With Carbon Black Container, Security and DevOps teams gain full visibility into Kubernetes environments to proactively harden workloads and better identify and reduce the risks posed by vulnerabilities and misconfigurations. Organizations can use the image repository to take inventory of the risks associated with an image, and directly align that vulnerability with a running workload.
Security Posture Dashboard
A single pane of glass provides complete visibility into your security posture across Kubernetes clusters or applications, including:
- Visibility into Kubernetes clusters and workload inventory.
- A combined view of all vulnerabilities, misconfiguration, and rules violations.
- A consolidated risk score aggregated for all workload attributes to prioritize remediation.
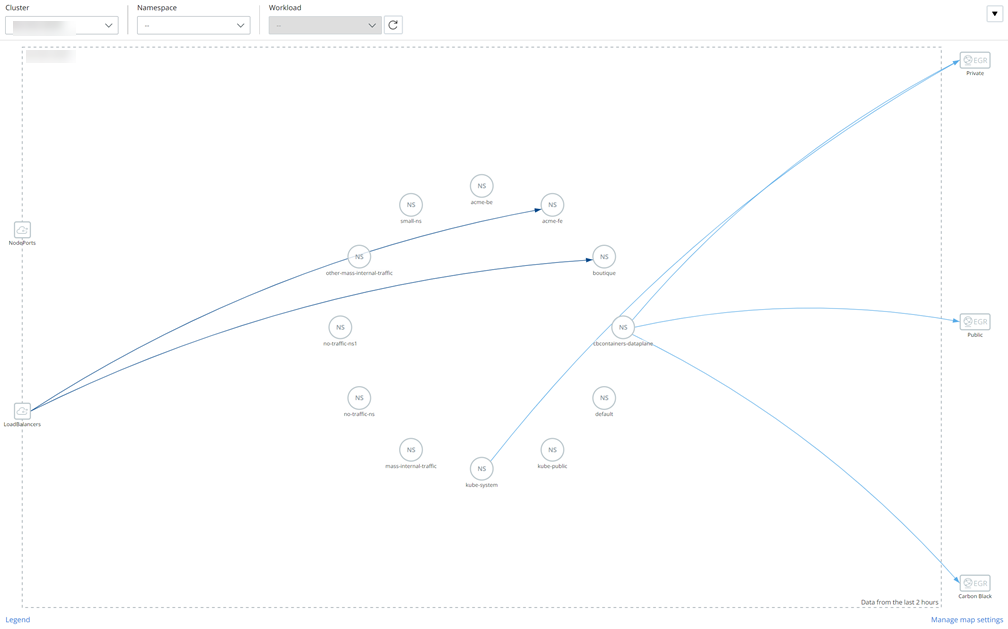
Network Map
The network visibility map lets you view workload connections in a single map of the application architecture. The network visibility map provides detailed information and context to better understand the application architecture and network traffic behavior.
To get a clean view of an application, filters allow the connectivity of the map to remove unnecessary noise such as system namespaces. You can use similar filters to better understand what connection is encrypted or not encrypted to gain full visibility into your application traffic posture. The goal of the networking visibility map is to give teams a better understanding of the connectivity and configuration of applications that are installed in the Kubernetes cluster.