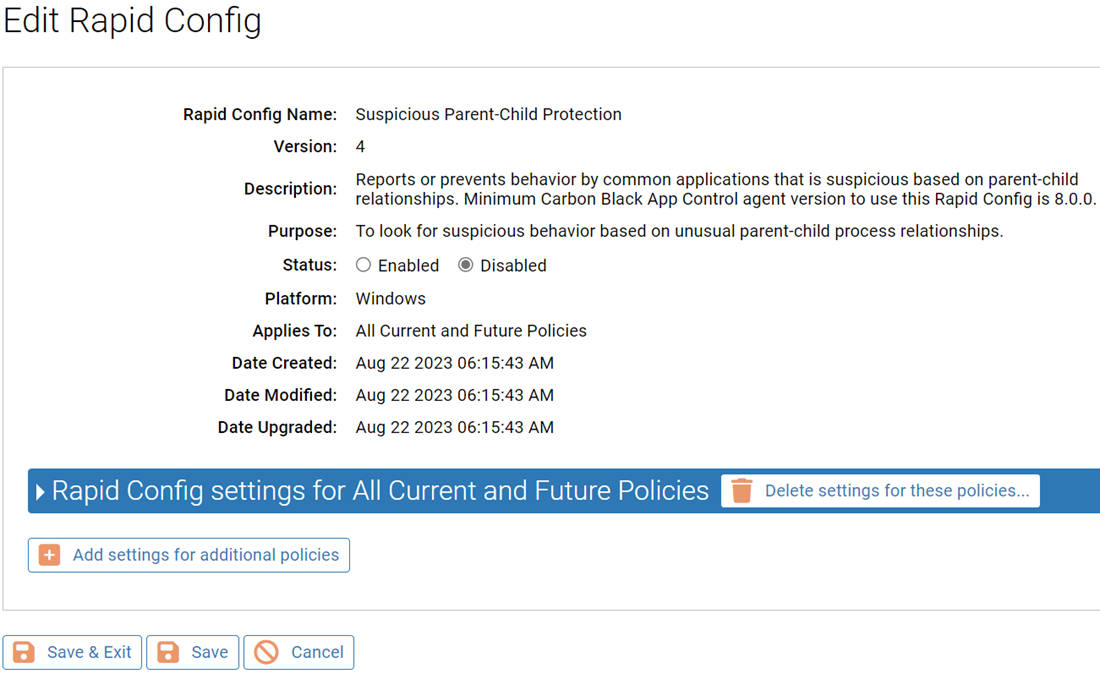
Purpose: To look for suspicious behavior based on unusual parent-child process relationships.
Description: Reports or prevents behavior by common applications that is suspicious based on parent-child relationships.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 8.0.0 |
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors.
For each of the following sections, specify what action you require.
Appvlp.exe
Use this group to specify how to handle suspicious behavior by Appvlp.exe.
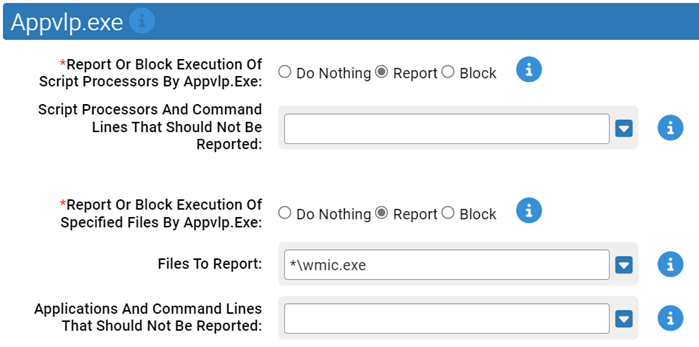
- *Report Or Block Execution Of Script Processors By Appvlp.Exe:
- Should execution of script processors by Appvlp.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Script Processors And Command Lines That Should Not Be Reported:
- Execution of these files by Appvlp.exe will not be reported or blocked.
- *Report Or Block Execution Of Specified Files By Appvlp.Exe:
- Should execution of the specified files by Appvlp.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Files To Report:
-
Carbon Black App Control will report or block execution of the specified files by Appvlp.exe. You can add or remove items from this list. By default, the following is listed:
- *\wmic.exe
- Applications And Command Lines That Should Not Be Reported:
- Execution of these files by Appvlp.exe will not be reported or blocked.
Bginfo.exe
Use this group to specify how to handle suspicious behavior by Bginfo.exe.
