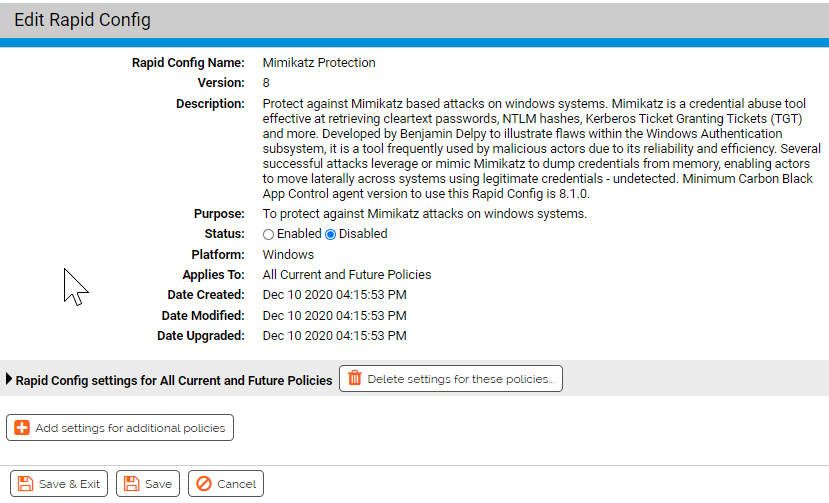
Purpose:To protect against Mimikatz attacks on windows systems.
Description: Protect against Mimikatz based attacks on windows systems. Mimikatz is a credential abuse tool effective at retrieving cleartext passwords, NTLM hashes, Kerberos Ticket Granting Tickets (TGT) and more. Developed by Benjamin Delpy to illustrate flaws within the Windows Authentication subsystem, it is a tool frequently used by malicious actors due to its reliability and efficiency. Several successful attacks leverage or mimic Mimikatz to dump credentials from memory, enabling actors to move laterally across systems using legitimate credentials - undetected.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.1.0 |
What is Mimikatz
Mimikatz started life as a GitHub project by Benjamin Delpy to illustrate flaws within the Windows Authentication subsystem. It is a tool that can extract plain text passwords, NTLM hashes, Kerberos Ticket Granting Tickets (TGT), and more from memory.
Malicious actors have leveraged this technology to infiltrate environments and move laterally across systems using legitimate credentials...undetected.
How can App Control help?
An endpoint in default deny mode (or what we like to call High Enforcement) will be protected from a binary-based Mimikatz attack because the process used to launch the attack will not be approved and therefore blocked.
App Control can protect endpoints in other enforcement levels against binary and memory based attacks with the use of the Mimikatz Protection Rapid Config.
Use Cases
<Add info>
Rapid Config Settings
The Mimikatz Protection Rapid Config has three sections that look for different indicators of compromise.
Report, Block, or Do Nothing
As with most Rapid Configs, you can choose to Do Nothing, Report, or Block the items or behaviors. In this case, you can Report or Block on the detection of a combination of DLLs loading. This particular combination (cryptdll.dll, hid.dll, samlib.dll, vaultcli.dll, and winscard.dll) is a good indication of a Mimikatz process as these are not typically loaded at the same time by other processes.
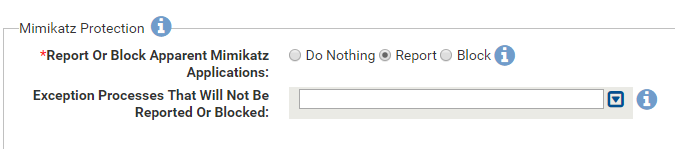
As with all Rapid Configs we recommend setting each section to Report prior to setting to Block. You will want to ensure that the legitimate behavior of these dlls will not be impacted.
Command Lines
The second section of the Rapid Config looks for specific command lines. It will look for:
*sekurlsa* anywhere within the command line. Sekurlsa is a Mimikatz module that extracts passwords, keys, etc from the memory of lsass.
*privilege*debug* in the command line argument. The combination of “privilege” and “debug” within a command line argument is typically used by Mimikatz to get access rights.

*These command line arguments can be changed by a malicious actor, we believe the default arguments will help catch low hanging fruit.
Reading Lsass.exe Memory
The final section of the Rapid Config centers on the reading of Lsass.exe memory.

Most processes should not be reading from lsass memory, however there are executables that legitimately need to do this. Out of the box we’ve included processes like ntoskrnl.exe, msiexec.exe, svchost.exe, and others that should be allowed to read the memory.
It is crucial to initially set this section to Report so that you can find that approved applications in your environment that legitimately need to read the lsass process memory. After letting the Rapid Config run in Report mode for a few weeks, add any approved processes that access lsass memory to the exception list.