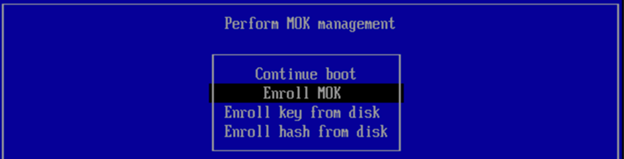
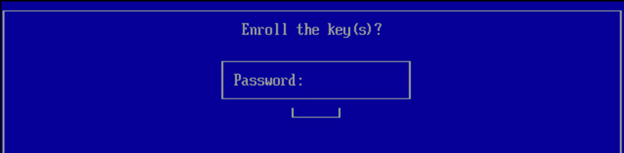
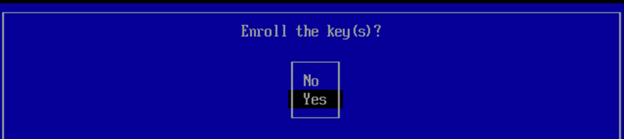
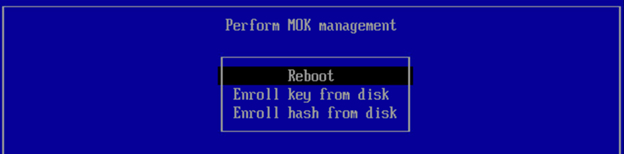
You can use this procedure to enable secure boot on a Carbon Black App Control Linux Agents. This feature is available only on agent version 8.8.0 and subsequent versions.
Prerequisites
- Download the public key used for signing App Control agent kernel modules.
- Log into the Broadcom customer portal and then select Cyber Security Software from the drop-down at the top of the page.
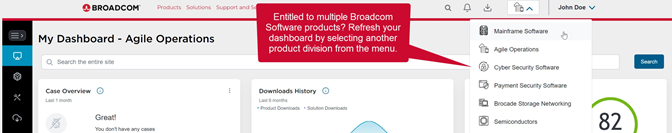
- Select My Downloads from the menu on the left to see the list of products that you are entitled to download for the selected division.
Important: If you do not see the product you are looking for in your download list, you should contact Broadcom's Global Customer Assistance. Do one of the following:
- Call the support number here: https://support.broadcom.com/web/ecx/contact-support
- Fill out this form: https://broadcomcms-software.wolkenservicedesk.com/web-form
- Navigate to, or search for the Carbon Black App Control Linux Agent and then select the Agent you need to download.
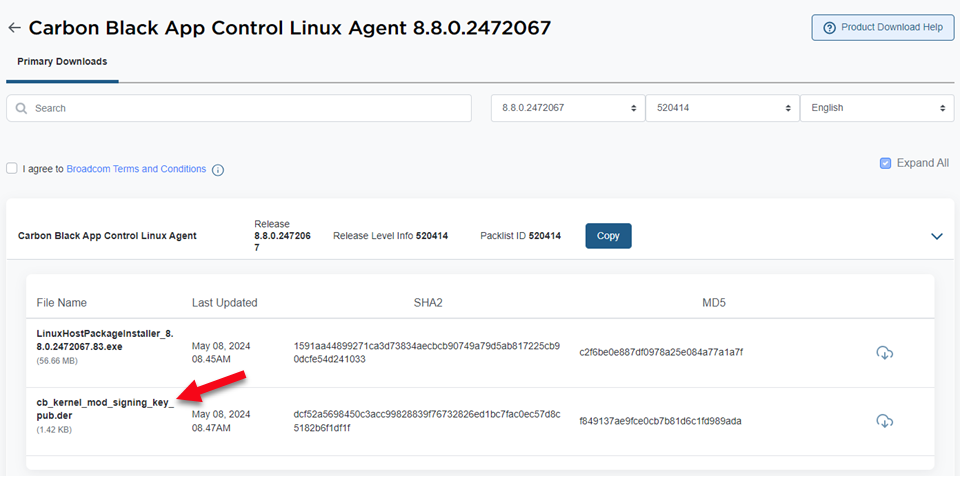
The public key required to sign the App Control Linux Agent kernel modules is included in the Linux Agent package.
In the example image below, you can see that the App Control Linux Agent 8.8.0 package contains both the installer package and the required signing key, cb_kernel_mod_signing_key_pub.der, along with required SHA2 keys.
- Log into the Broadcom customer portal and then select Cyber Security Software from the drop-down at the top of the page.
- Download cb_kernel_mod_signing_key_pub.der.
- Import the public key on the endpoint to authenticate and load agent kernel modules.
- Install the Carbon Black App Control Linux Agent. See: Install Linux Agents on Endpoints.
Tip: For additional assistance with downloads, see:
Product Download Help.