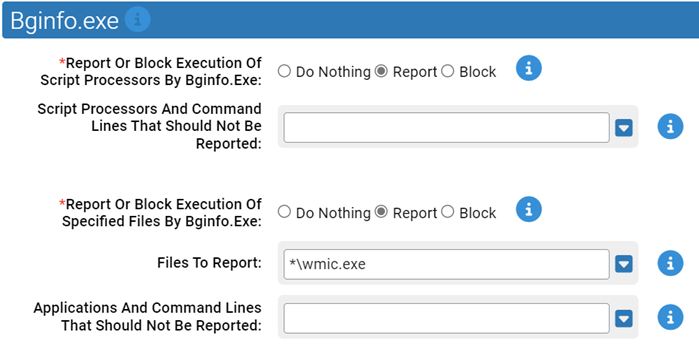
- *Report Or Block Execution Of Script Processors By Bginfo.Exe:
- Should execution of script processors by Bginfo.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Script Processors And Command Lines That Should Not Be Reported:
- Execution of these files by Bginfo.exe will not be reported or blocked.
- *Report Or Block Execution Of Specified Files By Bginfo.Exe:
- Should execution of the specified files by Bginfo.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Files To Report:
-
Carbon Black App Control will report or block execution of the specified files by Bginfo.exe. You can add or remove items from this list. By default, the following is listed:
- *\wmic.exe
- Applications And Command Lines That Should Not Be Reported:
- Execution of these files by Bginfo.exe will not be reported or blocked.
Dfsvc.exe
Use this group to specify how to handle suspicious behavior by Dfsvc.exe.
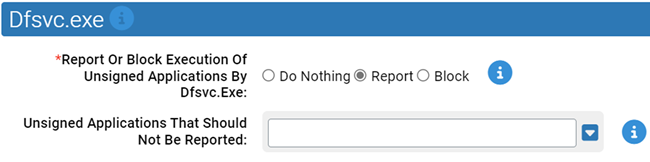
- *Report Or Block Execution Of Unsigned Applications By Dfsvc.Exe:
- Should execution of unsigned applications by dfsvc.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Unsigned Applications That Should Not Be Reported:
- Execution of applications specified here will not be reported or blocked.
Microsoft.Workflow.Compiler.exe
Use this group to specify how to handle suspicious behavior by Microsoft.Workflow.Compiler.exe.
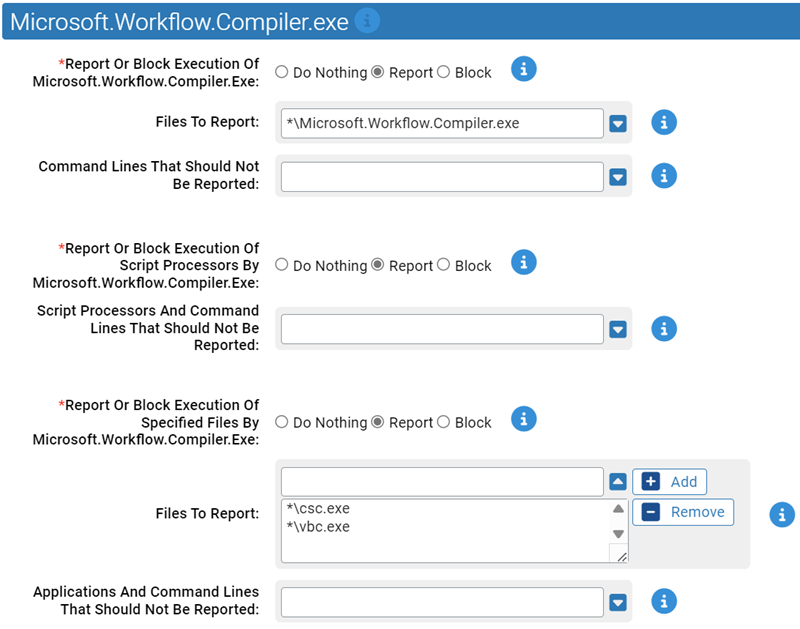
- *Report Or Block Execution Of Microsoft.Workflow.Compiler.Exe:
- Should execution of the Microsoft.Workflow.Compiler.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Files To Report:
-
Carbon Black App Control will report or block execution of the specified files. You can add or remove items from this list. By default, the following is listed:
- *\Microsoft.Workflow.Compiler.exe
- Command Lines That Should Not Be Reported:
- Execution of Microsoft.Workflow.compiler.exe command lines specified here will not be reported or blocked.
