Purpose:To prevent Ransomware from encrypting your important files.
Description: Protect against ransomware by reporting or blocking modification to files typically targeted by ransomware. The Rapid Config does this in a number of ways. It prevents in place encryption by looking for changes in the type of a file. It prevents deletion and renaming of files except by specified processes. It blocks creation of known ransomware files and registry settings. And it prevents the use of VSSAdmin to delete shadow copy backups.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 Patch 5 |
Use Cases:
Out of the box, this Rapid Config is designed to protect all instances of valuable files, such as: *.doc, *.xls, *.gif. Some customers may find that this results in too many false positives that require specific exceptions. For example, application installations and updates often create/remove image and document files that often trigger the protections in the Rapid Config.
Rather than using the out of the box settings and creating a long list of exceptions, you can limit the locations where files are protected. For instance, you could replace the default *.doc setting with *\users\documents\*.doc so only doc files under the users’ documents folder are protected. This would eliminate the need for most exception cases; however, it limits the protections.
If you take this approach, identify the locations where users create and store their valuable documents and protect those locations.
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Prevent in-place encryption (File type changes)
This group allows you to protect files from Ransomware by blocking in place encryption of files. Carbon Black App Control does this by looking for a change in the type of the file.
The protected file types are: doc, docm, docx, xls, xlsm, xlsx, ppt, pptm, pptx, rtf, pdf, png, jpg, jpeg, bmp, giff, and tiff.
In addition to blocking the file type change we will terminate the application attempting the change.

- *Report Or Block File Type Changes:
- This group allows you to protect files from Ransomware by blocking in place encryption of files. Carbon Black App Control does this by looking for a change in the type of the file.
- Processes Allowed To Change The Type Of Files:
- Processes specified here will be allowed to change the type of the specified files. You can add or remove items from this list.
- Files That Should Not Be Reported:
- Type changes of files specified here will not be reported. You can add or remove items from this list.
Prevent renaming and deleting of document files
This group allows you to protect document files from Ransomware by limiting the processes that are allowed to delete or rename those files.

- *Report Or Block Renaming Or Deletion Of Documents:
- Should renaming or deletion of the specified document types be reported or blocked? You should validate that legitimate behavior would not be blocked before enabling blocking.
- Document Files To Report:
- Carbon Black App Control will report or block renaming or deletion of the specified documents. You can add or remove items from this list. By default, the list is as follows:
- Processes Allowed To Rename Or Delete The Specified Document Files:
- Processes specified here will be allowed to rename or delete the specified documents. You can add or remove items from this list. By default, the following are listed:
- Document Files That Should Not Be Reported:
-
Renaming or deletion of files specified here will not be reported. You can add or remove items from this list. The following is listed by default: <localappdata>\temp\*
- Allow Interactive Instances Of Cmd.Exe And Powershell To Rename Or Delete The Specified Document Files:
- When checked, renaming or deletion of the specified document files by interactive instances of cmd.exe and powershell.exe will not be reported. An interactive instance of cmd.exe and powershell.exe are those that were started with no parameters.
- *Trigger When The Document Is The Target Of The Rename Operation?:
- Should the Rapid Config prevent renames when the document is the TARGET of the rename?
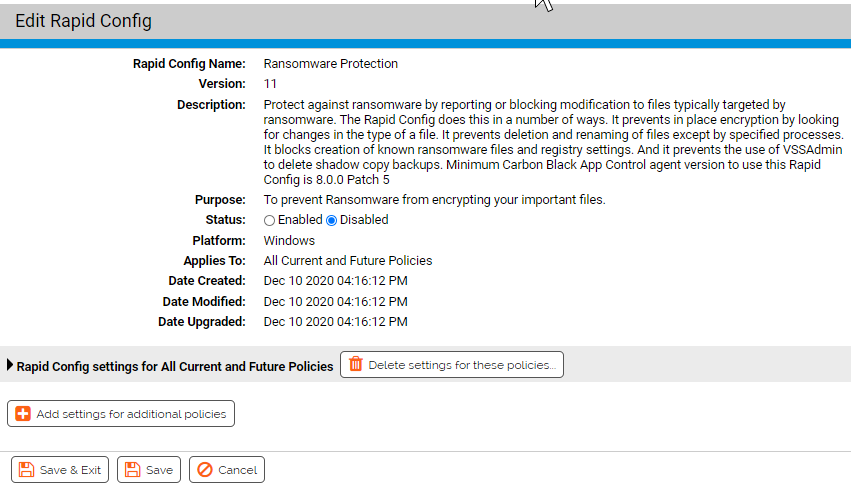
Prevent renaming and deleting of image files
This group allows you to protect Image files from ransomware by limiting the process that are allowed to delete or rename the files.
- *Report Or Block Renaming Or Deletion Of Image Files:
- Should renaming or deletion of the specified image file types be reported or blocked? You should validate that legitimate behavior would not be blocked before enabling blocking.
