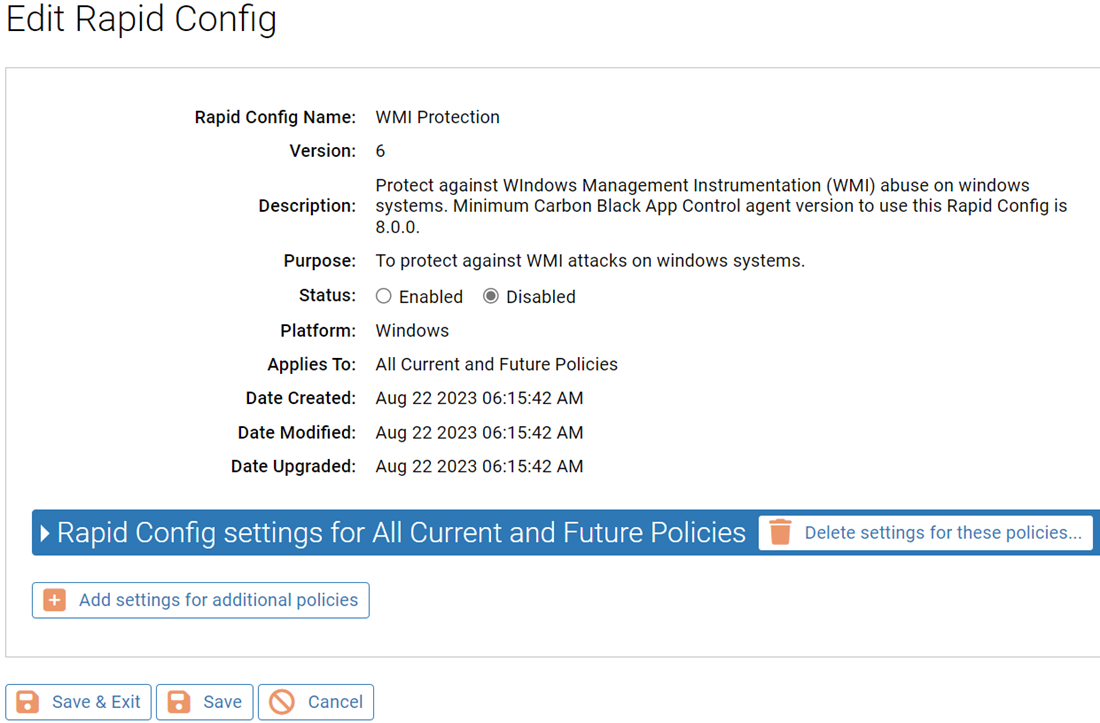
Purpose: To protect against WMI attacks on windows systems.
Description: Protect against WIndows Management Instrumentation (WMI) abuse on windows systems.
| CDC Push Date: | |
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
WMI/WinRM Execution
Use this group to protect against attacks using Windows Management Instrumentation (WMI)
Windows Management Instrumentation is a Windows administration feature that provides a uniform environment for local and remote access to Windows system components. It relies on the WMI service for local and remote access and the server message block (SMB) and Remote Procedure Call Service (RPCS) for remote access.
