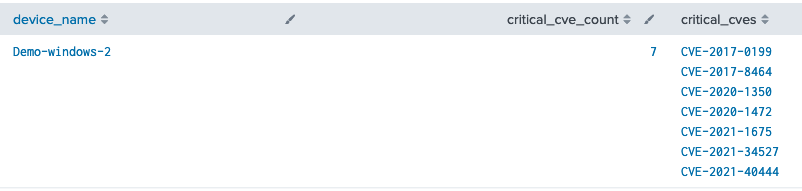
A good starting point for vulnerability assessment is to identify any endpoint with critical vulnerabilities. With that information, you can move the impacted endpoints to a more restrictive policy, or just keep a closer eye on any alert from that endpoint.
eventtype="vmware_cbc_vulnerability_os_list"severity="CRITICAL"
| rename affected_assets{} as device_name
| mvexpand device_name
| stats
dc(cve) as critical_cve_count,
values(cve) as critical_cves
by device_name
| sort -critical_cve_count