Purpose: To prevent the exploitation of Microsoft Office applications.
Description: Improve security by watching for suspicious behavior by Microsoft Office apps. Suspicious behavior includes spawning of other applications or creating executable file types.
| Enabled by Default: | No |
| Platform: | Windows |
| Minimum Agent Version Required: | 7.2.0 |
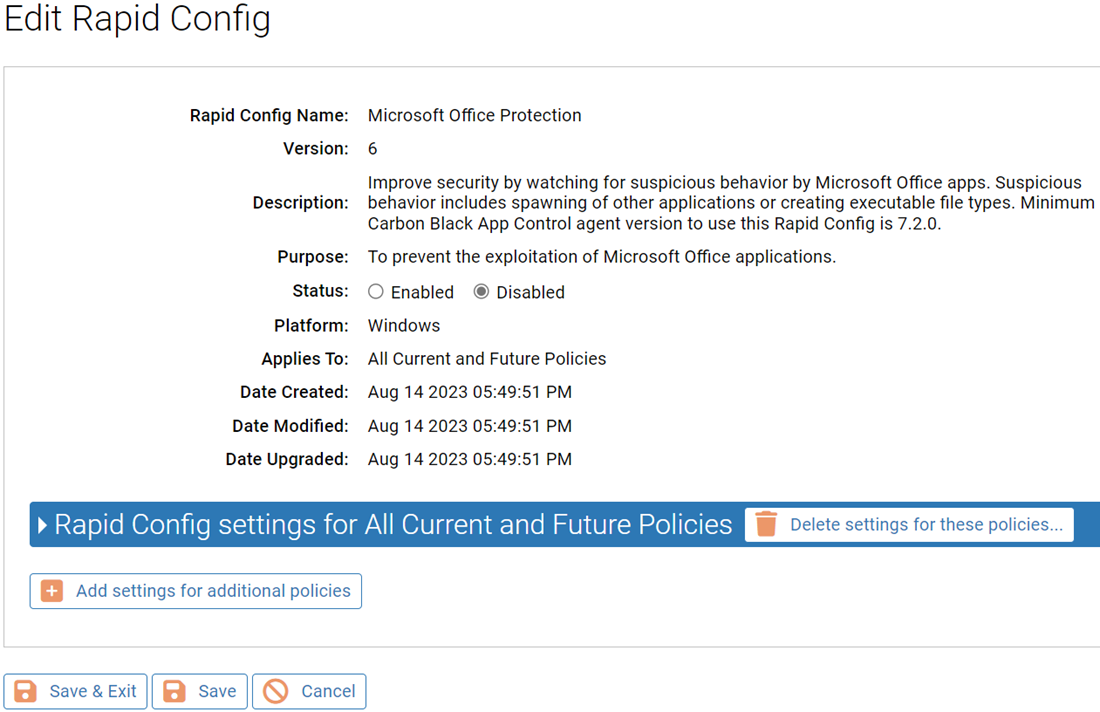
Rapid Config Settings
As with most rapid configs, you can:
-
Enable or disable the rapid config.
-
Specify what policies the rapid config applies to.
In addition, you can choose to Do Nothing, Report, or Block the specific items or behaviors. For each of the following sections, specify what action you require.
Note:
RECOMMENDATION: We recommend setting each section to
Report prior to setting to
Block. Use the resulting events to ensure that legitimate behavior will not be impacted.
Executions by Office Apps
Use this group to protect against Office Apps running other applications.
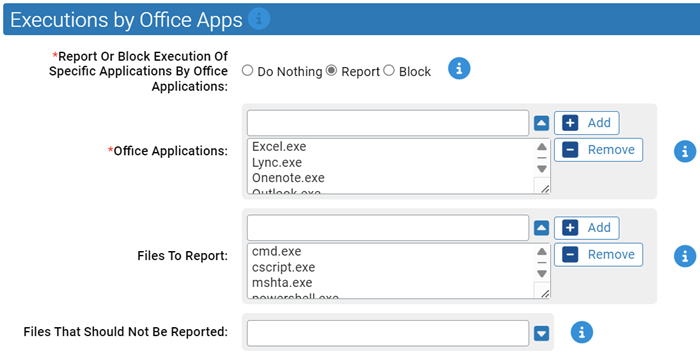
- *Report Or Block Execution Of Specific Applications By Office Applications:
- Should execution of the specified files by Office applications be reported or blocked? You should validate that legitimate execution is not blocked before enabling blocking.
- *Office Applications:
- Carbon Black App Control will report or block execution of specific files by these Microsoft Office applications. You can add or remove items from this list. By default, the list is:
- Files To Report:
- Carbon Black App Control will report or block execution of the specified files by Microsoft Office applications.
- Files That Should Not Be Reported:
- Execution of the files specified here will not be reported. You can add or remove items from this list.
Writes by Office Apps
Use this group to protect against Office Apps creating executable files.
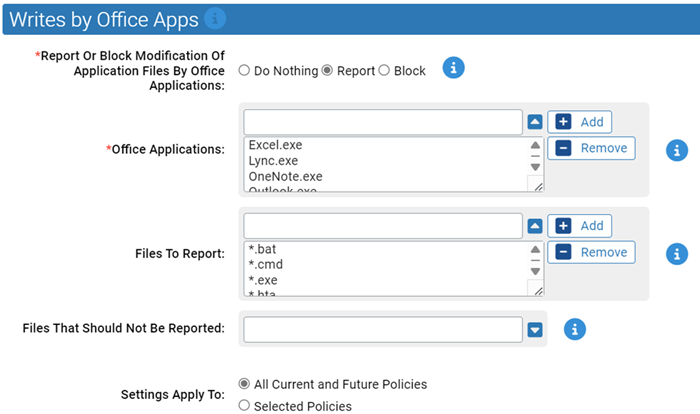
- *Report Or Block Modification Of Application Files By Office Applications:
- Should modification of the specified files by Microsoft Office applications be reported or blocked? You should validate that legitimate modification will not be blocked before enabling blocking.
- *Office Applications:
- Carbon Black App Control will report or block writes of specific files by these Microsoft Office applications. You can add or remove items from this list. By default, the files listed are:
- Files To Report:
- Carbon Black App Control will report or block modifications of the specified files by Microsoft Office applications. You can add or remove items from this list. By default, the files listed are:
- Files That Should Not Be Reported:
- Modifications to the files specified here will not be reported. You can add or remove items from this list.