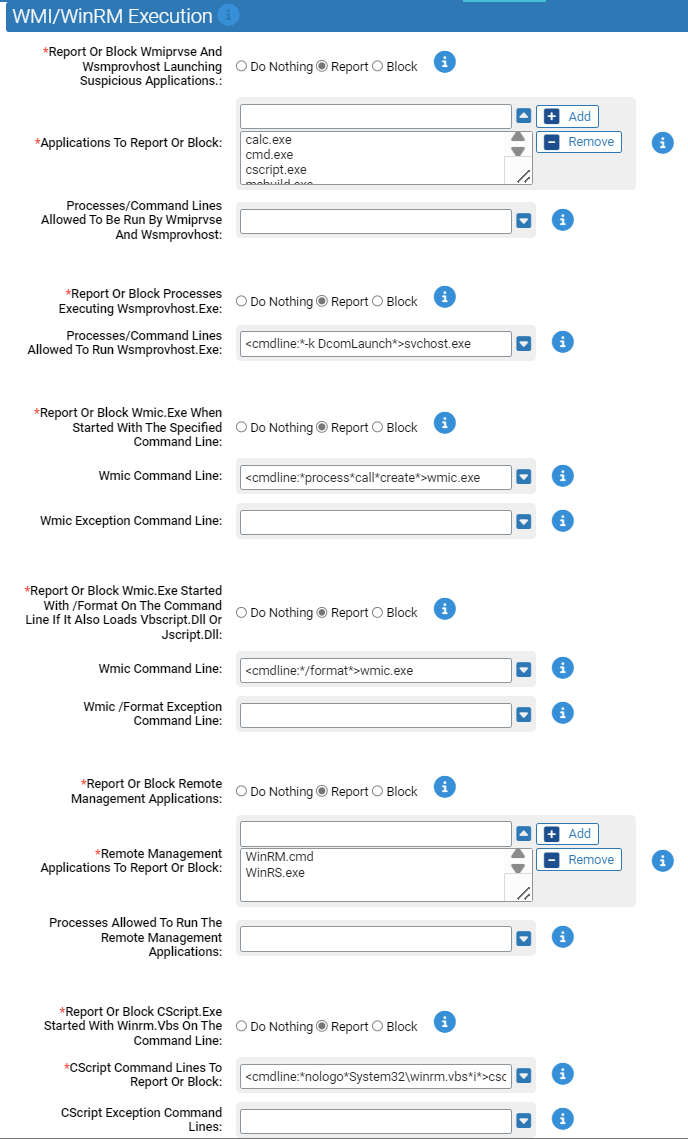
- *Report Or Block Wmiprvse And Wsmprovhost Launching Suspicious Applications:
- Should execution of the specified applications by wmiprvse or wsmprovhost be reported or blocked? You should validate that legitimate behavior is not blocked before enabling blocking.
- *Applications To Report Or Block:
-
Carbon Black App Control will report or block execution of the specified applications by wmiprvse.exe or wsmprovhost.exe. You can add or remove files from this list. By default, the list includes:
- calc.exe
- cmd.exe
- cscript.exe
- msbuild.exe
- mshta.exe
- notepad.exe
- powershell.exe
- vssadmin.exe
- wscript.exe
- Processes/Command Lines Allowed To Be Run By Wmiprvse And Wsmprovhost:
- Processes and command lines listed here will not be blocked.
- *Report Or Block Processes Executing Wsmprovhost.Exe:
- Should execution of wsmprovhost.exe be reported or blocked. Wsmprovhost is the process responsible for powershell remoting. You should validate that legitimate behavior is not blocked before enabling blocking.
- Processes/Command Lines Allowed To Run Wsmprovhost.Exe:
-
Processes/command lines listed here will not be reported or blocked when they run wsmprovhost.exe. You can add or remove lines from this list. By default, the list includes:
- <cmdline:*-k DcomLaunch*>svchost.exe
- *Report Or Block Wmic.Exe When Started With The Specified Command Line:
- Should execution of wmic.exe be reported or blocked when started with the potentially supcicious command line. The process call create command is often used for lateral movement/code execution. You should validate that legitimate behavior is not blocked before enabling blocking.
- Wmic Command Line:
-
Carbon Black App Control will report or block execution of wmic.exe using the specified command line. You can add or remove items from this list. By default, the list includes:
- <cmdline:*process*call*create*>wmic.exe
- Wmic Exception Command Line:
- Command lines specified here will not be blocked. You can add or remove items from this list.
- *Report Or Block Wmic.Exe Started With /Format On The Command Line If It Also Loads Vbscript.Dll Or Jscript.Dll:
- Should execution of wmic.exe be reported or blocked when started with /format on the command line and wmic loads either vbscript.dll or jscript.dll.
