| VMware Carbon Black App Control 8.10.0 | 27 JULY 2023 | Build 8.10.0.485 Check for additions and updates to these release notes. |
What's New
The 8.10.0 Server Release Notes provide information for users upgrading from previous versions as well as for users new to VMware Carbon Black App Control.
Server UI Refresh
The server has been refreshed with a new visual look and feel. The refreshed server utilizes the same functionality as previous servers, but now has all new colors, shapes, fonts, and logos. All console pages have been updated with a new responsive design allowing them to expand and compress to maximize the space of the browser window a page is being viewed in. In addition, server accessbility has been improved with updates to keyboard-only navigation and screen reader support. With these enhancements, users will benefit from a more pleasurable and accessible user experience on App Control.

Vulnerability Detection
The server now can identify CVEs (Common Vulnerabilities and Exposures) associated with Windows applications in an environment. The server displays CVEs in the new "CVE Instances" tab, on the Applications page. In this page, the server will display all CVE instances discovered through syncing with the National Vulnerability Database API. From this page, users can search and filter vulnerabilities by their CVE ID, CVSS Score (Common Vulnerability Scoring System), or other criteria of interest. In addition, users can also identify the specific machines the vulnerabilities are found on. Users can receive alerts about critical CVEs found in their environment as well. With this new feature, users can take additional steps to protect and secure their endpoints using the App Control Server.
.png)
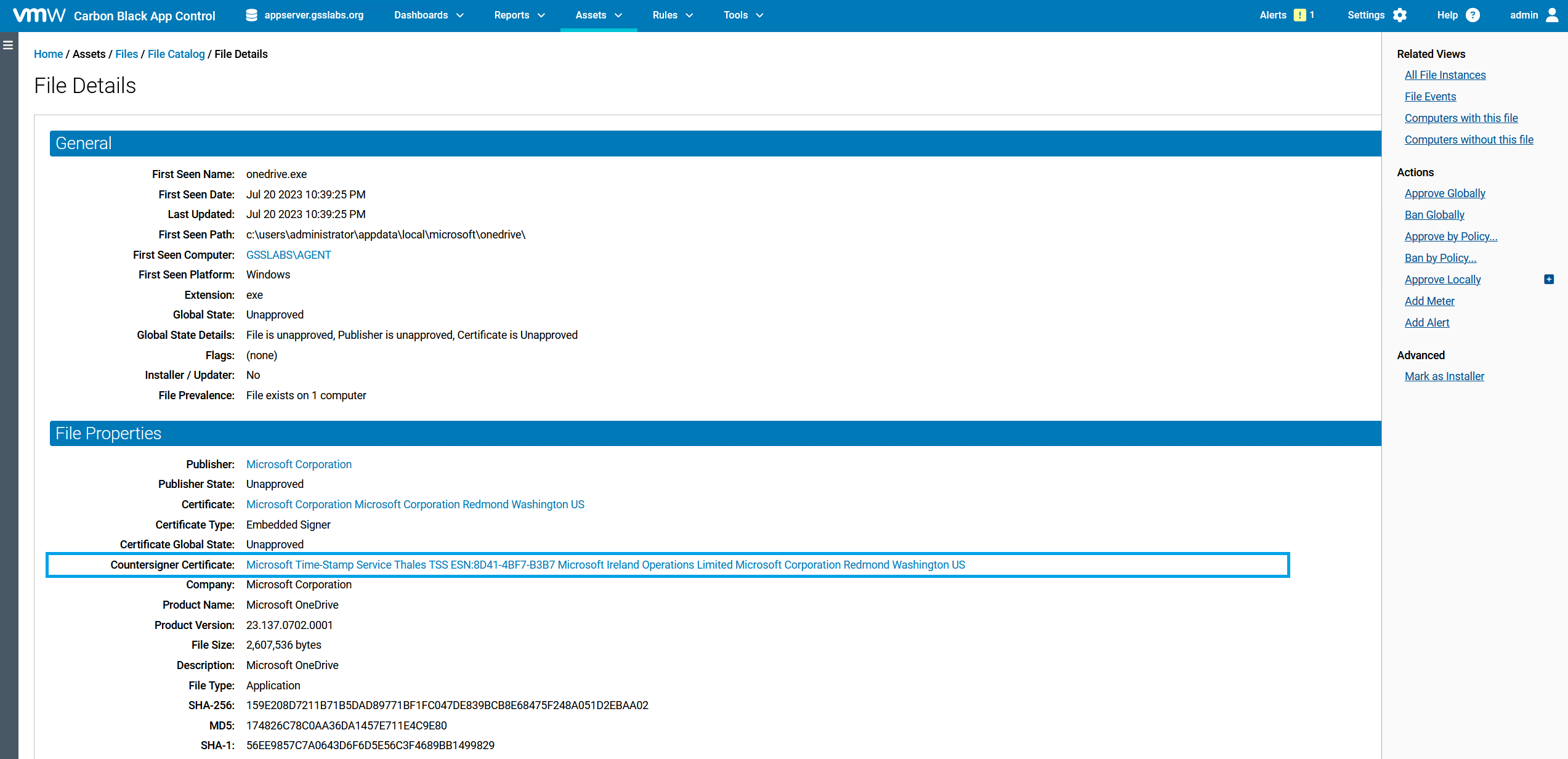
Countersigned Certificate Approval
The server now allows the approval of countersigned certificates from within the console. A new field has been added to the "File Details" page under "File Properties" that displays the name of a countersigned certificate, if it exists. Clicking on this field directs users to its respective "Certificate Details" page where the certificate's publisher can be found. The user can then approve the countersigned certificate publisher. This avoids the time-consuming process of approving a countersigned certificate manually on an endpoint.
