| VMware Carbon Black Cloud 3.7.3.159| 02 JUN 2023 | Build 3.7.3.159 Check for additions and updates to these release notes. |
What's New
VMware Carbon Black Cloud macOS Sensor 3.7.3.159 release includes features, improvements and bug fixes that are addressed in more detail here.
Important notes:
-
This release supports macOS 11 - 14. Please refer to the macOS support link under resources for more details.
-
Sensor version 3.8.0 and future sensor versions no longer support Kernel Extension approval as well as macOS11 and prior Operating Systems. Customers must use System Extension approval.
Resources:
Release checksums
| 3.7.3.159 DMG SHA256 Checksum |
291bdbd8fb0e3d8c7ea167e03c2034b8c3e61e8b0cf0e20261b73fd7664155a8 |
| 3.7.3.159 PKG SHA256 Checksum |
873ac0c9e40302fdac740679bc8e9faf268a469d8f2b2cf5917d8fdbe4022793 |
- Sensor Tamper Protection: Sensor Services
- Endpoint Standard
- Endpoint Standard and EEDR
- macOS Support
Sensor Tamper Protection: Sensor Services
-
This release enhances Sensor Tamper protections
The enhanced protections secure the sensor services, processes and communication channels against tampering by an external malicious actor or an endpoint user attempting to circumvent the uninstall protections.
Tamper Protection policy is built-in. Tamper attempt blocks are exposed with MODIFY_SENSOR TTP tagging the corresponding events.
Please check the Known Issues section for the current limitation around the Sensor Tamper Protection.
