Threat-related events are exported to Syslog together with other Carbon Black App Control events.
To determine what to filter or search for in Syslog, you can select one of the threat views and review the Rule Names shown in the table to see the specific rules that generated an event. You also can search for any event in Syslog that contains an Indicator Name field (“indicatorName” in raw output, mapped to different strings depending upon Syslog format), which identifies it as a threat detection event. For these events, Indicator Name is the same as Rule Name.
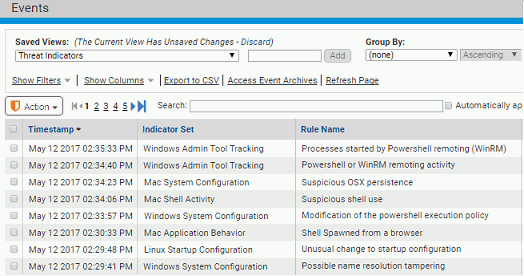
One search approach is to filter Syslog output to show only the event subtypes that begin with "Report " (except for "Report execution block") – these are the subtypes for threat-related events. To see the specific list of event subtypes for an Events page view, you can choose the view from the Saved Views menu and then click on Show Filters.
See the VMware Carbon Black App Control Events Guide for more information on the Syslog output available from the Carbon Black App Control Server.