Cluster image scanning helps you identify and classify discovered software by comparing it to an extensive database of known files.
As a security admin, you can use image scanning file reputation functionality to analyze all Linux ELF files of a specific container image against a list of known malicious files.
As a DevSecOps, you can view the suspicious/malicious file reputation for all deployed container images in your cluster.
Procedure
- On the left navigation pane, do one of the following depending on your system configuration and role:
- If you have the Kubernetes Security DevOps or SecOps role and your system has only the Container security feature, click .
- If you have any other role and your system has Container security and other Carbon Black Cloud features, click .
The Container Images page contains a general summary of what is currently happening in your Kubernetes environment. The File Reputations widget summarizes all reputations for deployed container images in a bar chart.
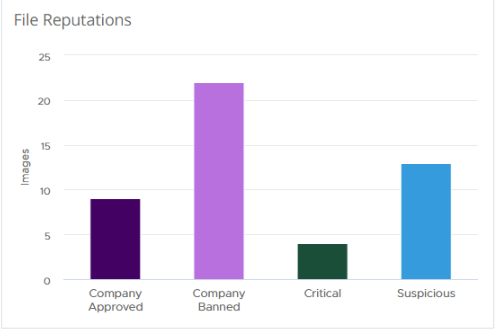
This visualization reveals the number of images running with suspicious files and their distribution by reputation.
- Company Approved — indicates the file is added to the Company Approved List through the SHA-256 hash.
- Company Banned — indicates the file is added to the Company Banned List through the SHA-256 hash.
- Critical — indicates the file is a known malware. Cloud analytics and threat intelligence feeds determine the known malware reputation.
- Suspicious — indicates the image file is a suspected malware. Cloud analytics and threat intelligence feeds determine the suspect malware reputation. The analysis cannot determine if the file is good or a malware.
- To further investigate the level of trust or distrust that the file reputation assigns to the files in container images:
- Click the Deployed Images tab and then click the arrow
 icon to the right of the image row.
icon to the right of the image row.The File Reputations section in the Image Details panel lists all interesting files in the container image and their assigned reputations.
- In the Deployed Images tab, click the link under the Image Tag column for that container image.
The File Reputations widget displays in the Overview tab of the Container Image page. It shows the distribution of suspicious and malicious files for that image in a pie chart.
- In the Container Image page, click the Layers tab and double-click a layer row.
In the File Reputations section, you can view the filename and reputation.

 icon to the right of the image row.
icon to the right of the image row.