Endpoint Standard
-
Restricting Network Connectivity for Untrusted Applications per Blocking Policy
The 3.7.3 sensor introduces blocking for the “Communicates over the network” policy operation. This policy enables the ability to block a connection attempt (Deny operation) or terminate specified applications (Terminate process) that attempts to communicate over the network, per the application reputation or the application path.
Deny Rule for Application that “Communicates over the Network” 
Related Documentation:
-
Detection and Prevention support for dynamically loaded modules (DYLD files)
This release adds support for scanning, detection and pre-execution prevention of potentially malicious DYLD (dynamically linked library) files.
1. Malicious reputation based DYLD pre-load prevention.DYLD files categorized by reputation as “on company banned list”, “Known malware”, “Suspect”, or “Adware or PUP” are prevented with the standard “Runs or is running” operation policy rule:
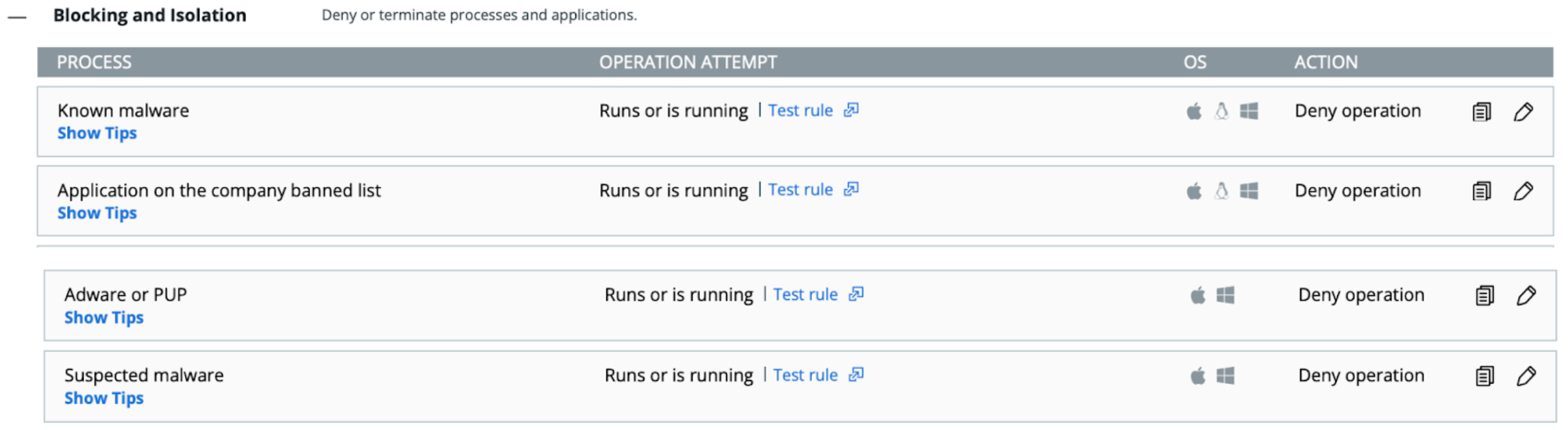
2. Behavioral DYLD code injection prevention. DYLD files with the “Unknown” or “Not listed” reputation, that are loaded into a running process using one of suspicious code injection techniques used to override the standard macOS DYLD libraries, are prevented with “Injects code” operation policy rule:
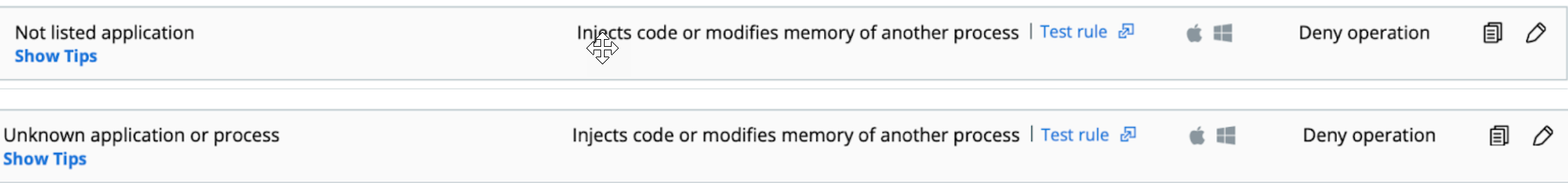
-
