| VMware Carbon Black Cloud 3.7.1.12 | 14 JUN 2022 | Build 3.7.1.12 Check for additions and updates to these release notes. |
What's New
VMware Carbon Black Cloud macOS Sensor 3.7.1.12 includes improvements and bug fixes.
Important notes
Carbon Black Cloud macOS 3.7.1.12 will be deprecated by January 9, 2023. We highly recommend upgrading to 3.7.1.17 at your earliest convenience. Please see 3.7.1.17 Release Notes and UEX announcement for more details.
This release supports macOS 10.15 - 12.5. Please refer to the macOS support link under Resources for more details.
Resources
Release checksums
| 3.7.1.12 DMG SHA256 Checksum |
bc7c42179e57bc32042c88fdad05640acbdb160be63ce524a0584af8588b3fea |
| 3.7.1.12 PKG SHA256 Checksum |
72a1106a3e433f12cd965788eb154e2739b43c4a3d92141da36fa156954ec88a |
Supported operating modes
| Supported Operating System |
Supported Modes and Architectures |
|---|---|
| macOS 10.15 (Catalina) |
Kernel Extension (Intel only) |
| macOS 11 (Big Sur) |
Kernel Extension (Intel only) System Extension (Intel, Apple Silicon) |
| macOS 12 (Monterey) |
System Extension (Intel, Apple Silicon) |
-
macOS Monterey support
Sensor version 3.7.1 supports operation on macOS Monterey via System Extensions. Legacy Kernel Extension mode operation is not supported on macOS 12 Monterey. For customers who plan to upgrade macOS 11 Big Sur endpoints running the Kernel Extension to Monterey, we recommend using a management tool like Workspace ONE, Jamf, or similar MDM solution to deploy the 3.7.1 sensor. Cloud upgrade does not support Kernel Extension mode upgrades from macOS 11 to macOS 12.
As always, to ensure full sensor enablement we recommend that endpoints are preconfigured with System Extension pre-approval via MDM before deployment of the sensor.
-
macOS 12.3, 12.4 support
Due to a compatibility-related change Apple has made in version 12.3 with regards to their internal protocols, all sensor versions prior to 3.6.2 will not support macOS 12.3 or greater.
Systems that upgrade to macOS 12.3 or greater before installing the 3.6.2 sensor or later will incorrectly display the sensor as active from the console; however the sensor will be in a bypass state causing a lapse in endpoint protection.
To maintain endpoint protection, install sensor version 3.6.2 or later before upgrading to macOS 12.3 or greater.
Please see these KB articles for more information:
-
LiveOps and Complete ARM / Apple Silicon Support
This release adds native ARM support for LiveOps/OSQuery engine and removes the 3.6 sensor OSQuery dependency on Rosetta in the ARM environment. Limitation that was previously caveated in 3.6 release notes has been removed. This marks the complete native ARM / Apple Silicon support milestone.
-
Tamper Protection (SysEXT sensor)
The 3.7.1 macOS sensor includes partial tamper protection support with added protection against changes to sensor files and directories and alerting on these tamper protection violations.
Full tamper protections against all methods of tampering with the SysEXT sensor will be available in future sensor releases.
-
Ransomware Prevention (SysEXT sensor)
The 3.7.1 macOS sensor now supports Ransomware Prevention in SysEXT mode, which can be enabled under Blocking and Isolation.
The prevention rule can be enabled for specific reputations (such as “Not Listed” and “Unknown” Applications) and application paths by setting the “Performs ransomware-like behavior” operation to the “Terminate” Action. Corresponding Ransomware exceptions rules can be written using application path rules for the “Performs ransomware-like behavior” operation, in the Permissions section.
For more information on setting a Ransomware Policy please refer to the Carbon Black Cloud user guide section Set a Ransomware Policy Rule.
-
Malware Pre-execution Prevention (SysExt sensor)
This release adds a major enhancement to the Antivirus functionality in the SysEXT sensor mode. MacOS binary and executable script files with a known malware reputation delivered on the endpoint are now blocked on the first attempt to execute and before the executable code image runs. The enhancement is specific to the “Runs or is running” Policy operation for the “Known Malware” Process target:
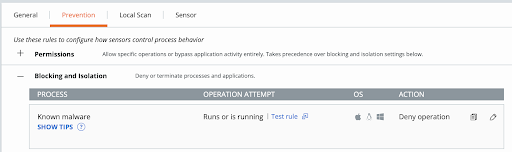
The Policy rule behavior for SysEXT sensor in 3.7.1 and greater is: Known malware process is blocked on the first execution, or terminated post-execution if the process was already running. Prior to 3.7.1, the same policy rule would only result in the post-execution termination.
