Purpose:To protect against attacks that use non standard script processors. For example, this can prevent an attacker from copying python.exe to a new location and using it to execute arbitrary scripts.
Description: Improves the security of computers by ensuring that script processors only run from expected locations.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |

Use Cases
<Add info>
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Command Processor
Use this group to report or block command processors run from non-default locations.

- *Report Or Block Execution Of Command Processors From Non-Default Locations:
- Should execution of command processors from non-default locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Command Processors:
- Execution of command processors specified here will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
Powershell
Use this group to report or block powershell run from non-default locations.
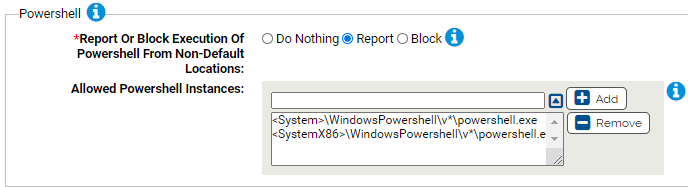
- *Report Or Block Execution Of Powershell From Non-Default Locations:
- Should execution of powershell from non-default locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Powershell Instances:
- Execution of these instances of powershell will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
Registry processors
Use this group to report or block registry processors run from non-default locations.
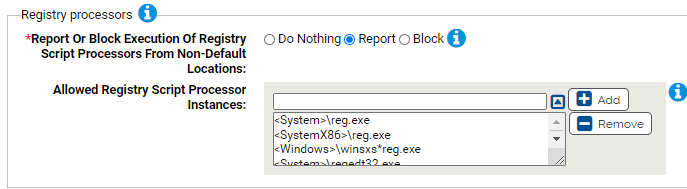
- *Report Or Block Execution Of Registry Script Processors From Non-Default Locations:
- Should execution of registry script processors from non-default locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Command Processors:
- Execution of these instances of registry script processors will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
VB Script processors
Use this group to report or block VB Script processors run from non-default locations.

- *Report Or Block Execution Of VB Script Processors From Non-Default Locations:
- Should execution of VB Script processors from non-default locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed VB ScriptProcessors:
- Execution of these instances of VB Script processors will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
Java Script processors
Use this group to report or block Java Script processors run from unexpected locations.

- *Report Or Block Execution Of Java Script Processors From Unexpected Locations:
- Should execution of Java Script processors from non-default unexpected be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Java Script Processors:
- Execution of these instances of Java Script processors will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
Perl Script processors
Use this group to report or block Perl Script processors run from unexpected locations.
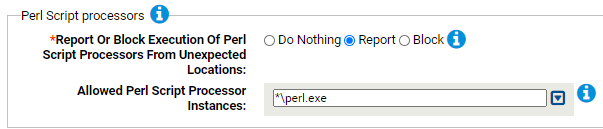
- *Report Or Block Execution Of Perl Script Processors From Unexpected Locations:
- Should execution of Perl Script processors from unexpected locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Perl Script Processors:
- Execution of these instances of Perl Script processors will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
Python Script processors
Use this group to report or block Python Script processors run from unexpected locations.

- *Report Or Block Execution Of Python Script Processors From Unexpected Locations:
- Should execution of Python Script processors from unexpected locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed Python Script Processors:
- Execution of theses instances of Python Script processors will not be blocked (if approved). You can add or remove items from this list. By default, the list includes:
HTML application processors
Use this group to report or block HTML application processors run from unexpected locations.
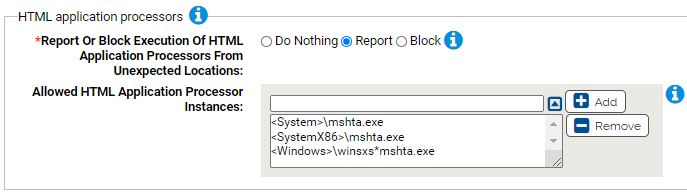
- *Report Or Block Execution Of HTML Application Processors From Unexpected Locations:
- Should execution of HTML Application processors from unexpected locations be reported or blocked? You should validate that legitimate executions are not blocked before enabling blocking.
- Allowed HTML Application Processors:
- Execution of these instances of HTML Application will not be blocked (if approved). You can add or remove items from this list. By default, the list includes: