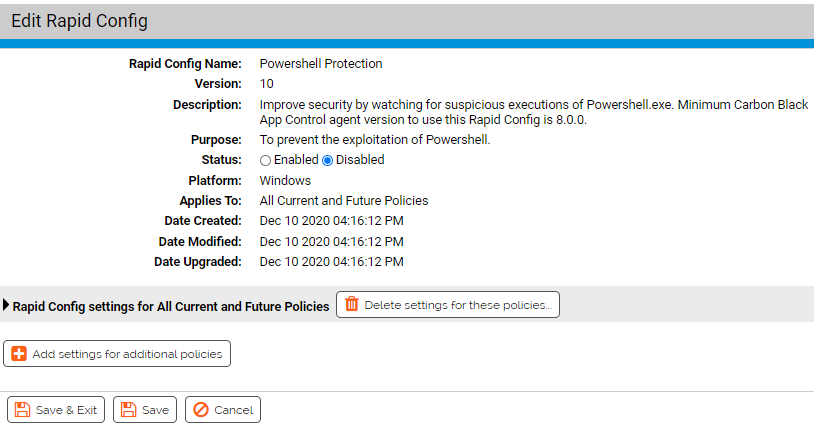
Purpose:To prevent the exploitation of Powershell.
Description: Improve security by watching for suspicious executions of Powershell.exe.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
Use Cases
<Add info>
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Invoke Expression
Use this group to protect against execution of powershell using the invoke-expression command line. Invoke-Expression is sometimes used by attackers to download and dynamically execute content.
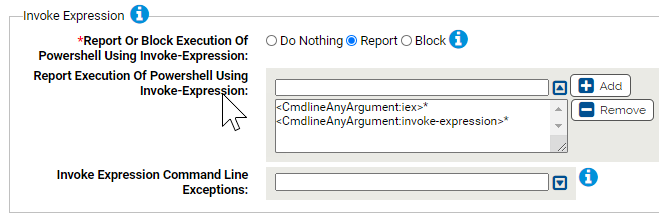
- *Report Or Block Execution Of Powershell Using Invoke-Expression:
- Should execution of powershell using invoke-expression be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell Using Invoke-Expression:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the list includes:
- Invoke Expression Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
Downloads
Use this group to protect against execution of powershell using the download commands to download malicious files.
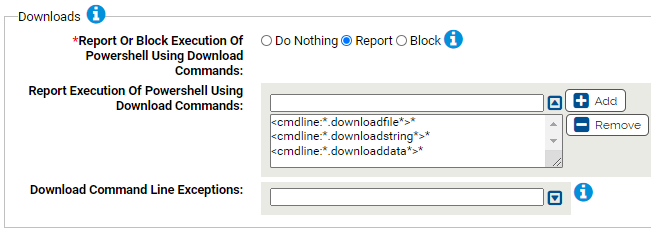
- *Report Or Block Execution Of Powershell Using Download Commands:
- Should execution of powershell using download commands be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell Using Download Commands:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the command list is as follows:
- Download Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
Execution Policy
Use this group to protect against powershell setting the ExecutionPolicy via the command line. The default policy is typically Restricted which only allows interactive powershell sessions and single command execution. Attackers can change the policy with the ExecutionPolicy parameter.
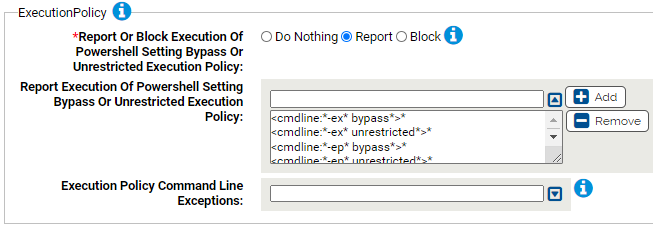
- *Report Or Block Execution Of Powershell Setting Bypass Or Unrestricted Execution Policy:
- Should execution of powershell with both the -hidden and -encoded parameters be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell Setting Bypass Or Unrestricted Execution Policy:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the following commands are listed:
- Execution Policy Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
Hidden and Encoded
Use this group to protect against powershell running in a hidden window and using an encoded command. Powershell attacks will often use the combination of encoded commands and hidden window styles to avoid detection.
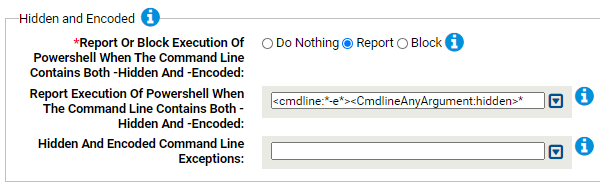
- *Report Or Block Execution Of Powershell When The Command Line Contains Both -Hidden And -Encoded:
- Should execution of powershell with both the -hidden and -encoded parameters be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell When The Command Line Contains Both -Hidden And -Encoded:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the following is listed: <cmdline:*-e*><CmdlineAnyArgument:hidden>*
- Hidden And Encoded Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
WindowStyle
Use this group to protect against execution of powershell using -WindowStyle Hidden or WindowStyle -Minimized parameters. This can avoid powershell being hidden or minimized while performing malicious tasks.