- Image Files To Report:
- Carbon Black App Control will report or block renaming or deletion of the specified image files. You can add or remove items from this list. The following are listed by default:
- Processes Allowed To Rename Or Delete The Specified Image Files:
- Processes specified here will be allowed to rename or delete the specified Image files. You can add or remove items from this list. The following are listed by default:
- Image Files That Should Not Be Reported:
- Renaming or deletion of files specified here will not be reported. You can add or remove items from this list. The following are listed by default:
- Allow Interactive Instances Of Cmd.Exe And Powershell To Rename Or Delete The Specified Image Files:
- When checked, renaming or deletion of the specified image files by interactive instances of cmd.exe and powershell.exe will not be reported. An interactive instance of cmd.exe and powershell.exe are those that were started with no parameters.
- *Trigger When The Image File Is The Target Of The Rename Operation?:
- Should the Rapid Config prevent renames when the image file is the TARGET of the rename?
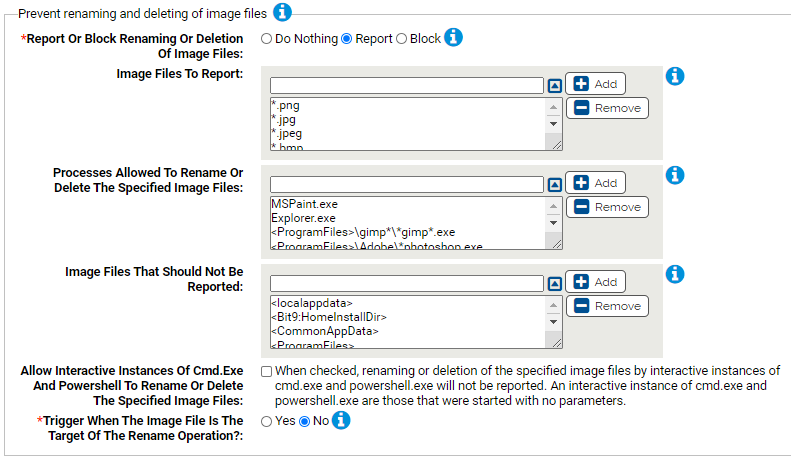
Prevent renaming and deleting of other files
This group allows you to specify any additional files you would like to protect. You can specify the files and the processes that should be allowed to delete or rename them.
- Report Or Block Renaming Or Deletion Of Files:
- Should renaming or deletion of the specified files be reported or blocked? You should validate that legitimate behavior would not be blocked before enabling blocking.
- Files To Report:
- Carbon Black App Control will report or block renaming or deletion of the specified files. You can add or remove items from this list.
- Processes Allowed To Rename Or Delete The Specified Files:
- Processes specified here will be allowed to rename or delete the specified files. You can add or remove items from this list.
- Files That Should Not Be Reported:
- Renaming or deletion of files specified here will not be reported. You can add or remove items from this list.
- Allow Interactive Instances Of Cmd.Exe And Powershell To Rename Or Delete The Specified Files:
- When checked, renaming or deletion of the specified files by interactive instances of cmd.exe and powershell.exe will not be reported. An interactive instance of cmd.exe and powershell.exe are those that were started with no parameters.
- *Trigger When The File Is The Target Of The Rename Operation?:
- Should the Rapid Config prevent renames when the file is the TARGET of the rename?
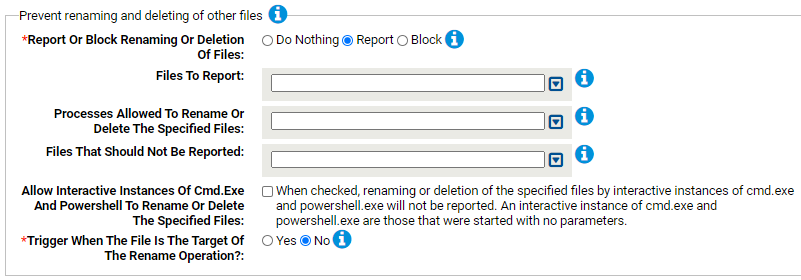
Prevent the creation of ransomware artifacts
This group allows you to watch for and optionally block file and registry changes that indicate ransomware activity. For example you can block files with extensions known to be used by ransomware.
- *Report Or Block Ransomware Files:
- Should modification of the specified files be reported or blocked? You should validate that legitimate modification is not blocked before enabling blocking.
- Ransomware Files To Report:
- Carbon Black App Control will report or block modifications of the specified files. Typically listed here are files or extensions known to be used by ransomware. You can add or remove items from this list. By default, the following are listed:
- Processes Allowed To Modify The Specified Files:
- Processes specified here will be allowed to modify the specified files. You can add or remove items from this list.
- *Report Or Block Ransomware Related Registry Settings:
- Should modification of the specified registry settings be reported or blocked? You should validate that legitimate modification is not blocked before enabling blocking.
- Ransomware Registry Settings To Report:
- Carbon Black App Control will report or block modification of the specified registry settings. You can add or remove items from this list. By default, the following are listed:
- Processes Allowed To Modify The Specified Registry Settings:
- Processes specified here will be allowed to modify the specified registry settings. You can add or remove items from this list.
Prevent the use of VSSAdmin to delete shadow copies
This group allows you to report or block VSSAdmin execution when using the specified command line options. Ransomware will often delete shadow copies using VSSAdmin in order to hinder restoring systems from backup.
- *Report Or Block VSSAdmin With The Specified Parameters:
- Should execution of VSSAdmin using the delete command be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- VSSAdmin Command Line To Report:
- Carbon Black App Control will report or block execution of VSSAdmin.exe with the specified command line.