This topic describes netconn data that you can retrieve in the Carbon Black Cloud Console. It also introduces Intrusion Detection System (IDS) to identify and classify netconn traffic, and Network Traffic Analysis (NTA) to determine anomalies.
Netconn Data
XDR analyzes network connections (netconn) and makes these analyses visible for threat hunting and investigations. For a list of netconn fields that you can search on, see XDR Search Fields.
Observation data types are available for filtering and sorting. For descriptions of observation types, see Investigate - Observations.
- CB Analytics
- Contextual Activity
- TAU Intelligence
- Tamper
- Blocked Hash
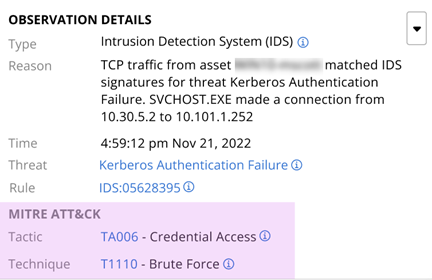
- Intrusion Detection System
- Network Traffic Analysis
- Host-based Firewall
- Indicator of Attack
Intrusion Detection System (IDS)
The MicroIDS network classification engine runs on netconn events and uses IP packets to classify connections. This engine is embedded in the Carbon Black Cloud 3.9+ Windows sensor.
IDS provides the following benefits:
- Monitors inbound and outbound network traffic
- Monitors data that moves between the system and the network
- Detects attacks by capturing and analyzing network packets
- Identifies abnormal network traffic
Intrusion Detection System is a filter option on the Alerts, Processes, and Observations pages.
Network Traffic Analysis (NTA)
Network Traffic Analysis (NTA) monitors network availability and activity to identify anomalies. Benefits of NTA include:
- Improved visibility into your network by providing rich context
- Detecting anomalous actions
- Assisting in security triage investigations
Data extracted from network packets can help you track usage and monitor for suspicious behavior.
For example:
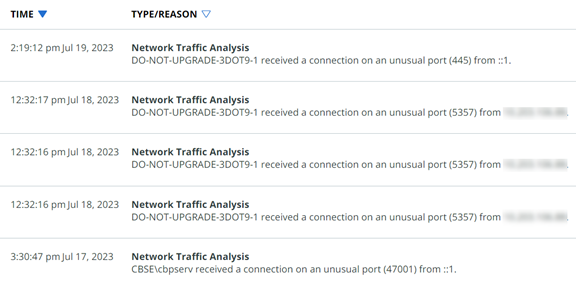
Carbon Black shows the following types of NTA detectors:
| Alert Type | Description |
|---|---|
| IP Profiler | Looks for connections to or from a local host that have an unusual remote IP address, compared to remote IP addresses to which the host typically connects. |
| User Agent Profiler | Looks for unusual HTTP user agents in connections that are made from a local device, compared to previous device activity. |
| Port Profiler | Looks for unusual port activity on either end of a network connection. This alert type includes four variations:
|
| JA3 Profiler | Looks for unusual JA3 hashes of SSL/TLS connections that are made from a local device, compared to previous device activity. |
Network Traffic Analysis is a filter option on the Alerts, Processes, and Observations pages.
MITRE ATT&CK Tactics & Techniques
MITRE ATT&CK® is visible throughout the Carbon Black Cloud console as well as in XDR; it is not XDR-specific.
MITRE ATT&CK is widely adopted by the security industry as a knowledge base of adversarial tactics and techniques. For more information about MITRE ATT&CK, see MITRE ATT&CK (external link).
A Tactic represents the purpose behind a technique. For example, a MITRE ATT&CK Tactic ID of TA0001 signifies that the adversary is trying to penetrate your network.
A Technique expresses how the adversary is attacking. For example, a MITRE ATT&CK Technique ID of T1548.003 indicates that adversaries are performing sudo caching to elevate privileges.
You can filter, search, and sort on Tactic and Technique fields on the Observations, Alerts, Processes, and Process Analysis pages. For example:
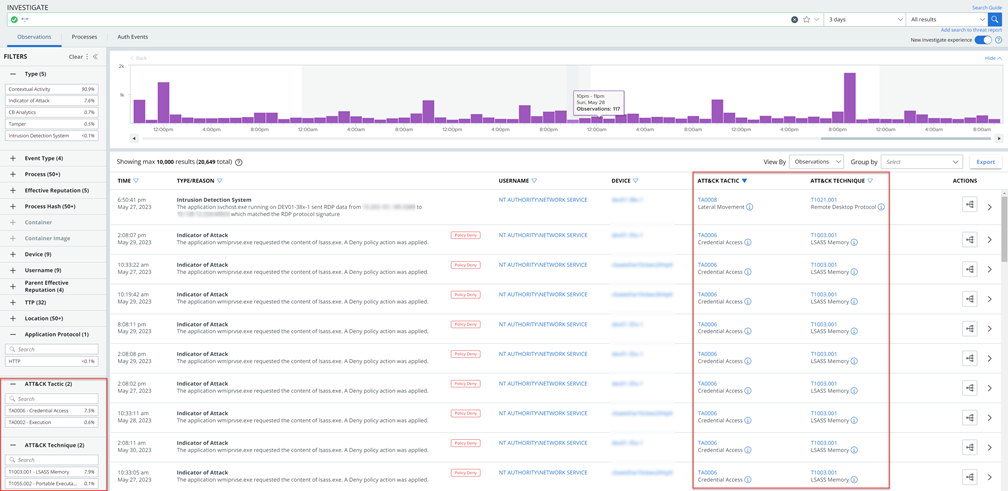
- To show both the Tactic and Technique columns in the table on the Observations and Alerts pages, click Configure Table at the bottom left of the table.
- Click the Information icon to view a brief synopsis of the tactic or technique. Within the Information pane, you can click Learn more to go to the MITRE web site for more information.
- MITRE ATT&CK tactics and techniques display in the Observation Details pane on the Observations, Alerts, and Alert Triage pages.