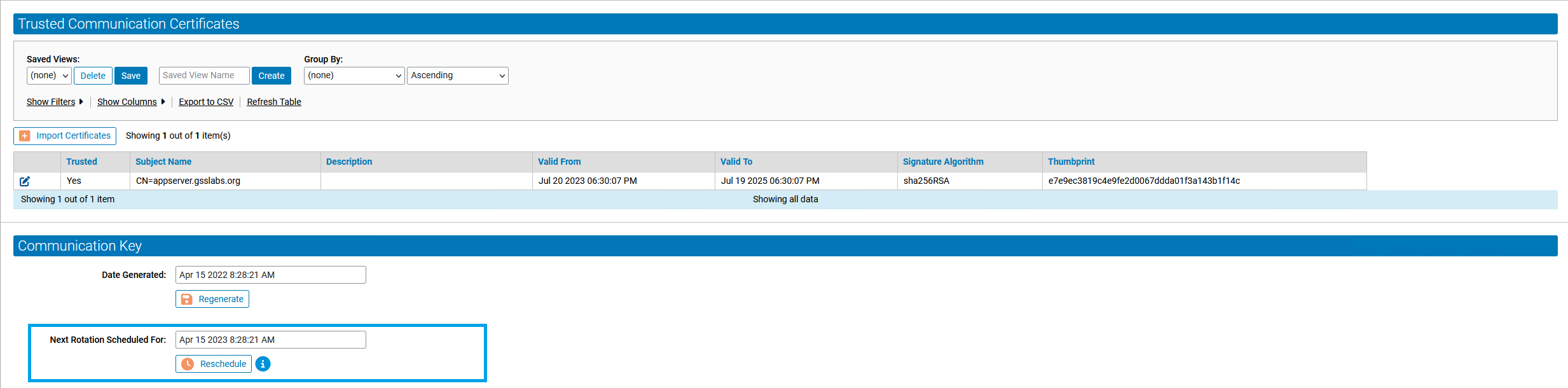
Communication Key Rotation Visibility and Scheduling
The server now provides users more visibility into the agent/server communication key rotation process. A new section has been added to the "Security" tab on the "System Configuration" page that displays the date the last communication key was generated and the next scheduled rotation. Users can now regenerate keys and reschedule future key rotations to their desired date. In addition, a new console alert has been created that notifies customers 5 days before an upcoming key rotation. This new feature is aimed to help users with air-gapped servers or alternative resource download locations to prepare for communication key rotations and provide flexibility around the process.
AD Managed Service Account Support
The server now can be installed and run on an Active Directory (AD) managed service account. AD managed service accounts are a more secure alternative to standard AD accounts. AD managed service accounts utilize more complex passwords not known by any users and are not stored locally. These passwords are also automatically changed every 30 days by default. Support for AD managed service accounts are for users who desire additional security around server management.
Additional Changes:
General Changes
-
Added support for MS SQL Server 2022
-
Added the ability to get v1/deviceInstance and v1/deviceSerialNumber by ID through the API.
-
Added support for negative anti-body and file name/path names IDs in server database tables which doubles the number of IDs that can be stored. This will help prevent the databases of large deployment users from filling up too quickly.
Common Platform Enumeration Changes
-
Moved the "Execution sync and matching now" button and date/time of last execution to a more convenient location on the "CPE Applications" page.
-
Added a configuration for an NVD API key for CPE users. Providing an NVD API key allows for faster data sync between the server and the NVD.
