Purpose: To defend against cryptomining in your enterprise.
Description: Reports or prevents potentially malicious behavior related to file based cryptomining attacks.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
What is Cryptomining?
In order for people to obtain cryptocurrency without purchasing it, the currency needs to be mined. Mining uses the processing power of a computer to solve mathematical problems with hashing functions to mine “coins.”
Obviously, having computers running cryptominers becomes a problem when people within and outside of your organization are using your systems without your knowledge. Mining can impact your business processes and electricity bills.
How can App Control Help?
Customers with their endpoints running App Control in High Enforcement will likely be protected from the majority of cryptoming processes. But for added protection or for those endpoints that have not yet moved to High Enforcement (or are not planned for High Enforcement), the Cryptoming Rapid Config can help.
Use Cases
<Add info>
Rapid Config Settings
The Cryptomining Rapid Config focuses on blocking or reporting on executables and command lines matching specific parameters.
Report, Block, or Do Nothing
As with most Rapid Configs, you can choose to Do Nothing, Report, or Block the items or behaviors.
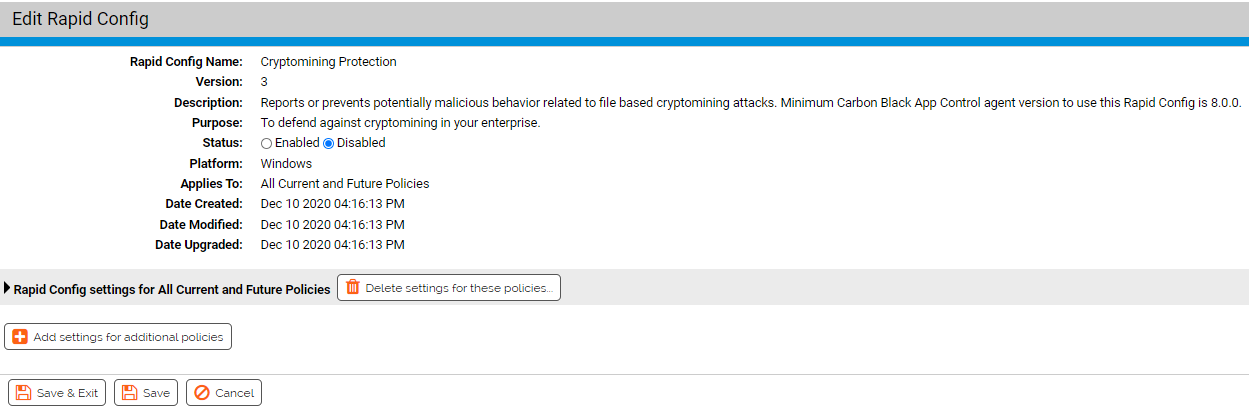
This Rapid Config consists of a single section which defaults to reporting on Cryptomining file executions.
In the process of researching Cryptominers our Threat Research team determined that the majority of these executables had the following filenames or paths:
|
|
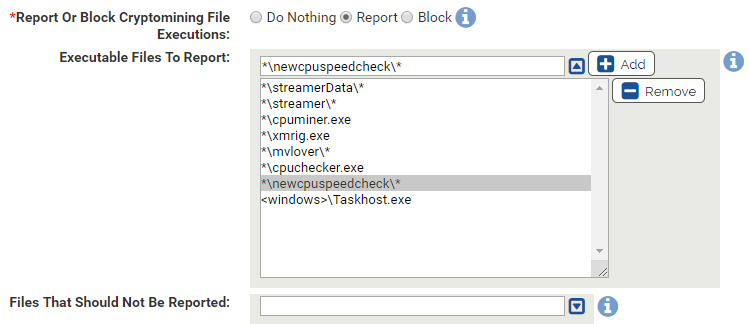
If you are getting blocks or reports on legitimate files because of this list of executables, you can add exceptions. For example, if you have an internally developed application that resides at C:\Program Files\MyBiz\streamer\ and it is getting blocked, you could add the application name to the exception list like *\streamer\myapp.exe.
Command Lines
There are several common parameters that are used by cryptoming tools when they are launched. These commands are:
|
|
Using the cmdline macro, the App Control Windows agent can look for any of these parameters when an executable is launched. If it sees any process launching with any of these parameters, the process will be terminated.
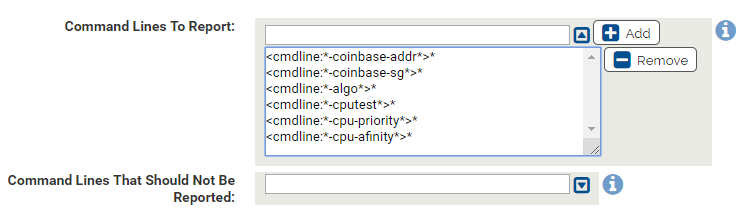
Just like with the executables you can add exceptions to this list. For example, if you have an executable called myapp.exe that uses a -cpu-affinity parameter, you can exclude your application from being blocked or reported on by adding this <cmdline:*-cpu-affinity*>myapp.exe in the Command Lines That Should Not Be Reported area.