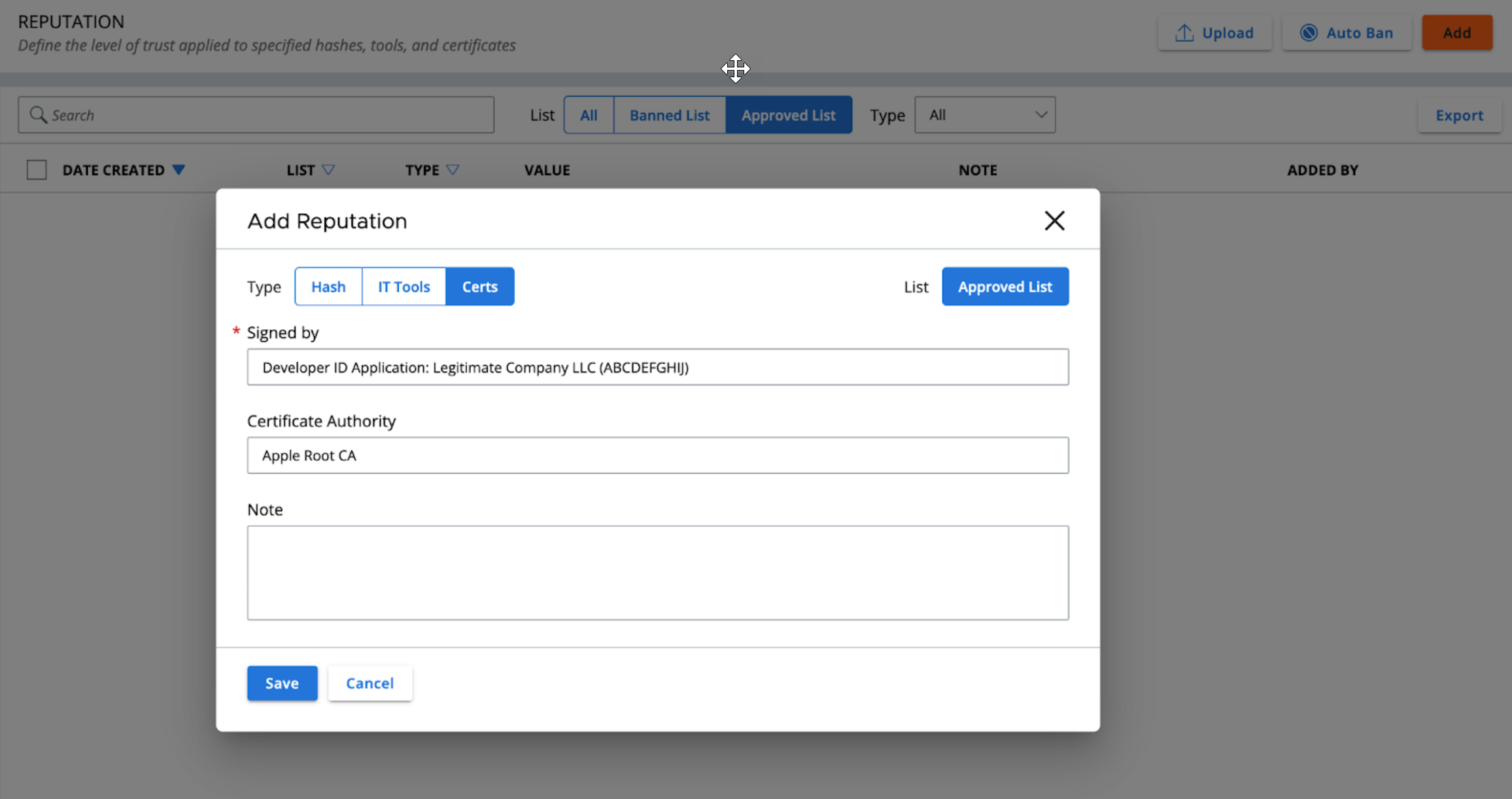
AllowList: Certificate
This release enables the Certificate Allowlisting feature for signed files and processes running signed code. Certificate Allowlisting can be configured on Reputation page by Signing Authority. Cert AllowList in this release does not include trust propagation to files bundled within signed PKG installer packages (planned for future release).
The common use-cases for this feature are macOS and 3rd party software updates for signed and sanctioned software in the customer environment. When combined with advanced prevention policies, the feature helps improve interoperability and lower false positives.
-
AllowList: IT Tools
The release fully enables IT Tools Allow list feature. IT Tools can be configured on Reputation page by path of IT tool:
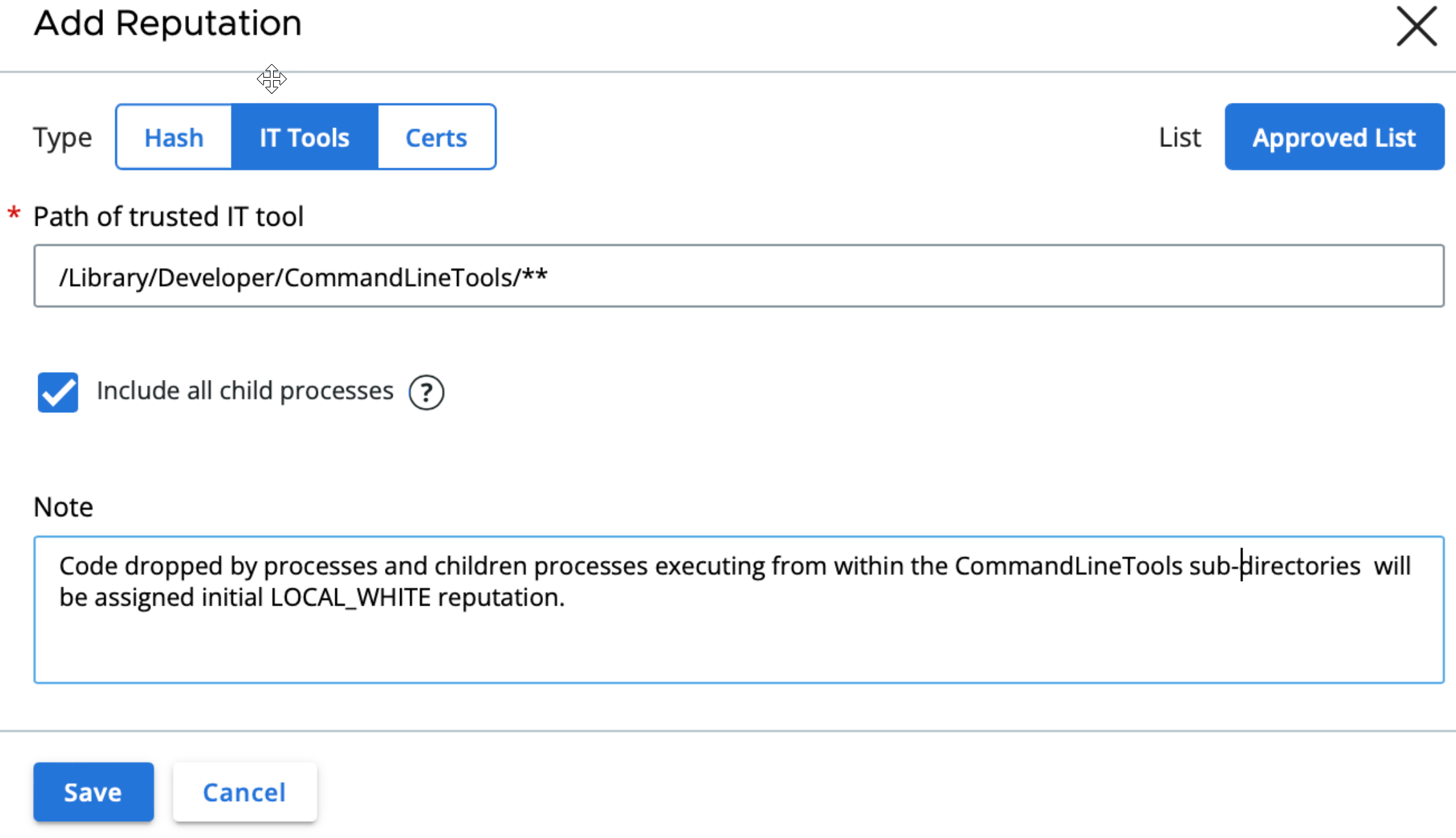
Common use-case for IT Tools on Mac is to improve performance and reduce false positives for software mass deploy tools and developer tools common in the user environments that act as frequent code droppers.
-
Ransomware Prevention: Efficacy Enhancements
The release improves the efficacy of behavioral Ransomware Prevention to better prevent against the following attacks:
-
Leveraging operating system binaries.
-
Persistant ransomware.
-
Endpoint Standard and EEDR
-
Enhanced Cross-Process Behavior Reporting and Detections
The release enhances cross-process reporting and detections for the following cross-process behaviors:
