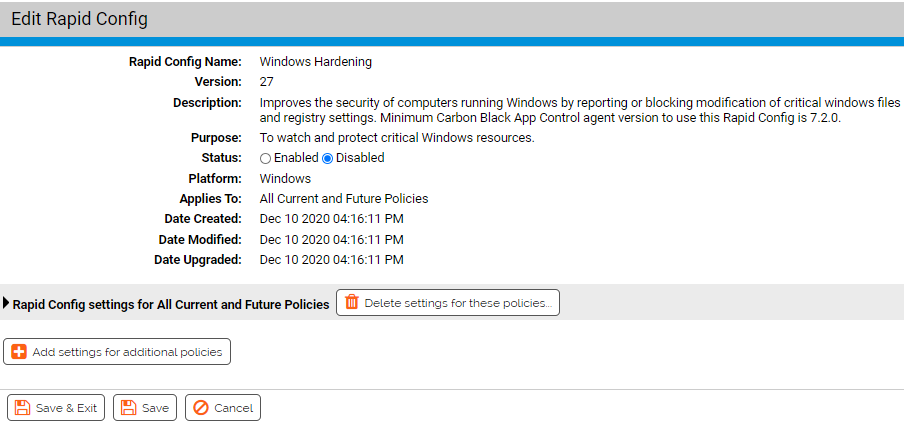
Purpose: To watch and protect critical Windows resources.
Description: Improves the security of computers running Windows by reporting or blocking modification of critical windows files and registry settings.
| CDC Push Date: | |
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 7.2.0 |
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Windows Configuration Files
Use this group to protect Windows configuration files.
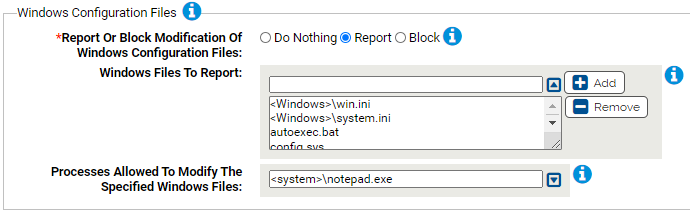
- *Report Or Block Modification Of Windows Configuration Files:
- Should modification of the specified files be reported or blocked? You should validate that legitimate modification is not blocked before enabling blocking.
- Windows Files To Report:
-
Carbon Black App Control will report or block modifications of the specified files. You can add or remove items from this list. By default, the list includes:
- <Windows>\win.ini
- <Windows>\system.ini
- autoexec.bat
- config.sysboot.ini
- Processes Allowed To Modify The Specified Windows Files:
-
Processes specified here will be allowed to modify the specified Windows files. You can add or remove items from this list. By default, the list includes:
- <system>\notepad.exe
Windows System Files
Use this group to protect Windows system files.
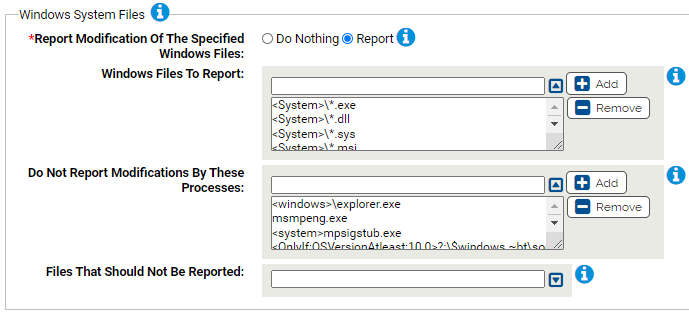
- *Report Modification Of The Specified Windows Files:
- Should modification of the specified Windows files be reported?