Note that full support for pre-execution blocking of additional Known Malware file types, specifically loadable code in form of dylib, scripts, installers and documents, will be added in subsequent releases.
Additionally, the 3.7.1 sensor in SysEXT mode now supports the “Runs or is running” operation for the “Unknown” Process target for customers implementing the most restrictive policy.
-
Resolved SysEXT sensor Network Connectivity
Previous issue with Network Connectivity symptoms on macOS11-macOS12 with SysEXT sensor has been addressed by Apple in the macOS 12.4 release. Endpoints running any macOS12.4 - compatible sensor (3.6.2 or newer) can now be upgraded to macOS 12.4 to resolve the issue where the network becomes unresponsive using multiple Network Extensions or a Network Extension with an Ethernet adapter. Please refer to Apple’s macOS Monterey 12.4 release update and our article link regarding this issue for more information.
Please see these articles for more information:
Security Efficacy Improvements
Endpoint Standard / SysEXT
-
DSEN-15839: XProtect: Improved reporting on XProtect (macOS malware scanner) blocks to include the execution path and not the translocated path
-
DSEN-16913: Keylogger Detection: Improved detection of Mac keyloggers leveraging CGEventTap mechanism (detected as MONITOR_USER_INPUT TTP)
Endpoint Standard, Enterprise EDR / SysEXT
-
DSEN-17245: Network Connections: Improved reporting of remote hostnames used for DNS resolutions, especially for connections initiated by web browsers
-
DSEN-14141, EA-2050: Device Quarantine: fix to correctly terminate network connections established before sensor is moved to quarantine state
Resolved Issues
The following issues were fixed in this version of the software.
Endpoint Standard and Enterprise EDR
-
DSEN-16606: RepCLI: Fixed CPU spike caused by race condition when running multiple repcli commands simultaneously
-
DSEN-18119, DSEN-13823, DSEN-13750: Fixed minor repmgr service stability issues
-
DSEN-16254: Unattended Install: now supports installer options to enable proxy configuration during sensor upgrade and downgrade
These options were previously available only to the sensor fresh install.
Endpoint Standard, Enterprise EDR / SysEXT
-
DSEN-16229: Unattended Install: Fixed issue where macOS11+ install with "-d off" didn't install into bypass mode.
-
DSEN-16290: Network Extension control moved from VMware CBCloud.app interface to the RepCLI interface
Please update your internal procedures.
Use 'repcli help networkextension' for more details.
-
DSEN-18190, EA-20677: Fixed an issue that prevented the sensor from exiting Device Quarantine
-
DSEN-16107, EA-19299: Some Mac devices were not assigned to the correct Policy Group based on the specific Group criteria
-
DSEN-17902, DSEN-17914: Sensor Upgrade: Resolved issues where in some cases SysEXT sensor upgrade did not complete, leading to stale previous version SysEXT remaining on the system
This should eliminate the circumstances that may have required post-upgrade SysEXT cleanup procedure.
For older sensors still in such state, please refer to this KB for improved automated SysExt cleanup procedure that no longer requires SIP disablement:
Known Issues
The following issues are known to affect the software. Each lists the sensor version when the issue was first reported. Issues are removed after they are resolved.
-
Extraneous Kernel Extension approval
If a Kernel Extension sensor is installed in macOS Catalina, and an OS upgrade to Big Sur occurs, users might see an extraneous Kernel Extension approval pop-up, despite the Kernel Extension already being approved.
Users can safely re-approve the Kernel Extension or safely ignore the pop-up. Users should re-approve Kernel Extension upon any future sensor upgrades.
-
Apple Silicon chip set
3.6.1.10 was the first GA version supporting the Apple Silicon chipset. Sensor downgrade to 3.5.x versions prior to 3.6.1.10 is therefore not officially supported on Apple Silicon machines. Doing so would bring the sensor to a version that does not officially support Apple Silicon, causing the sensor to run in emulation mode.
Note that downgrade behavior/expectations on Intel machines does not change.
We are aware that some customers are utilizing the 3.5.x versions for emulated support of the sensor on Apple Silicon chip sets.
The recommended downgrade path from Apple Silicon native sensors (any 3.6.x+ sensor) to any Apple Silicon pre-native sensor (any sensor prior to 3.6.x) is via uninstall of the native sensor and installation of the pre-native emulated version
Utilizing standard downgrade behaviors is unsupported and can lead to undefined behavior.
-
Migrating data from Intel to an Apple Silicon machine
Including the sensor as part of migrating data from Intel to an Apple Silicon machine (i.e. Migration Assistant) is not a supported workflow.
The recommended workflow is to uninstall the sensor before migration or exclude the sensor during migration and install it on the target machine.