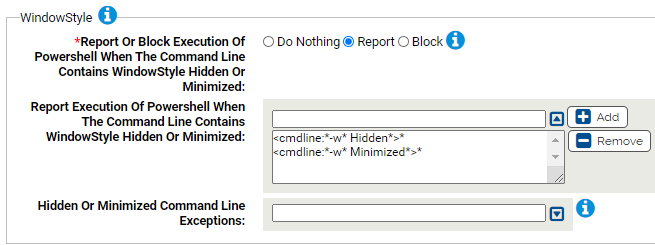
- *Report Or Block Execution Of Powershell When The Command Line Contains WindowStyle Hidden Or Minimized:
- Should execution of powershell with WindowStyle hidden or minimized be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell When The Command Line Contains WindowStyle Hidden Or Minimized:
-
Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the list includes:
- <cmdline:*-w* Hidden*>*
- <cmdline:*-w* Minimized*>*
- Hidden Or Minimized Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
NoProfile
Use this group to protect against execution of powershell using the -NoProfile parameter. This can avoid powershell being run without using the profile scripts that have been put in place.
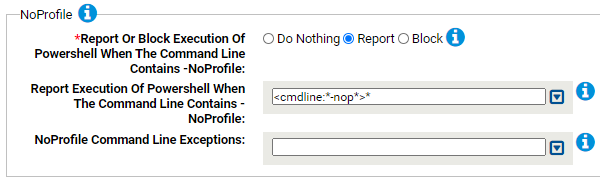
- *Report Or Block Execution Of Powershell When The Command Line Contains -NoProfile:
- Should execution of powershell with -NoProfile be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell When The Command Line Contains -NoProfile:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the following is listed:
- NoProfile Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
Downgrade Attacks
Use this group to protect against powershell downgrade attacks. Downgrade attacks are when the attacker attempts to use an older, more vulnerable version of Powershell.
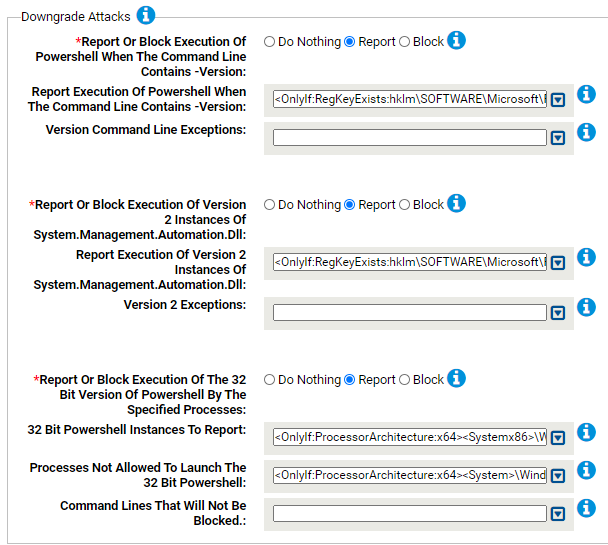
- *Report Or Block Execution Of Powershell When The Command Line Contains -Version:
- Should execution of powershell with -Version be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Powershell When The Command Line Contains -Version:
- Carbon Black App Control will report or block execution of powershell using these command lines. You can add or remove items from this list. By default, the following is listed:
- Version Command Line Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
- *Report Or Block Execution Of Version 2 Instances Of System.Management.Automation.Dll:
- Should execution of version 2 instances of system.management.automation.dll by powershell be reported or blocked? Carbon Black App Control will block loading the dll by terminating powershell. You should validate that legitimate execution is not blocked before enabling blocking.
- Report Execution Of Version 2 Instances Of System.Management.Automation.Dll:
- Carbon Black App Control will report or block execution of powershell running older versions of System.Management.Automation*.dll. You can add or remove items from this list. The following listed by default:
- Version 2 Exceptions:
- Command lines that will not be reported or blocked. You can add or remove items from this list.
- *Report Or Block Execution Of The 32 Bit Version Of Powershell By The Specified Processes:
- Should execution of the 32 bit version of powershell by the specified processes be reported or blocked? Specifically, execution of 32 bit Powershell by 64 bit Powershell can indicate a downgrade attack. You should validate that legitimate execution is not blocked before enabling blocking.
- 32 Bit Powershell Instances To Report:
- Carbon Black App Control will report or block execution of 32 bit powershell instances by the specified processes. By default, the following is listed:
- Processes Not Allowed To Launch The 32 Bit Powershell:
- Carbon Black App Control will report or block execution of 32 bit powershell instances by the specified processes. By default, the following is listed:
- Command Lines That Will Not Be Blocked:
- Command lines specified here will not be blocked when starting a 32 bit instance of powershell.exe.
Execution Policy Registry Settings
Use this group to protect against modification of Powershell Execution Policy registry settings

- *Report Or Block Registry Modification:
- Should modification of the specified Powershell registry settings be reported or blocked? You should validate that legitimate registry modifications are not blocked before enabling blocking.
- Report Registry Modification:
- Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. The default entry is:
- Processes Allowed To Modify The Specified Registry Settings:
- Processes specified here will be allowed to modify the specified registry settings. You can add or remove items from this list. The default entry is: