To better understand how recommendations work, this section describes how the Carbon Black Cloud generates Hash and IT Tools recommendations.
How does Carbon Black Cloud generate Hash recommendations?
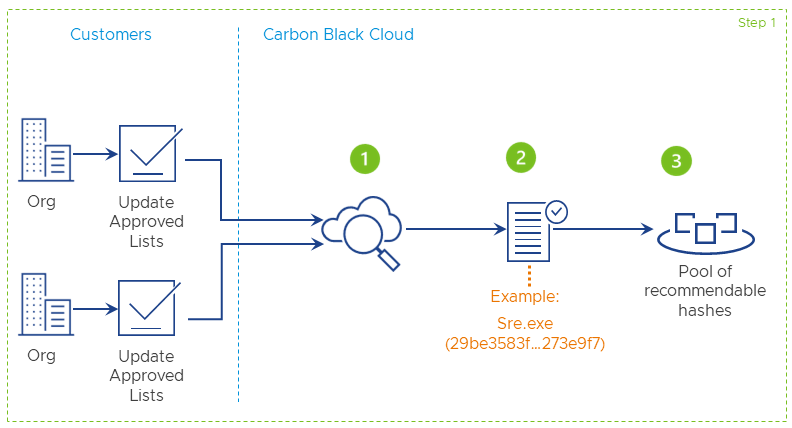
First, the Carbon Black Cloud looks in every single organization within your environment for the rules the organization has in its approved list of reputations. It analyzes all hash entries present in the approved lists across different organizations. Then, Carbon Black checks the reputation of each hash to make sure it belongs to the approved list. Finally, it uses the data to create a pool with potentially recommendable hash rules (good recommendations).
Once the pool is present, the Carbon Black Cloud looks at each organization and analyzes all sensor action events that are happening in your environment. It cross-references the observed hashes with the pool of good recommendations and uses the available data to generate recommendations and apply them to your account. The Carbon Black Cloud console lists the recommendations that rank in priority by the number of sensor action events that apply to your account - the greater the number of sensor actions, the higher the priority.
Hash sample: Sre.exe (29be3583t...273e9f7)
 |
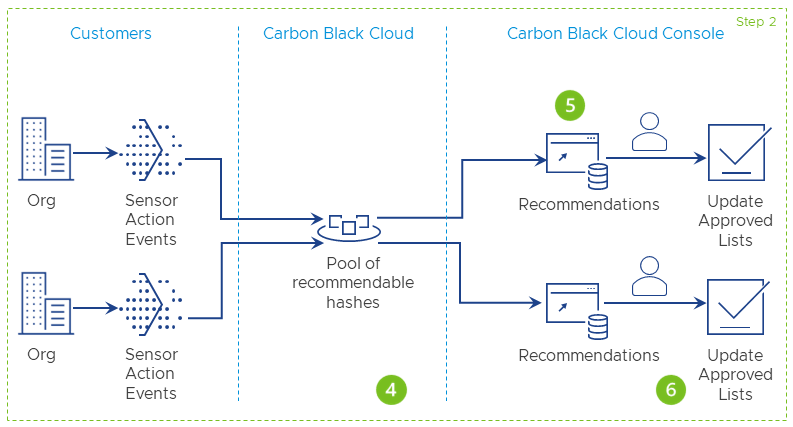 |
For example, the greater the number of sensor actions is, the higher the priority. |
How does Carbon Black Cloud generate IT Tools recommendations?
The Carbon Black Cloud generates the IT Tool recommendations from a list of approved tools maintained by our Threat Research team. Then, the Recommendations feature analyzes sensor actions and matches observed applications with a list of trusted IT Tools. From there, the Carbon Black Cloud console generates a list of recommendations ranked by the number of sensor actions associated with the tool. Finally, the recommendations are presented to the user to choose whether they want to add the process to the Approved list.
IT Tool sample: c:\program files\dell\supportassistagent\sre\sre.exe
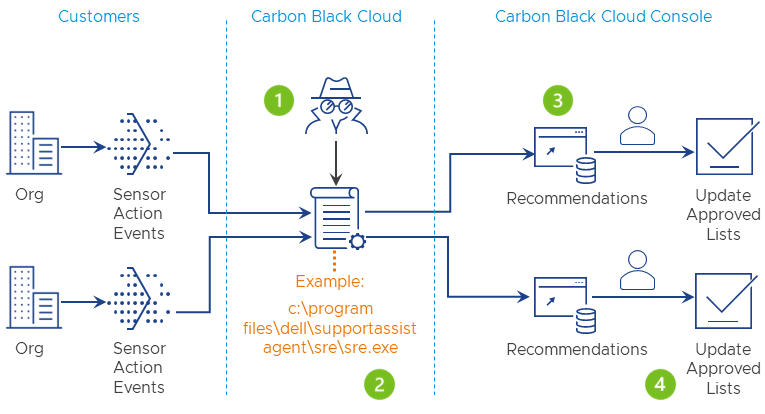 |
For example, the greater the number of sensor actions is, the higher the priority. |