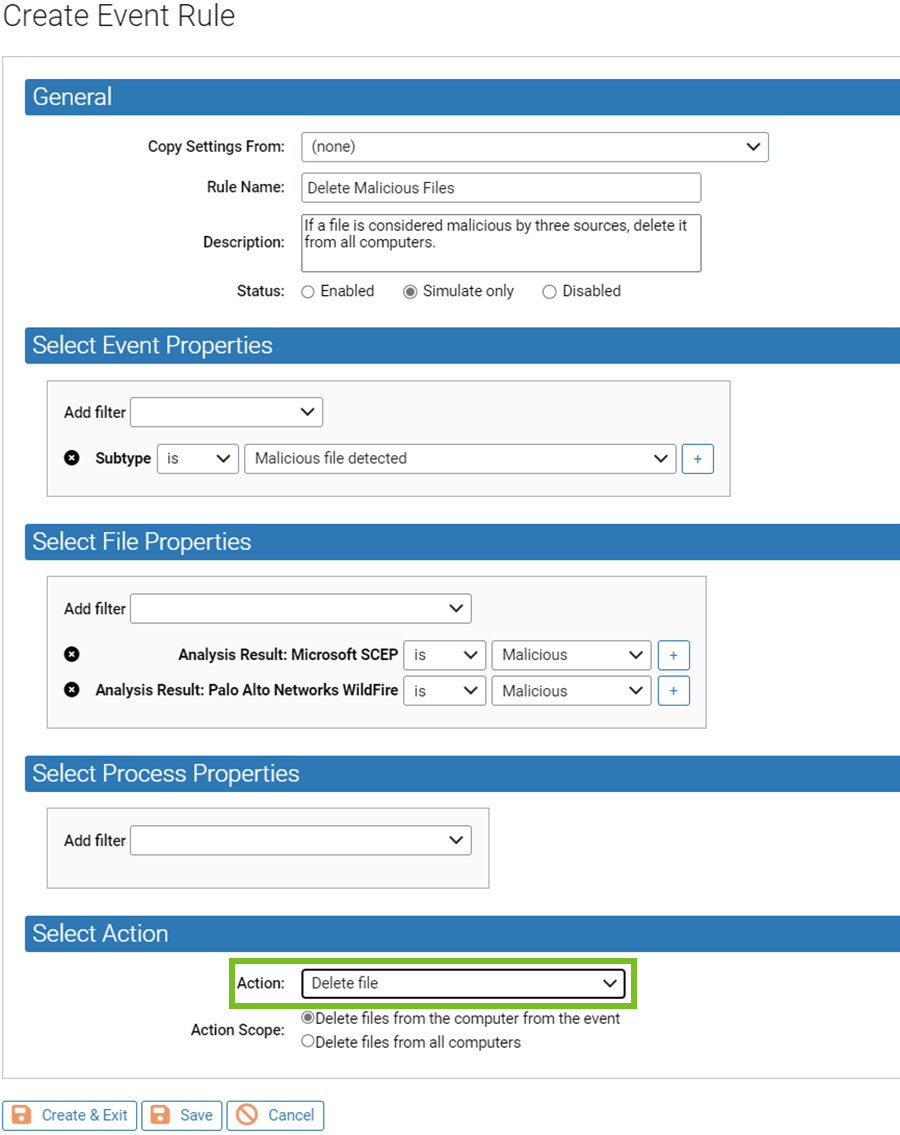
You can create Event Rules that will automatically delete files when certain events occur, such as a report of a malicious file.
Unlike deletions done using commands, Event Rule deletions have no confirmation dialog. If an event matches the rule, the files specified in the rule are immediately scheduled for deletion, without feedback on the console. You can, however, create Alerts that inform you when a file deletion is requested or completed.
Event Rules that delete files do offer you the same scope options as delete commands: you can either delete all instances of a file on one computer or you can delete all instances of the file from all computers.
Create Event Rule that Deletes Files (example)
Use this procedure to create an Event Rule that deletes files. This is an example of how to do an automated file deletion request.