-
Added the ability to find files in the "File Catalog" by clicking on the magnifying glass icon next to items on the "CPE Applications" page.
-
CPE applications are now updated whenever the NVD API reports changes. This ensures CVE data is accurate and up-to-date.
-
Transitioned to NVD API 2.0 as the NVD API 1.0 is scheduled to be deprecated later this year.
-
Added a progress bar to show the completion of syncs between the NVD API and the console.
-
Made changes to improve the reliability of downloads from the NVD API.
Active Directory Changes
-
Modified the "User Role Mappings" tab to identify rules with a disabled user role. Removed the ability for users to save a mapping rule with a disabled user role.
-
User mappings for deleted user/roles are now deleted to prevent unauthenticated users from accessing the console.
UI Changes
-
Changed "trusted" filter to radio buttons on the "Trusted Communication Certificates" table on the Configuration > Security page.
-
Added the ability to double-click column names in "Column Settings" area of table data pages to move them to the left or right.
-
Reworded language to more clearly explain agent upgrade functionality in "Policy Settings" and "System Configuration".
Security Changes
-
Added password validation for Global CLI passwords. Previously, users could enter invalid passwords and they were accepted causing issues authenticating locally with agents.
-
Added a "Client Registration Code" section to the Security tab on the System Configuration page. This allows users to generate and manage registration codes to be used when agents register with the server.
Library Changes
The following libraries were updated:
-
Updated OpenSSL to version 3.1.1
-
Updated PHP to version 8.1.20
-
Updated curl to version 8.1.2
-
Updated libxml to 2.9.12
-
Updated PHP SQL Driver to 5.11.0
-
Updated jQuery UI library to 1.13.2
-
Updated Newtonsoft.Json library to version 13.0.3
-
Updated gSOAP library to version to 2.8.127E
-
Updated Smarty library to version 4.3.1
Supported Upgrade Paths
For customers using SQL 2019, installation of the latest Cumulative Update is required before installing version Carbon Black App Control Server 8.10.0. Please see the Server OER for more details.
The table below shows the supported upgrade paths for Carbon Black App Control 8.10.0 servers:
| Upgrading from: |
Upgrading to: |
|---|---|
| 8.9.x |
8.10.0 |
| 8.8.x |
8.10.0 |
| 8.7.x |
8.10.0 |
| 8.6.x |
8.10.0 |
| 8.5.x |
8.10.0 |
| 8.1.10 |
8.10.0 |
| 8.1.8 |
8.10.0 |
| 8.1.6 |
8.10.0 |
| 8.1.4 |
8.10.0 |
| 8.1.0 Patch 2 |
8.10.0 |
| 8.1.0 |
8.10.0 |
Resolved Issues
The following defects were fixed in the Carbon Black App Control 8.10.0 Server.
-
EP-16210: Fixed an issue where File uploads are not removed from the default upload location during daily pruning. (EA-21623)
-
EP-16525: Default timeout for CPE database operations increased from 120 seconds to 900 seconds.
-
EP-16854: Fixed subject name and expiration date issues for agent trust certificates.
-
EP-16967: Fixed an issue when editing an event rule that caused the page to scroll unexpectedly when adding event property filters
-
EP-17315: Fixed an issue where updating CPE configurations and pressing the sync button within 15 seconds would cause outdated configuration settings to be used.
-
EP-17349: Fixed issue with browsing OUs which have special characters in the OU name. (EA-22338)
-
EP-17352: Recreated two alerts - Rule Data Too Large and Critical CVE Detected so that they appear correctly in the UI.
-
EP-17394: Fixed a grouping issue in the Trusted Communication Certificates table related to the "Trusted" field.
-
EP-17524: Changed a database field to accommodate larger integers. (EA-17524)
-
EP-`17551: Fixed an issue deleting alerts.
-
EP-17590: Fixed an issue where some scheduled tasks would run on service restart.
-
EP-17592: Fixed an issue where the copy function on custom rules failed when the rule applied to specific policies. (EA-22449)
-
EP-17599: Fixed logic of smart search field on Computers page to use correct filter column on Return key press. (EA-22445)
-
EP-17601: The Certificate API no longer requires all fields to be sent in the request to modify an existing certificate. (EA-22255)
-
EP-17604: Fixed an issue to resolve AD Login issues that occurred after MS Patches were applied on App Control Server. (EA-22428)
-
EP-17684: Fixed an issue with the login of the AD user having a "\" in the DN. (EA-22686, EA-22269, EA-23362, EA-23050)
-
EP-17793: Fixed an issue where for remote-database installations, some valid account passwords caused installation failures. (EA-22528)
-
EP-17795: Fixed search filter on Tables pages when a search string ends with a backslash. (EA-22605, EA-23026)
-
EP-18016: Fixed an issue where CPE data was being missed while syncing.
