Event Rules allow you to take certain actions when events matching the rule definition occur.
This feature offers an automatic way to respond to threats, even if you haven’t reviewed them on the Events page. Although you normally cannot automatically ban files using an Event Rule, you can take other actions that might be useful for reported threats:
- Remove Approval from Suspicious Files – You can use event rules to automatically remove local or global approval from files matching the rule parameters.
- Send Suspicious Files for Analysis – If you have used the Carbon Black App Control Connector to integrate an external analysis appliance or service, you can create an event rule that sends files reported as threats for external analysis. For example, in the following illustration, files reported in threat events that are not already banned are sent to WildFire for analysis. This action can provide more information that might influence your decision to block or not block a file.
- Create a Ban – You can define an event rule that bans any file included in a threat event triggered by an ATI. You can also create a Report Only ban that will generate an event telling you that a file would have been blocked if the Ban was fully activated.
- Delete Files – You can define an event rule that deletes any file included in a threat event triggered by an ATI.
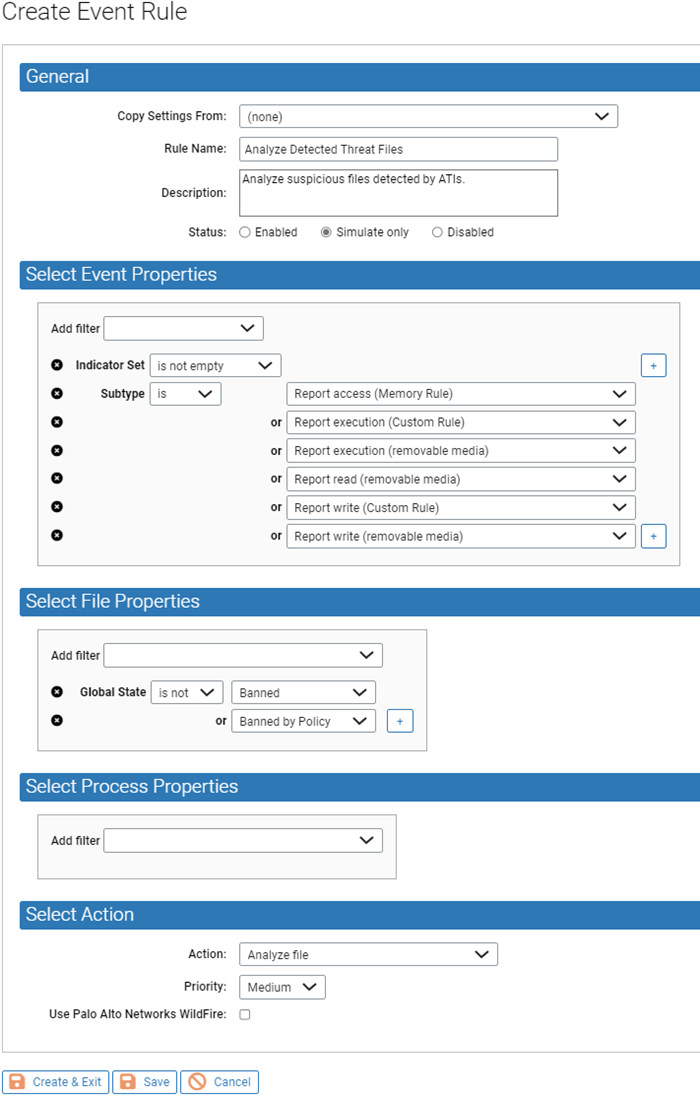
See Event Rules for more information about creating and editing event rules.