- *Report Or Block Execution Of Script Processors By Microsoft.Workflow.Compiler.Exe:
- Should execution of script processors by Microsoft.Workflow.Compiler.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Script Processors And Command Lines That Should Not Be Reported:
- Execution of these files by Microsoft.Workflow.Compiler.exe will not be reported or blocked.
- *Report Or Block Execution Of Specified Files By Microsoft.Workflow.Compiler.Exe:
- Should execution of the specified files by Microsoft.Workflow.Compiler.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Files To Report:
-
Should execution of the specified files by Microsoft.Workflow.Compiler.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking. You can add or remove items from this list. By default, the following is listed:
- *\csc.exe*\vbc.exe
- Applications And Command Lines That Should Not Be Reported:
- Execution of these files by Microsoft.Workflow.Compiler.exe will not be reported or blocked.
Msconfig.exe
Use this group to specify how to handle suspicious behavior by Msconfig.exe. Note that if msconfig.exe is started by Task Manager subsequent executions by msconfig.exe will not be reported/blocked.
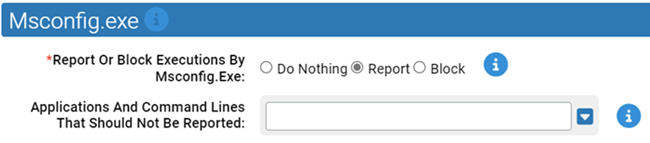
- *Report Or Block Execution By Msconfig.Exe:
- Should execution of applications by msconfig.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking. Note that if msconfig.exe is started by Task Manager subsequent executions by msconfig.exe will not be reported/blocked.
- Applications And Command Lines That Should Not Be Reported:
- Execution of applications or command lines specified here will not be reported or blocked.
Openwith.exe
Use this group to specify how to handle suspicious behavior by Openwith.exe.
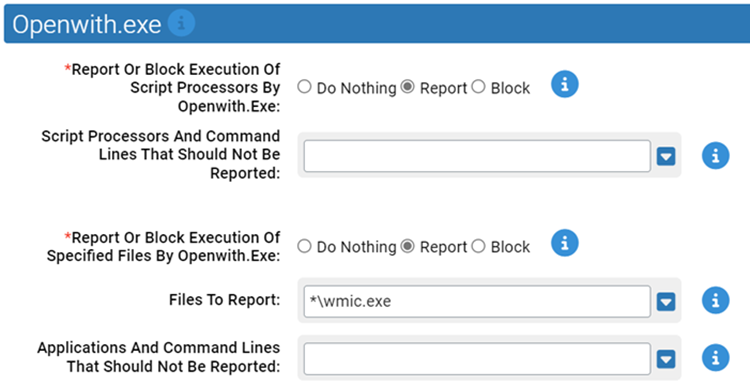
- *Report Or Block Execution Of Script Processors By Openwith.Exe:
- Should execution of script processors by Openwith.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Script Processors And Command Lines That Should Not Be Reported:
- Execution of these files by Openwith.exe will not be reported or blocked.
- *Report Or Block Execution Of Specified Files By Openwith.Exe:
- Should execution of the specified files by Openwith.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Files To Report:
-
Carbon Black App Control will report or block execution of the specified files by Openwith.exe. You can add or remove items from this list. By default, the following is listed:
- *\wmic.exe
- Applications And Command Lines That Should Not Be Reported:
- Execution of these files by Openwith.exe will not be reported or blocked.
Pcwrun.exe
Use this group to specify how to handle suspicious behavior by Pcwrun.exe.
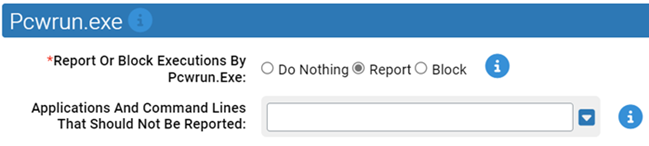
- *Report Or Block Execution By Pcwrun.Exe:
- Should execution of applications by Pcwrun.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Applications And Command Lines That Should Not Be Reported:
- Execution of applications or command lines specified here will not be reported or blocked.
Scriptrunner.exe
Use this group to specify how to handle suspicious behavior by Scriptrunner.exe.
- *Report Or Block Execution By Scriptrunner.Exe:
- Should execution of applications by Scriptrunner.exe be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- Applications And Command Lines That Should Not Be Reported:
- Execution of applications or command lines specified here will not be reported or blocked.