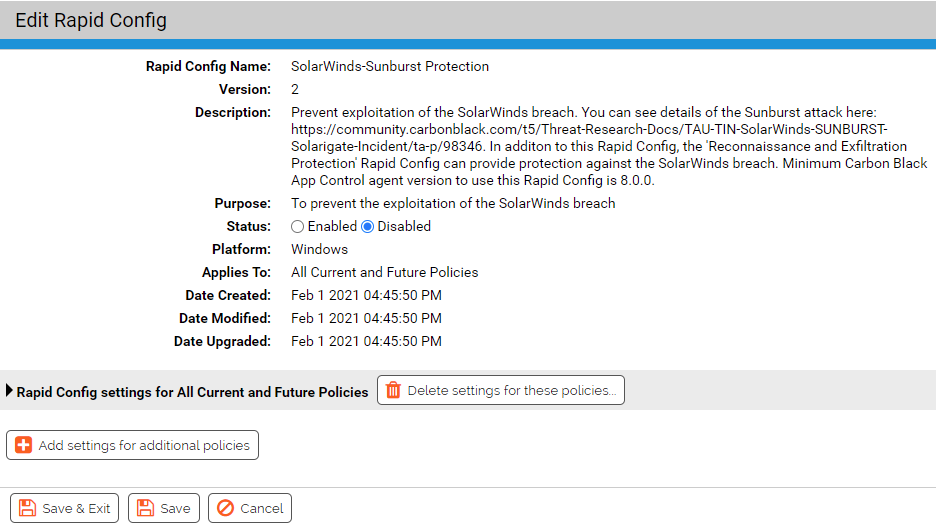
Purpose:To prevent the exploitation of the SolarWinds breach.
Description:Prevent exploitation of the SolarWinds breach. You can see details of the Sunburst attack here: https://community.carbonblack.com/t5/Threat-Research-Docs/TAU-TIN-SolarWinds-SUNBURST-Solarigate-Incident/ta-p/98346.
In December 2020, FireEye disclosed a supply chain attack leveraging SolarWinds Orion software updates to distribute malware, impacting at least 18,000 customers worldwide. The trojanized backdoor, known as Sunburst, is packaged in SolarWinds.Orion.Core.BusinessLayer.dll, a SolarWinds digitally-signed component of the Orion software framework. The trojanized update file is a Windows Installer Patch that includes the trojanized DLL. Once the update is installed, the malicious DLL will be loaded either by the legitimate SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe. Sunburst uses multiple droppers, one of which is the in-memory dropper TEARDROP, which is used in part as a Cobalt Strike beacon.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
Use Cases
<Add info>
How can Carbon Black App Control help?
The SolarWinds-Sunburst Protection Rapid Config can be enabled to block or report execution of the compromised SolarWinds publisher certificate. The Rapid Config can also be configured to report or block suspicious child processes that are spawned by the SolarWinds processes. Lastly, it can prevent the writing of the SolarWinds dropper (TEARDROP) or subsequent invocation as a service.
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Execution of Solarwinds signed files
This group allows you to protect against execution of files signed by Solarwinds Worldwide, LLC. The legitimate Solarwinds publisher (SolarWinds WorldWide, LLC) has signed backdoored installer and malicious executable files.
If you do not leverage SolarWinds in your environment, you can safely enable this rule to block.
Given the sheer number of executables signed by this reported publisher, we recommend customers that leverage SolarWinds enable this rule with Report Only to provide a baseline before assessing if blocking all executions are feasible.
: Known bad hashes associated with SolarWinds are already marked as Malicious via reputation at this time

- Report Or Block Execution Of Anything Published By Solarwinds Worldwide, LLC:
- Should execution of anything published by Solarwinds Worldwide, LLC be reported or blocked. You should validate that legitimate execution is not blocked before enabling blocking.
- Files That Should Not Be Reported:
- Execution of the files specified here will not be reported or blocked.
Executions by suspect processes
This group allows you to protect against malicious application execution. All applications executed by the suspect processes will be blocked unless they are on the exception list.
This rule looks for the primary SolarWinds processes spawning suspicious child processes that could indicate malicious activity. This rule negates typical, benign child processes executing from the typical SolarWinds directories. Note: These primary SolarWinds processes have been observed spawning command interpreters such as PowerShell.exe and cmd.exe and network discovery executables such as arp.exe.
Given the frequent exploit of command interpreters in various attacks, if these child processes are observed in the environment, we recommend triaging command lines and negating benign command lines if feasible, or setting this rule to Report Only for visibility.
: You may have configured alternate directories for the location of SolarWinds executables than the ones listed out of the box.

- Report Or Block Executions By Suspect Processes:
- Should execution by suspect processes be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- *Suspect Processes:
- Carbon Black App Control will report or block execution of files by these processes unless the files are on the exception list. The following are listed by default:
- Files And Command Lines That Should Not Be Reported:
- Execution of the files and command lines specified here will not be reported or blocked. You can add or remove items from this list. The following are listed by default:
Suspicious DLLs
This group allows you to protect against creation and use of suspicious netsetupsvc.dll.
Adversaries disguised their malicious (and unsigned) memory-only dropper with the same name as the legitimate NetSetupSvc.dll, which originates out of System32. The malicious dropper will write to SysWOW64, run as a service, and deploy the Cobalt Strike beacon.
There are two rules associated with this dropper: When set to block, the first rule blocks the write in the reported SysWOW64 directory; the second rule blocks the invocation of this dll as a service.
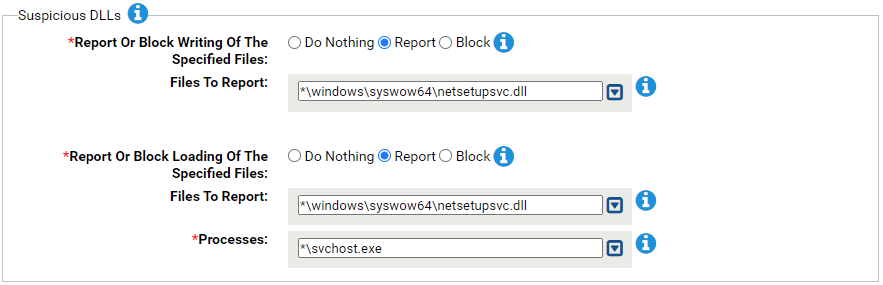
- *Report Or Block Writing Of The Specified Files:
- Should writing of the specified files be reported or blocked? You should validate that legitimate writing will not be blocked before enabling blocking.
- Files To Report:
- Carbon Black App Control will report or block writing of the specified files. You can add or remove items from this list. The following is listed by default:
- *Report Or Block Loading Of The Specified Files:
- Should loading of the specified files by the specified processes be reported or blocked? You should validate that legitimate loading will not be blocked before enabling blocking.
- Files To Report:
- Carbon Black App Control will report or block writing of the specified files. You can add or remove items from this list. The following is listed by default:
- *Processes:
- Carbon Black App Control will report or block execution of the specified files by these processes. You can add or remove items from this list. The following is listed by default: