To set up a CLI instance for image scanning, perform the following procedure.
Add configured CLI instances to enable local scanning of images, workload vulnerability assessment, and CI integration. The CLI instance scans container images and reports their health to the Carbon Black Cloud console.
Procedure
- On the left navigation pane of the console, do one of the following depending on your system configuration and role:
- If you have the Kubernetes Security DevOps or SecOps role and your system has the Containers Security feature only, click .
- If you have any other role and your system has Container security and other Carbon Black Cloud features, click .
- Click the CLI Config tab.
- In the upper right of the page, click Add CLI.
- Enter a unique name for this CLI instance (different from the API key name).
Use lowercase characters, numbers, and hyphens only. The name helps identify and manage the CLI in the console.
- Enter the build step name (for example, development, production, compliance) to be used as the default field for CLI runs.
Build steps are used as reference IDs in build-phase scopes to establish a connection with related configured CLIs. The build step parameter is used to match a scope in
Carbon Black Cloud, and consecutively to apply the policy for that scope. The default scope is stored in the configuration file.
Note:
- The default build step is not unique. Multiple CLI instances can use the same default scope. The Default build step cannot be modified after the initial setup, unless you directly edit the configuration file.
- If a scan is invoked without a build step parameter, the default build step from the configuration file is used.
- Create a Build Phase scope using this value on the Kubernetes > Scopes page in Build steps. See Kubernetes Scopes.
- You must use the CLI
validate command.
- Add an optional description (recommended).
- Click Next.
- Enter a unique API key name and click Generate.
- Click Next.
- Copy and run the following command in your terminal window.
mkdir -p ~/.cbctl
cat > ~/.cbctl/.cbctl.yaml <<EOF
active_user_profile: cbctl_default
cbctl_default:
cb_api_id: UHSZCDKMI1
cb_api_key: 4AYGEJ1T9ILZTQ6VZG9TTEH8
org_key: EWRTY2PK
saas_url: https://defense-dev01.cbdtest.io/containers
default_build_step: ix-test
EOF
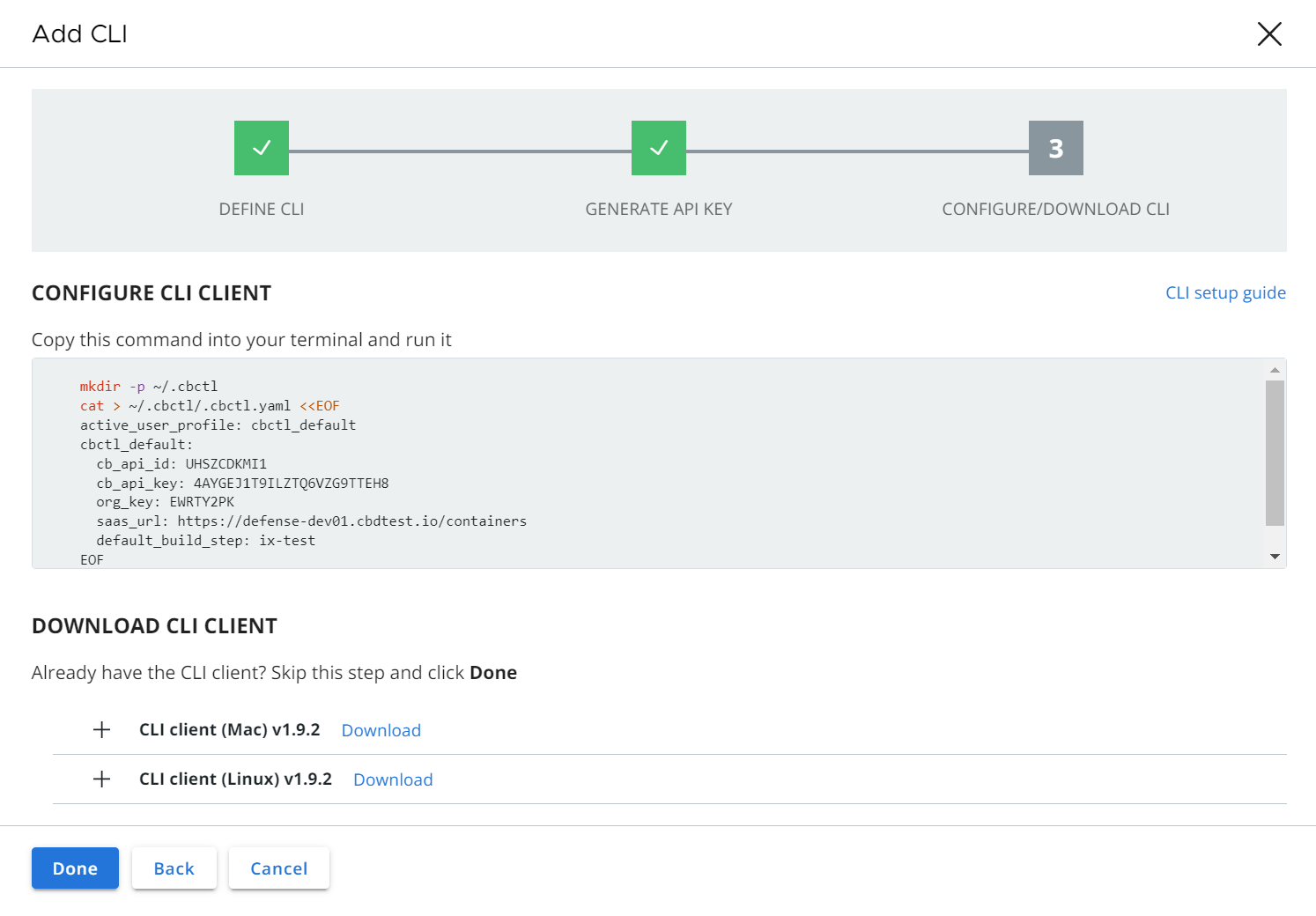
- If you did not already download the CLI client, you can select and download the CLI instance binary file now, and run it in your build environment.
- Click Done.
Results
You can operate the configured CLI Client in a terminal to observe the results from vulnerabilities scans on your container images.
What to do next
To run the Image Scanning CLI API, see Container Security API and Integrations.
To monitor the Vulnerabilities scan for container images that are deployed on Kubernetes, go to the page.
To see the image scanning results for container images that are in particular repositories but not yet deployed, go to the page and click the Image Repos tab.