- Windows Files To Report:
-
Carbon Black App Control will report modifications of the specified Windows files. You can add or remove items from this list. By default, the list includes:
- <System>\*.exe
- <System>\*.dll
- <System>\*.sys
- <System>\*.msi<System>\*.drv
- <System>\*.ocx<System>\*.scr
- <SystemX86>\*.exe
- <SystemX86>\*.dll
- <SystemX86>\*.sys
- <SystemX86>\*.msi
- <SystemX86>\*.drv
- <SystemX86>\*.ocx
- <SystemX86>\*.scr
- Do Not Report Modifications By These Processes:
-
Processes listed here will be allowed to modify the specified Windows files. You can add or remove items from this list. By default, the list includes:
- <windows>\explorer.exe
- msmpeng.exe
- <system>mpsigstub.exe
- <OnlyIf:OSVersionAtleast:10.0>?:\$windows.~bt\sources\setuphost.exe
- Files That Should Not Be Reported:
- Modifications to files specified here will not be reported. You can add or remove items from this list.
Windows Registry Settings
Use this group to protect Windows registry settings.
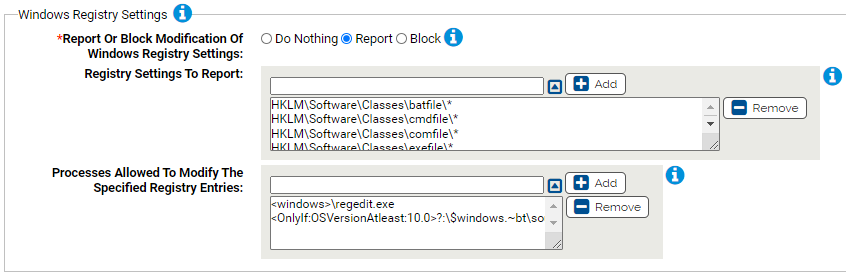
- *Report Or Block Modification Of Windows Registry Settings:
- Should modification of the specified registry settings be reported or blocked? You should validate that legitimate registry modifications are not blocked before enabling blocking.
- Registry Settings To Report:
-
Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. By default, the list includes:
- HKLM\Software\Classes\batfile\*
- HKLM\Software\Classes\cmdfile\*
- HKLM\Software\Classes\comfile\*
- HKLM\Software\Classes\exefile\*
- HKLM\Software\Classes\piffile\*
- HKLM\Software\Classes\AllFilesystemObjects\*
- HKLM\Software\Classes\Directory\*
- HKLM\Software\Classes\Folder\*
- HKLM\Software\Classes\Protocols
- HKLM\System\CurrentControlSet\Control\Session Manager\KnownDLLs\*
- HKLM\System\CurrentControlSet\Control\SecurePipeServers\winreg\*
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run\*
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce\*
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnceEx\*
- HKLM\Software\Microsoft\Windows\CurrentVersion\URL\*
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\*
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\*
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\*
- HKLM\Software\Microsoft\Active Setup\Installed Components\*
- Processes Allowed To Modify The Specified Registry Entries:
-
Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list. By default, the list includes:
- <windows>\regedit.exe
- <OnlyIf:OSVersionAtleast:10.0>?:\$windows.~bt\sources\setuphost.exe
Trust Verification Registry Settings for Executables
Use this group to protect registry settings that affect verifying security certificates for executable files - exes, dlls, etc. We expect minimal false positives for these keys. Allowing modification of these keys enables a malicious user to make a file appear to have a valid digital signature even though it does not. Windows updates will be allowed to make modifications to the registry settings, other processes will be blocked or reported.
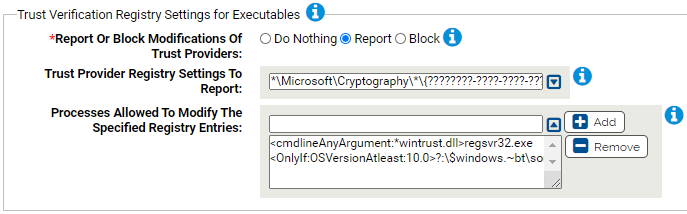
- *Report Or Block Modifications Of Trust Providers:
- Should modification of the specified registry settings be reported or blocked? You should validate that legitimate registry modifications are not blocked before enabling blocking.
