Use this procedure to encrypt your AWS S3 bucket using your customer managed AWS KMS key.
Prerequisites
This procedure requires that you have created a customer managed KMS key. If necessary, see: Create a Customer Managed KMS Key
Note: This procedure was written from the perspective that you have already created and configured your S3 AWS bucket. This is not a requirement and you can create and configure the S3 bucket and perform this task similtaneously. If necessary, see:
Create an S3 Bucket in the AWS Console
Procedure
- In the AWS Management Console, navigate to the S3 bucket you want to encrypt and then select it.
- Select the Properties tab and scroll down to the section, Default encryption.
- In the Default encryption page:
- For Server-side encryption, select Enable.
- For Encryption key type, select AWS Key Management Service key (SSE-KMS).
- For AWS KMS key, select, and define if necessary, one of the following:
- AWS managed key (aws/s3)
- Choose from your KMS master keys
- Enter KMS master key ARN
- For Bucket Key, select Enable.
Note: Enabling the Bucket Key is NOT mandatory.
AWS recommends using a Bucket key for cost reasons and support of KMS with the Data Forwarder was validated using this recommendation.
If you choose not to enable Bucket Key, there are no known, negative impacts on Data Forwarder.
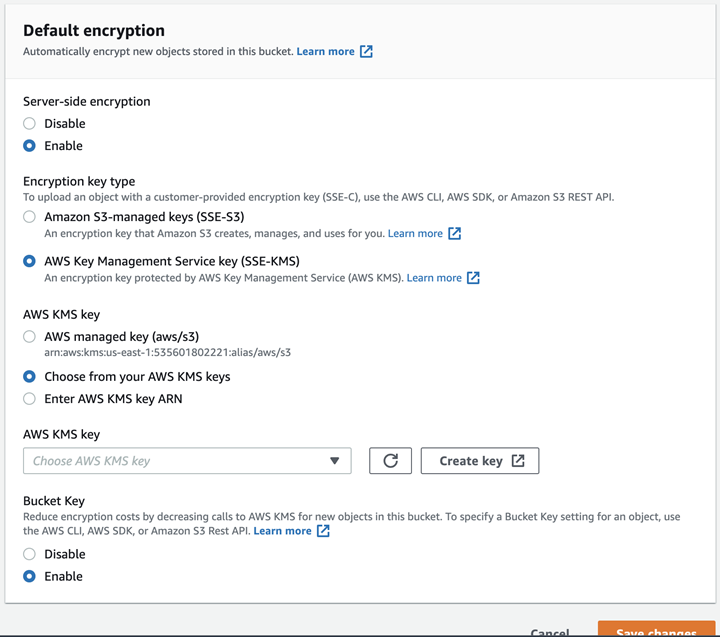
- Click Save Changes.
Results
The AWS S3 bucket is now encrypted using a methodology supported by Carbon Black Cloud Data Forwarder.
