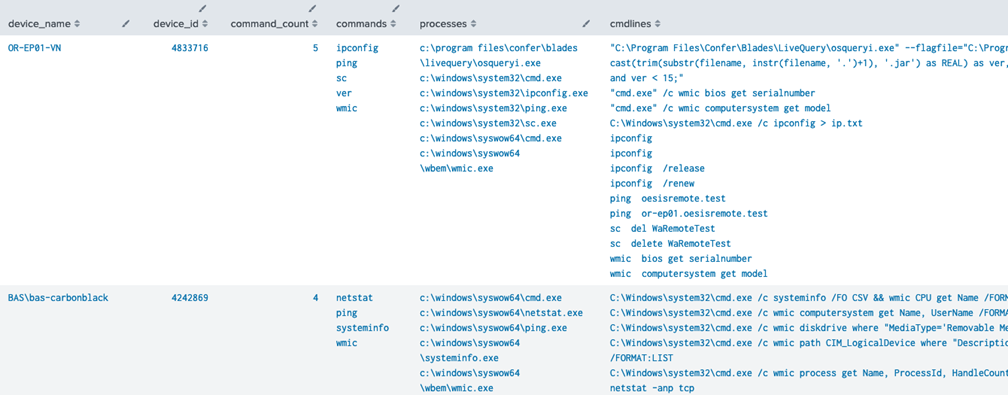
When multiple normal commands are observed on the same endpoint in a short time, it can require investigation.
Required Product: Carbon Black Cloud Enterprise EDR
Required Data: Endpoint Events (Data Forwarder)
You can accomplish an investigation by forwarding process start endpoint events (custom query filter type:endpoint.event.procstart) to Splunk SIEM.
This query uses a long regex to pull these commands when they are a standalone word. Consider additional tuning such as allowing adjacent characters like . and /, and allow-listing certain known good processes that invoke some of these commands and might contribute to noise.
See also Windows Commands Abused by Attackers.
Endpoints with the Most Commonly Abused Commands
| `vmware_tstats` count from datamodel=VMWare_CBC where nodename=All_CBC.Endpoint by All_CBC.device_name, All_CBC.device_id, All_CBC.org_key, All_CBC.Endpoint.process_cmdline, All_CBC.process_executable | rename All_CBC.* as * | rename Endpoint.process_cmdline as cmdline | rex field=cmdline "(^|\s)(?<command>tasklist|ver|ipconfig|systeminfo|net\stime|netstat|whoami|net\sstart|qprocess|query|dir|net\sview|ping|net\suse|type|net\suser|net\slocalgroup|net\sgroup|net\sconfig|net\sshare|at|reg|wmic|netsh\sadvfirewall|sc|wusa)($|\s)" | where not isnull(command) | stats dc(command) as command_count, values(command) as commands, values(process_executable) as processes, values(cmdline) as cmdlines by device_name, device_id | sort -command_count