- Wmic Command Line:
-
Carbon Black App Control will report or block execution of wmic.exe using the specified command line if it also loads vbscript.dll or jscript.dll. You can add or remove items from this list. By default, the list includes:
- <cmdline:*/format*>wmic.exe
- Wmic /Format Exception Command Line:
- Command lines specified here will not be blocked. You can add or remove items from this list.
- *Report Or Block Remote Management Applications:
- Should execution of the specified remote management applications be blocked? You should validate that legitimate behavior is not blocked before enabling blocking.
- *Remote Management Applications To Report Or Block:
-
Carbon Black App Control will report or block execution of the remote management applications. You can add or remove files from this list. By default, the list includes:
- WinRM.cmd
- WinRS.exe
- Processes Allowed To Run The Remote Management Applications:
- The remote management applications will not be blocked when run by processes listed here.
- *Report Or Block CScript.Exe Started With Winrm.Vbs On The Command Line:
- Should execution of Cscript.exe using the specified command lines be blocked? You should validate that legitimate behavior is not blocked before enabling blocking.
- *CScript Command Lines To Report Or Block:
-
Carbon Black App Control will report or block execution of CScript.exe started with the specified command lines. You can add or remove files from this list. By default, the list includes:
- <cmdline:*nologo*System32\winrm.vbs*i*>cscript.exe
- CScript Exception Command Lines:
- CScript Command lines specified here will not be reported or blocked.
WMI/WinRM Hardening
Use this group to provide miscellaneous rules for WMI hardening
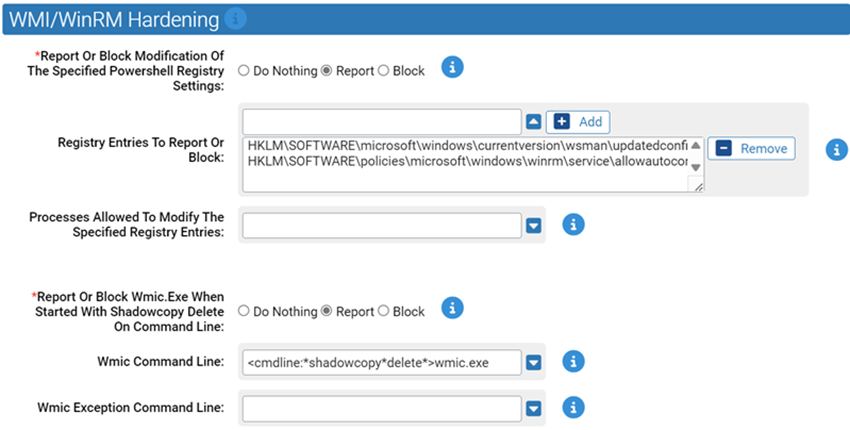
- *Report Or Block Modification Of The Specified Powershell Registry Settings:
- Should modification of the specified powershell registry entries be reported or blocked. You should validate that legitimate behavior is not blocked before enabling blocking.
- Registry Entries To Report Or Block:
-
Carbon Black App Control will report or block modification of the specified registry entries. You can add or remove items from this list. By default, the list includes:
- HKLM\SOFTWARE\microsoft\windows\currentversion\wsman\updatedconfig
- HKLM\SOFTWARE\policies\microsoft\windows\winrm\service\allowautoconfig
- Processes Allowed To Modify The Specified Registry Entries:
- Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list.
- *Report Or Block Wmic.Exe When Started With Shadowcopy Delete On Command Line:
- Should execution of wmic.exe be reported or blocked when started with shadowcopy delete on the command line. You should validate that legitimate behavior is not blocked before enabling blocking.
- Wmic Command Line:
-
Carbon Black App Control will report or block execution of wmic.exe using the specified command line. You can add or remove items from this list. By default, the list includes:
- <cmdline:*shadowcopy*delete*>wmic.exe
- Wmic Exception Command Line:
- Command lines specified here will not be blocked. You can add or remove items from this list.
