Purpose: To protect against doppelganger attacks on windows systems.
Description: Protect against the exploit known as Doppelganging on windows systems.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 Patch 7 |

What is Doppelganger Protection?
The Process Doppelganging technique uses ntoskrnl to create a transaction subsequently opening a legitimate file into that transaction (for attack purposes the legitimate file would most likely be a signed Microsoft binary).
A malicious payload (in the form of an executable) is then written to that transaction record using the standard API calls (in their POC the malicious payload was encrypted on disk, opened and decrypted by their loader and then written to the transaction record). Their technique then creates a section (via NTCreateSession) for the malicious code (preserving the malicious code), and rolls back the changes to the original legitimate file (the previously created section will not be altered and still contains the malicious code). Their technique then creates a process (and a thread) with a handle to this section, which will appear to be the legitimate process (backed up by legitimate code on disk).
Ultimately this technique is a process that uses the legit Window Loader to run malicious code. As for right now, until we can determine how to best detect this technique, we are suggesting that practitioners focus on the final payload being run. The Cb suite of products will be able to detect the final payload and their associated actions the same as if an attacker used rundll32 or PowerShell to execute the malicious code. Obviously, we want to try and focus on detecting suspicious actions as soon as possible (and we will work to ensure we can detect this technique), but this exploit was developed to evade traditional AV that hooks and scans files (with signatures) at different points prior to the code actually being loaded or executed.
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors. For each of the following sections, specify what action you require.
Doppelganger Behavior
You can use these properties to specify how to treat files that appear to be part of a doppelganger exploit.
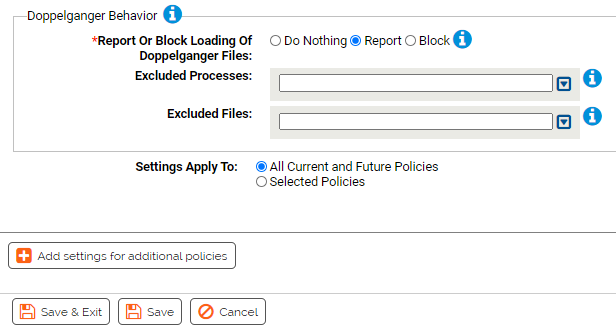
- Report Or Block Loading Of Doppelganger Files:
- Should doppelganger behavior be reported or blocked? You should validate that legitimate behavior is not blocked before enabling blocking.
- Excluded Processes:
- Processes specified here will be allowed to load suspected doppelganger files. You can add or remove items from this list.
- Excluded Files:
- Files specified here will not be reported or blocked. You can add or remove items from this list.