- Trust Provider Registry Settings To Report:
-
Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. By default, the list includes:
- *\Microsoft\Cryptography\*\{????????-????-????-????-00C04FC295EE}\*
- Processes Allowed To Modify The Specified Registry Entries:
-
Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list. By default, the list includes:
- <cmdlineAnyArgument:*wintrust.dll>regsvr32.exe<OnlyIf:OSVersionAtleast:10.0>?:\$windows.~bt\sources\setuphost.exe
Trust Verification Registry Settings for Non-Executables
Use this group to protect registry settings that affect verifying security certificates for non executables such as scripts, .net assemblies, etc. Allowing modification of these keys enables a malicious user to make a file appear to have a valid digital signature even though it does not. Windows updates will be allowed to make modifications to the registry settings, other processes will be blocked or reported.
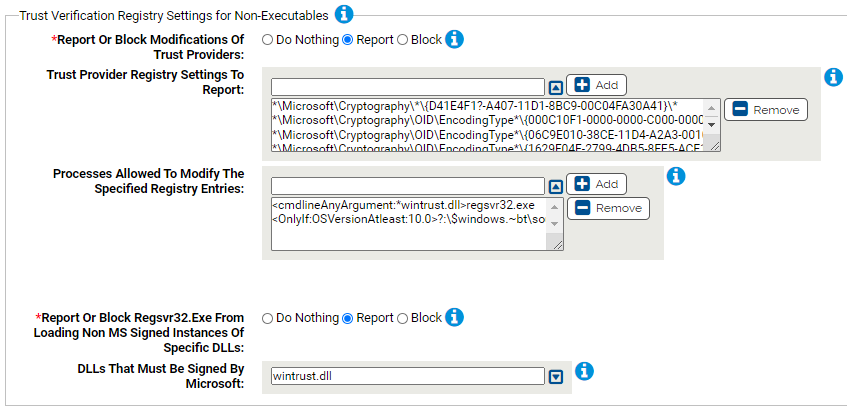
- *Report Or Block Modifications Of Trust Providers:
- Should modification of the specified registry settings be reported or blocked? You should validate that legitimate registry modifications are not blocked before enabling blocking.
- Trust Provider Registry Settings To Report:
-
Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. By default, the list includes:
- *\Microsoft\Cryptography\*\{D41E4F1?-A407-11D1-8BC9-00C04FA30A41}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{000C10F1-0000-0000-C000-000000000046}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{06C9E010-38CE-11D4-A2A3-00104BD35090}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{1629F04E-2799-4DB5-8FE5-ACE10F17EBAB}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{1A610570-38CE-11D4-A2A3-00104BD35090}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{0AC5DF4B-CE07-4DE2-B76E-23C839A09FD1}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{0F5F58B3-AADE-4B9A-A434-95742D92ECEB}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{5598CFF1-68DB-4340-B57F-1CACF88C9A51}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{9F3053C5-439D-4BF7-8A77-04F0450A1D9F}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{CF78C6DE-64A2-4799-B506-89ADFF5D16D6}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{D1D04F0C-9ABA-430D-B0E4-D7E96ACCE66C}\*
- *\Microsoft\Cryptography\OID\EncodingType*\{603BCC1F-4B59-4E08-B724-D2C6297EF351}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{6078065b-8f22-4b13-bd9b-5b762776f386}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{64B9D180-8DA2-11CF-8736-00AA00A485EB}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{7801EBD0-CF4B-11D0-851F-0060979387EA}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{C6B2E8D0-E005-11CF-A134-00C04FD7BF43}\*
- *\Microsoft\Cryptography\Providers\Trust\*\{FC451C16-AC75-11D1-B4B8-00C04FB66EA0}\*
- Processes Allowed To Modify The Specified Registry Entries:
-
Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list. By default, the list includes:
- <cmdlineAnyArgument:*wintrust.dll>regsvr32.exe
- <OnlyIf:OSVersionAtleast:10.0>?:\$windows.~bt\sources\setuphost.exe
- *Report Or Block Regsvr32.Exe From Loading Non MS Signed Instances Of Specific DLLs:
- Should regsvr32.exe loading the specified DLLs be reported or blocked when the DLLs are NOT signed by Microsoft? You should validate that legitimate DLL loading is not blocked before enabling blocking.
- DLLs That Must Be Signed By Microsoft:
-
DLLs listed here that are not signed by Microsoft will be reported or blocked from being loaded by regsvr32.exe. You can add or remove items from this list. By default, the list includes:
- wintrust.dll