Cross-Process Behavior
Product
Open Process Handle
EEDR
Potential Memory Scraping
TTP: RAM_SCRAPING
Endpoint Standard
Privilege Escalation
TTP: PRIVILEGE_ESCALATE
Endpoint Standard
Process Enumeration
TTP: ENUMERATE_PROCESSES
Endpoint Standard
-
Enhanced Sensor Status Reporting
The release provides additional visibility into effective Sensor Status.
-
Sensor Bypass reporting due to SysEXT initialization error: In the event of an unexpected internal SysEXT initialization error, such as when caused by an unexpected and unhandled MDM configuration issue, the sensor automatically enters internal bypass state, followed by subsequent re-initialization retries. This state can be queried as follows:
-
repcli status command: General Info -> System Extension: and Sensor State: State: entries.
-
Carbon Black Cloud Console:
-
Inventory->Endpoints page, Last Check-in column: Error (extension error).
-
Device->Protection Mode: DRIVER_INIT_ERROR.
-
-
-
Network Extension Status. This additional sensor state info can be useful when:
-
Troubleshooting the effective MDM policy.
-
Identifying and re-configuring devices with previously disabled Network Extension.
-
The Network Extension status can be queried as follows:
-
repcli status command: General Info -> System Extension -> Network Extension.
-
CBC Console: Device->Protection Mode: NETWORK_DRIVER_LOAD_NOT_GRANTED and NETWORK_DRIVER_DISABLED.