WMI/WinRM Persistence
Windows Management Instrumentation (WMI) can be used to install event filters, providers, consumers, and bindings that execute code when a defined event occurs. Adversaries may use the capabilities of WMI to subscribe to an event and execute arbitrary code when that event occurs, providing persistence on a system.
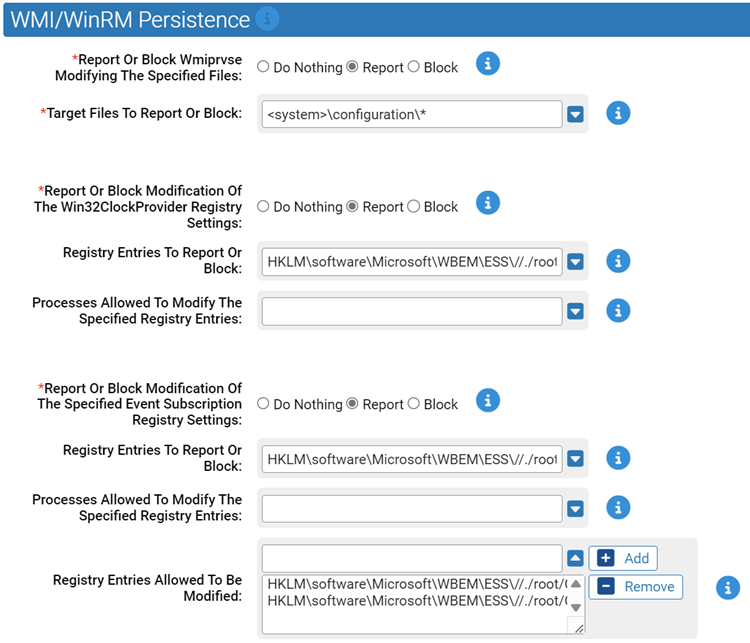
- *Report Or Block Wmiprvse Modifying The Specified Files:
- Should writing of the specified files by wmiprvse.exe be reported or blocked. You should validate that legitimate behavior is not blocked before enabling blocking.
- *Target Files To Report Or Block:
-
Carbon Black App Control will report or block modification of the specified files by WMIPrvse.exe. You can add or remove items from this list. By default, the list includes:
- <system>\configuration\*
- *Report Or Block Modification Of The Win32ClockProvider Registry Settings:
- Should modification of the specified registry entries be reported or blocked. You should validate that legitimate behavior is not blocked before enabling blocking.
- Registry Entries To Report Or Block:
-
Carbon Black App Control will report or block modification of the specified registry entries. You can add or remove items from this list. By default, the list includes:
- HKLM\software\Microsoft\WBEM\ESS\//./root/CIMV2\Win32ClockProvider*
- Processes Allowed To Modify The Specified Registry Entries:
- Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list.
- *Report Or Block Modification Of The Specified Event Subscription Registry Settings:
- Should modification of the specified Event Subscription registry entries be reported or blocked. You should validate that legitimate behavior is not blocked before enabling blocking.
- Registry Entries To Report Or Block:
-
Carbon Black App Control will report or block modification of the specified registry entries. You can add or remove items from this list. By default, the list includes:
- HKLM\software\Microsoft\WBEM\ESS\//./root/CIMV2*
- Processes Allowed To Modify The Specified Registry Entries:
- Processes specified here will be allowed to modify the specified registry entries. You can add or remove items from this list.
- Registry Entries Allowed To Be Modified:
-
Modification of the registry entries specified here will be allowed. You can add or remove items from this list. By default, the list includes:
- HKLM\software\Microsoft\WBEM\ESS\//./root/CIMV2\Win32ClockProvider*
- HKLM\software\Microsoft\WBEM\ESS\//./root/CIMV2\SCM Event Provider*