You can create a custom rule for container images that is based on built-in rules.
Procedure
- On the left navigation pane, click Enforce > K8s Policies.
- Click the Rules tab.
- Click Add Rule.
- Define the rule.
- Enter a unique custom rule name and a description.
- Select Container image criteria as the rule criteria.
- Click Next.
- Configure the rule. Options are:
Image Criteria Vulnerability Severity or Registry Domains Critical vulnerabilities Note: The vulnerabilities with Critical severity are part of the default Critical vulnerabilities built-in rule. If you select Critical (9.0 - 10.0), you duplicate the existing built-in rule.- Critical (9.0 - 10.0)
- High and above (7.0 - 10.0)
- Medium and above (4.0 - 10.0)
- Low and above (0.1 - 10.0)
Vulnerabilities with fixes - Critical (9.0 - 10.0)
- High and above (7.0 - 10.0)
- Medium and above (4.0 - 10.0)
- Low and above (0.1 - 10.0)
Allowed registries Specify registries you want to allow as source. For example, docker.io. - Click Next.
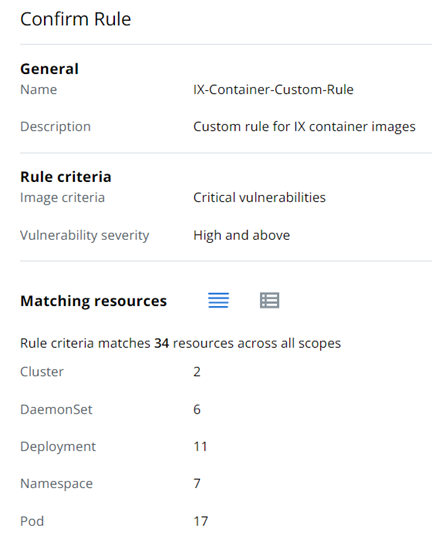
- On the Confirm Rule page, review the summary of the rule criteria and the matching Kubernetes resources and click Save.