF Profile screen is as shown below.
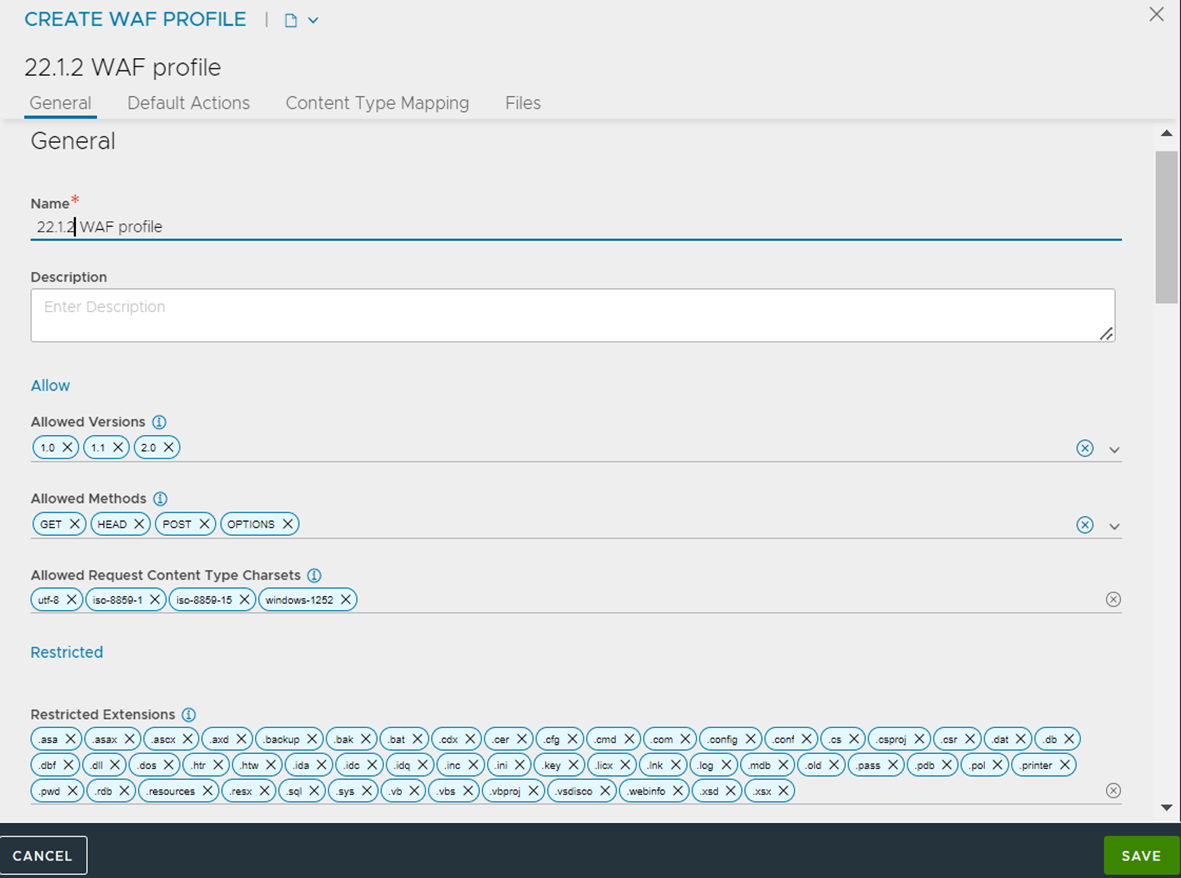
Provide the following details to configure the WAF Profile.
Field |
Description |
Additional Information |
|---|---|---|
Name |
Enter a relevant name for the profile. |
|
Allowed Versions |
Enter the allowed HTTP versions for the profile. |
1.0, 1.1 and 2.0 are the default entries. |
Allowed Methods |
Enter the allowed HTTP method for the profile. Different applications might need different methods. |
Websites might use only the default HTTP methods that is, GET, HEAD, POST, OPTIONS. APIs can use other HTTP methods such as PUT, DELETE, PATCH, TRACE, CONNECT and so on. You can also choose from the following additional options:
|
Allowed Request Content Type Charsets |
Enter the accepted request content types for the profile. By default, all standard content types are covered. |
Defaults character sets are utf-8, iso8859-1, iso8859-15, and windows-1252. You can directly add or update desired character sets in WAF Profile without configuring any pre-CRS rules. |
Restricted Extensions |
Enter extensions that must be restricted and blocked. |
Generally, these are files that do not reside on a web server. |
Restricted Headers |
Enter headers that will not be allowed by WAF. |
|
Static Extensions |
Enter the list of static file extensions that will bypass the WAF check. |
A GET request without any parameter or dynamic part is classified as a static request. It does not contain any attack vector. |
Other Settings
Field |
Description |
Additional Information |
|---|---|---|
Maximum Client Request Size |
This is the maximum size for the client request body scanned by WAF. |
Example - 32 |
Maximum Backend Response |
Enter the maximum response size in KB allowed by WAF. |
Example - 128 |
Regex Match Limit |
This is the Limit for CPU utilization for each regular expression match when the processing rules. |
Example - 30000 |
Regex Recursion Limit |
Limit depth of recursion for each regular expression match when processing rules. |
|
Max Execution Time |
This is the maximum time allowed for WAF processing for a single request. |
Example - 50. |
Argument Separator |
Enter the separator for special applications that have different argument separators. |
Example - &. |
Cookie Format Version |
Select the preferred cookie format version. |
|
Ignore Request Body Parsing Errors due to partial Scanning |
Select to ignore request body parsing errors due to partial scanning. |
|
Enable XXE Protection |
Block or flag XML requests referring to External Entities. |
Select or deselect the check box. |
Default Actions Tab
Each phase has a default action. The fields defined for the default action are phase, action, status code, additional logging and WAF logs.
The value of default action takes the following format:
<phase:n>, <action>, <status code>, <additional-log-level>, <WAF-log-level>
<phase>: The following is the list of WAF phases and the allowed values for the phase:
Request Header Phase - phase:1
Request Body Phase - phase:2
Response Header Phase - phase:3
Response Body Phase - phase:4
<action>: Two options for action are pass and deny.
<status code>: If the request is denied by WAF, by default a 403 status code is sent to the client. The status code can also be customized (if required). For example, 403.
<additional-log-level>: The additional logging level. For example, log.
<WAF-log-level>: The WAF logging level. For example, auditlog.
The following is an example of a default action for theRequest Header Phase.
phase:1,deny,status:403,log,auditlog
Content Type Mapping Tab
This tab is used to configure the accepted request content types for the profile.
For more information on content-type mapping and available request body parsers, see Content-Type Mapping in WAF Profile.
Files Tab
The static input data in a WAF Profile that is shared between virtual services is stored here. For example, the file name sql-errors.data has the default data set which contains strings for examining HTTP responses for data leakage protection.
To create a new file.
Navigate to the Files tab.
Click Add.
Provide a Name, Type, and enter the relevant Data.
The following file Types can be defined.
WAF pmFromFile operator data |
This is the default and it is used for files used by WafPolicies rules with an @pmf or @pmFromFile operator. |
DTD |
This defines an XML DTD file and it can be used by the WafPolicy @validateDTD operator. |
XSD |
This defines an XML schema file and it can be used by the WafPolicy @validateSchema operator. |
These files can be referred in the custom WAF Policy rules. For more information, see Custom Rules.