-
EP-18038: Fixed an issue where AD domains were not recognized due to case-sensitive comparisons.
-
EP-18061: Minor UX change on the remove match dialog for CPE Applications.
-
EP-18143: Fixed an issue where the current server certificate would not be displayed if an invalid file was attempted to be imported.
-
EP-18464: In 8.8.2 some daily prune tasks were changed to do batch processing to improve transaction log usage. This however caused them to take much longer to execute in some cases. The default behavior is now reverted to how it used to be, and the batch processing mode is now optional just for those customers who may need it. (EA-23063)
-
EP-18909: Fixed a bug where clicking the filter icon on a "Status" cell on custom rules would filter by the wrong value under certain conditions.
Known Issues
The following known issues and limitations are present in the Carbon Black App Control 8.10.0 Server.
-
EP-1222: If the CryptoAPI cannot initialize, the license will not be imported
This is typically due to the environment not being set up according to the installation instructions.
-
EP-2752: If you modify the permissions of, or disable, the "admin" user that ships with the product, the API module may no longer function correctly, causing problems when using the REST API and the console
Make sure that the "admin" user retains its "View users" and "Manage users" permissions, and that it is not disabled.
-
EP-2879: Baseline Drift Reports only report on Windows computers
Baseline Drift Reports do not report on Mac or Linux computers.
-
EP-3157: Exports to CSV of tabular data from console pages do not render date and time fields consistently with respect to time zone
Some columns are reported as UTC; others use the local time zone.
-
EP-3349: Right after a new version of App Control is installed, the version health indicator will incorrectly report that the previous version is the newest version
Refreshing the health indicator will cause it to disappear and will remove the incorrect report.
-
EP-3352: An event with the subtype "File deletion failed" is erroneously generated when a file that no longer exists is selected for deletion
When a file that no longer exists is selected for deletion, the App Control Server should generate an error with subtype "File deletion processed (file not found)". Instead, an event with the subtype "File deletion failed" is erroneously generated.
-
EP-4085: When uninstalling the App Control server a message may appear saying that the system is protected by the App Control agent even though the agent has already been uninstalled
-
EP-4094: Users without the "View Policies" permission will not be able to make use of Role-Based Access Controls based on policies
-
EP-4578: If a user turns on the config property ShowHiddenCustomRules and creates a Custom Rule with a hidden action (that is, an action ending with "(Hidden)") that rule will display as an expert rule after being saved
Rules of this type requiring an Operation value of "Execute and Write" should be created as two separate rules to avoid losing data.
-
EP-5504: Systems created using Sysprep may not boot if Tamper Protection was enabled when Sysprep was performed
-
EP-5703: Canceling a diagnostic request while it is underway does not always work
From the App Control console one can request a diagnostic upload from an endpoint. Canceling such a request while it is underway does not always work. Sometimes cancellation can merely cause the endpoint to retry the upload.
-
EP-6510: Some customers have reported seeing false positives with the Doppleganger rule being triggered by TIWorker.exe and TrustedInstaller.exe
-
EP-6515: In a specific scenario it's possible for newly installed agents to register with the server from a deleted policy
-
EP-6719: File analysis through connectors will not work with files containing certain foreign characters in the name
-
EP-6721: If a SAML identity provider requires a signed logout request, the logout request will fail
-
EP-6796: In some cases it's not possible to export a large amount (300+) of custom rules
-
EP-7891: When adding a user to the "Linux User/Group to Manage Agents" section of the Agent Management configuration the message “(Not validated)” is erroneously returned
The new user should still be added.
-
EP-13195: Rapidly changing a computer's policy more than once can sometimes cause the last policy change to not apply
-
EP-14702: Due to an InstallShield issue, if a reboot is required during install, the installer may not automatically continue after reboot
If this occurs, you must manually restart the install.
-
EP-16158: Incorrect list of files when creating a snapshot
Sometimes when filtering files and creating a snapshot from the result set, files not part of the result set are included in the snapshot.
-
EP-17537: When running on Windows Server 2012 R2 the AppC Server is unable to access the NIST API due to incompatible cipher suites. Because of this, CPE syncing is not possible on this operating system
-
EP-19103: On the Requested Files > Diagnostic Files page, logs for rules and host package installers may download empty files due to OS permission issues