-
-
Related KB articles:
-
macOS Support
-
Sensor Version Support
Sensor versions 3.7.2 and later are “macOS 14 - ready” and will be enabled for macOS 14 by default. These sensor versions will be announced as officially “macOS 14 supported” if passing the macOS 14 Beta and GM qualification process, unless compatibility issues are identified during the process.
Sensor versions 3.7.3 supports macOS 13 Ventura.
For customers who plan to upgrade macOS 11 Big Sur endpoints running the Kernel Extension to macOS Ventura, we recommend using a management tool like Workspace ONE, Jamf, or similar MDM solution to deploy the 3.7.3 sensor. Cloud upgrade does not support Kernel Extension mode.
to ensure full sensor enablement, preconfigure endpoints with System Extension pre-approval through MDM before deployment of the sensor.
Supported operating modes
Supported Operating System
Supported Modes and Archs
macOS 11 (Big Sur)
System Extension (Intel, Apple Silicon)
macOS 12 (Monterey)
System Extension (Intel, Apple Silicon)
macOS 13 (Ventura)
System Extension (Intel, Apple Silicon)
macOS 14 - ready *
System Extension (Intel, Apple Silicon)
* Official support will be announced after macOS 14 GM, not recommended for production deployment until then. For more information, see the UEX forum.
.
Resolved Issues
Endpoint Standard
-
DSEN-21582: Performance improvements for applications with bypass rules
-
DSEN-24461: Fixed OS compatibility issue between the unattended installer and MacOS 13.3.1(a)
Please refer to this KB article for the workaround and updated script announcement.
EEDR
-
DSEN-21872: Events throttling and sending improvements during periods of low endpoint activity
Associated with: EA-22114.
Endpoint Standard and EEDR
-
DSEN-22646: Fixed sensor cloud upgrade latency after the upgrade is triggered from the CBC console
The change will be visible when cloud upgrade is triggered from 3.7.3 to future sensor versions.
-
DSEN-22672: Fixed reported network event FQDN field sometimes containing extraneous period character
Associated with: EA-22365.
-
DSEN-21399: Improved service operability in environments with Proxy server
-
DSEN-21400: Improved detection and reporting of the endpoint IP address for endpoints with virtual network interfaces
Associated with: EA-22012.
-
DSEN-23396: General SysEXT (se_agent) performance improvements
-
DSEN-24470: Unattended installer option is now supported on sensor upgrade and reinstall
Unattended installer option --disable-sysext-network-extension is now supported on sensor upgrade and reinstall. This is an alternative mechanism to toggle Network Extension on and off, in addition to sensor fresh install and RepCLI.
Please refer to the following KBs on Network Extension troubleshooting:
-
Disable the Carbon Black Cloud network extension: How to disable and re-enable CBC network extension on MacOS
-
-
DSEN-21103: Thirdparty library updates
LiveOps
-
DSEN-21103: Updated OSQuery engine to 5.7.0
Known Issues
The following issues are known to affect the software. Each lists the sensor version when the issue was first reported. Issues are removed after they are resolved.
-
Current Apple macOS limitation enables end user to drag and uninstall SysEXT, circumventing the sensor Uninstall Protection
Carbon Black is in contact with Apple Eng. to resolve the macOS limitation.
-
Device Quarantine limitation with VPN per-app tunnel
Carbon Black is in contact with Apple Eng. to resolve the universal macOS limitation.
Please refer to this KB article for a workaround.
-
Kernel Extension approval pop-up
If a Kernel Extension sensor is installed in macOS Catalina, and an OS upgrade to Big Sur occurs, users might see an extraneous Kernel Extension approval pop-up, despite the Kernel Extension already being approved.
Users can safely re-approve the Kernel Extension or safely ignore the pop-up. Re-approve Kernel Extension upon any future sensor upgrades.
-
Unsupported workflow for migrating data from Intel to an Apple Silicon machine
Including the sensor as part of migrating data from Intel to an Apple Silicon machine (i.e. Migration Assistant) is not a supported workflow.
The recommended workflow is to uninstall the sensor before migration or exclude the sensor during migration and install it on the target machine.
-
Running command line uninstall utility from within a Carbon Black directory causes crash after successfully uninstalling the sensor
Run the uninstall command from a user-owned directory.