Purpose: To defend against malicious actors who exploit browser vulnerabilities to attack your enterprise.
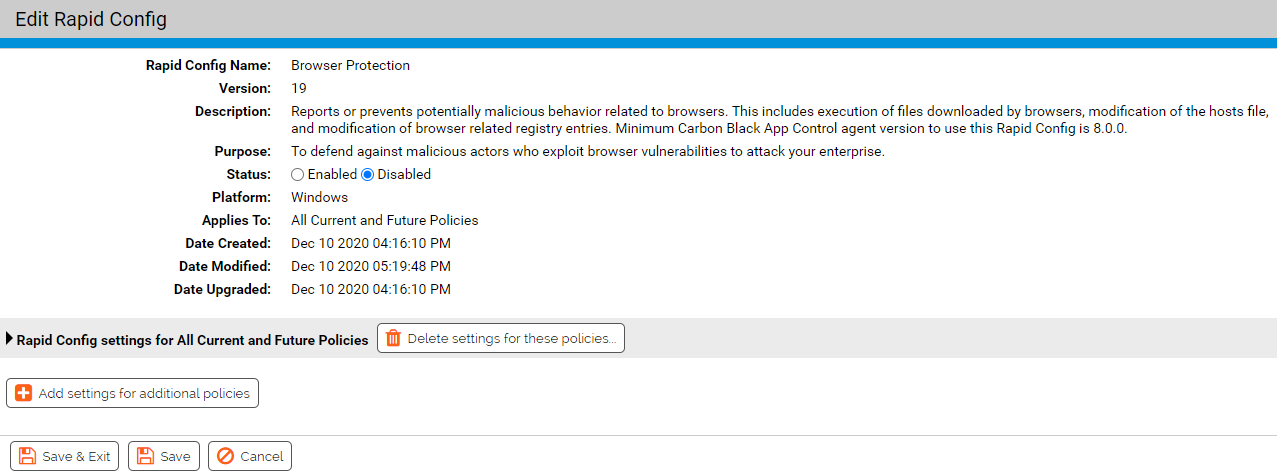
Description: Reports or prevents potentially malicious behavior related to browsers. This includes execution of files downloaded by browsers, modification of the hosts file, and modification of browser related registry entries.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
Use Cases:
<Add info>
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Executables
Use this group to specify applications that should not be run by browsers.
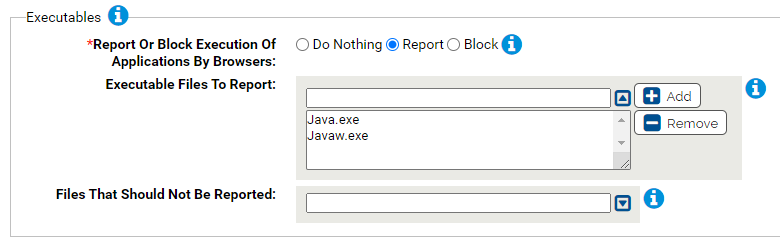
- *Report Or Block Execution Of Applications By Browsers:
- Should execution of the specified applications by browsers be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Executable Files To Report:
-
Carbon Black App Control will report or block execution of the specified files by a browser. You can add or remove items from this list. By default, the list includes:
- Java.exeJavaw.exe
- Files That Should Not Be Reported:
- Execution of files specified here will not be reported or blocked. You can add or remove items from this list. To edit, click the down arrow next to the text box.
Downloaded Executables
Use this group to specify how to handle applications downloaded by browsers.
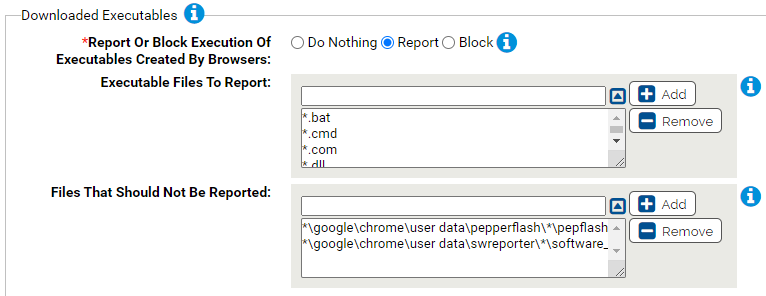
- *Report Or Block Execution Of Executables Created By Browsers:
- Should execution of the specified executables that were created by browsers be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Executable Files To Report:
-
Carbon Black App Control will report or block execution of the specified files if they were created by a browser. You can add or remove items from this list. Bydefault, the list includes:
- *.bat
- *.cmd
- *.com
- *.dll
- *.exe
- *.msi
- *.scr
- Files That Should Not Be Reported:
-
Execution of files specified here will not be reported or blocked. You can add or remove items from this list. To edit, click the down arrow next to the text box and select the item to edit. By default, the list includes:
- *\google\chrome\user data\pepperflash\*\pepflashplayer.dll
- *\google\chrome\user data\swreporter\*\software_reporter_tool.exe
Registry Protection
Use this group to specify registry settings to protect.
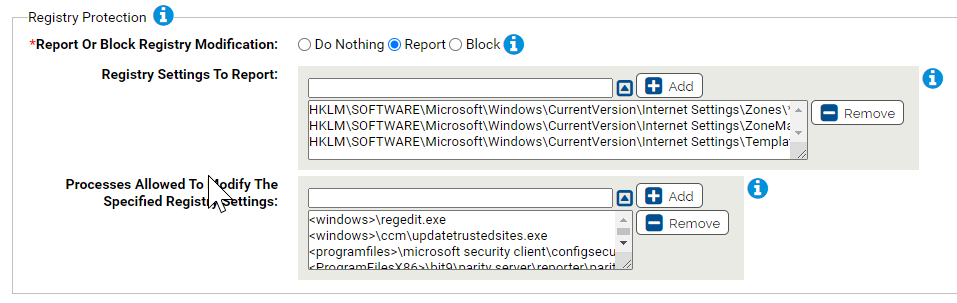
- *Report Or Block Registry Modification:
- Should modification of the specified registry settings be reported or blocked? You should validate that legitimate registry modifications are not blocked before enabling blocking.
- Registry Settings To Report:
-
Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. By default, the list includes:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\*
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\*
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\TemplatePolicies\*
- Processes Allowed To Modify The Specified Registry Settings:
-
Processes specified here will be allowed to modify the specified registry settings. You can add or remove items from this list. By default, the list includes:
- <windows>\regedit.exe
- <windows>\ccm\updatetrustedsites.exe
- <programfiles>\microsoft security client\configsecuritypolicy.exe
- <ProgramFilesX86>\bit9\parity server\reporter\parityreporter.exe
Host File Protection
Use this group to protect the hosts file.
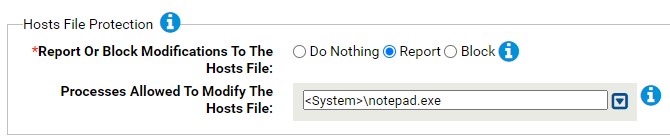
- *Report Or Block Modifications To The Hosts File:
- Should modification of the hosts file be reported or blocked? You can specify process that are allowed to modify the hosts file in the next parameter.
- Processes Allowed To Modify The Hosts File:
-
Processes specified here will be allowed to modify the hosts file. You can add or remove items from this list. By default, the list includes:
- <System>\notepad.exe